raptor: Web-based Source Code Vulnerability Scanner
Raptor is a web-based (web-service + UI) github centric source-vulnerability scanner i.e. it scans a repository with just the github repo url. You can set up webhooks to ensure automated scans every-time you commit or merge a pull request. The scan is done asynchronously and the results are available only to the user who initiated the scan.
Some of the features of the Raptor:
- Plug-in architecture (plug and play external tools and generate unified reports)
- Web-service can be leveraged for custom automation (without the need of the UI)
- Easy to create/edit/delete signatures for new vulnerabilities and/or programming languages.
This tool is an attempt to help the community and start-up companies to emphasize on secure-coding. This tool may or may not match the features/quality of commercial alternatives, nothing is guaranteed and you have been warned. This tool is targeted to be used by security code-reviewers and/or developers with secure-coding experience to find vulnerability entry-points during code-audits or peer reviews. Please DO NOT trust the tool’s output blindly. This is best-used if you plug Raptor into your CI/CD pipeline.
Tech
Integrated Plugins:
Note: Most of the following tools/modules/libs have been modified heavily to be able to integrate well into the framework.
- ⚡️ Mozilla ScanJS – for JavaScript (Client-Side, Node.JS etc. and upcoming support for Chrome Extensions & Firefox Plugins)
- ⚡️ Brakeman – for Ruby On Rails
- ⚡️ RIPS – for PHP
- ⚡️ Manitree – for AndroidManifest.xml insecurities
Available Rulepacks:
- ⚡️ ActionScript – supports Flash/Flex (ActionScript 2.0 & 3.0) source/sinks
- ⚡️ FindSecurityBugs (rules Only) – for Java (J2EE, JSP, Android, Scala, Groovy etc.)
- ⚡️ gitrob – for Sensitive Date Exposure (files containing credentials, configuration, backup, private settings etc.)
Installation
$ wget https://github.com/dpnishant/raptor/archive/master.zip -O raptor.zip
$ unzip raptor.zip
$ cd raptor-master
$ sudo sh install.sh
Usage
Scanner
cd raptor-master
sudo sh start.sh #starts the backend web-service
Now point your browser to Raptor Home (http://localhost/raptor/)
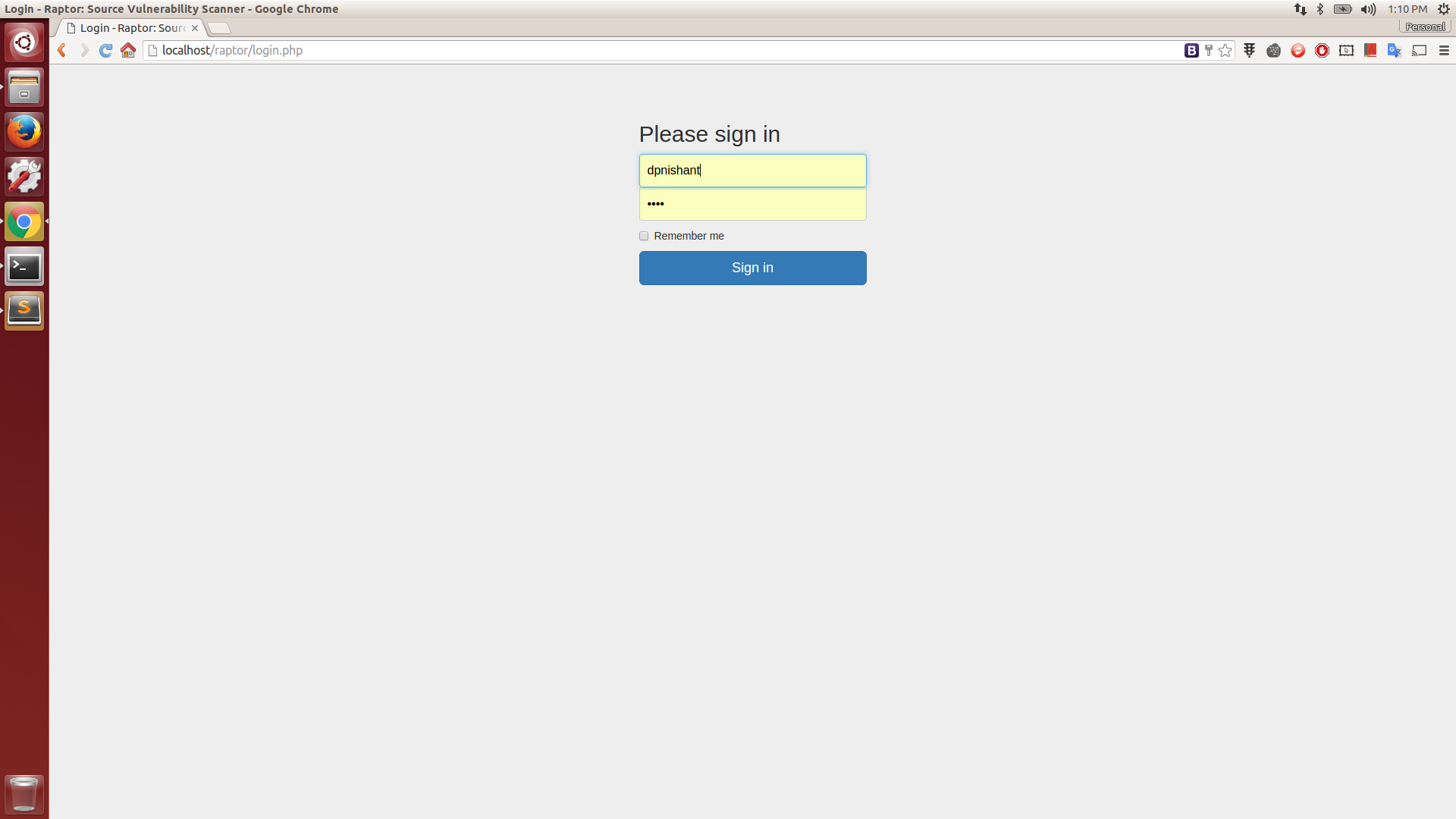
Login
Login with the username as registered on the corresponding github server you are connected to and any password (but remember the username to view scan history)
Rules Editor
You can use the bundled light-weight, GUI client-side rules editor for adding any new/custom rule(s) for your specific requirements(s) or any other plain-text editor as the rulepack files are just simple JSON structures. Use your browser to open rules located in ‘backend/rules’. When you are done, save your new/modified rules file in same directory i.e. ‘backend/rules’. All you need to do now is a minor edit, here: Init Script. Append your new rulepack filename to this array without the ‘.rulepack’ extension and restart the backend server. You are all set! 👍
You can access it here: Rules Editor (http://localhost/raptor/editrules.php)
Login
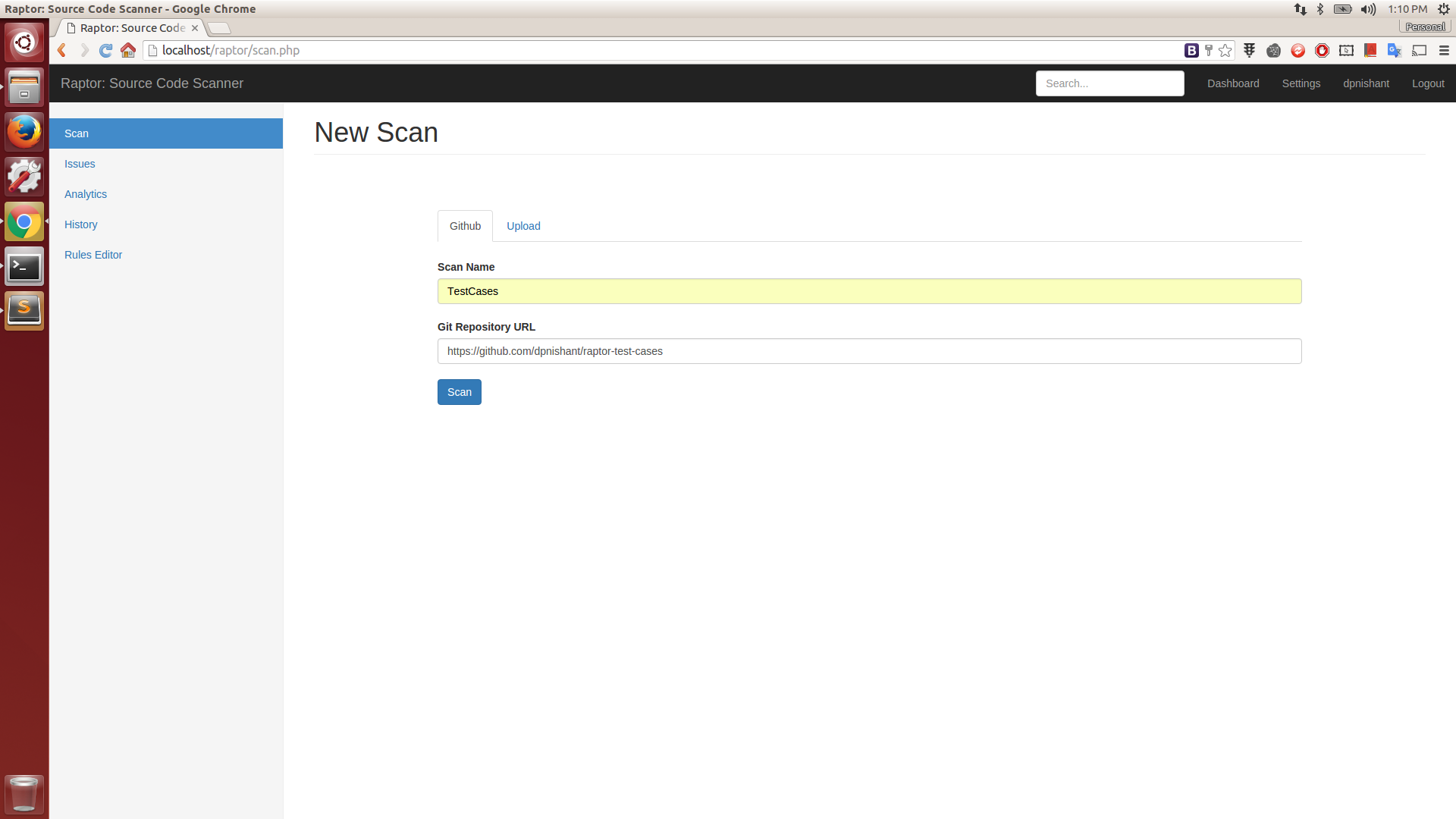
Github Scan
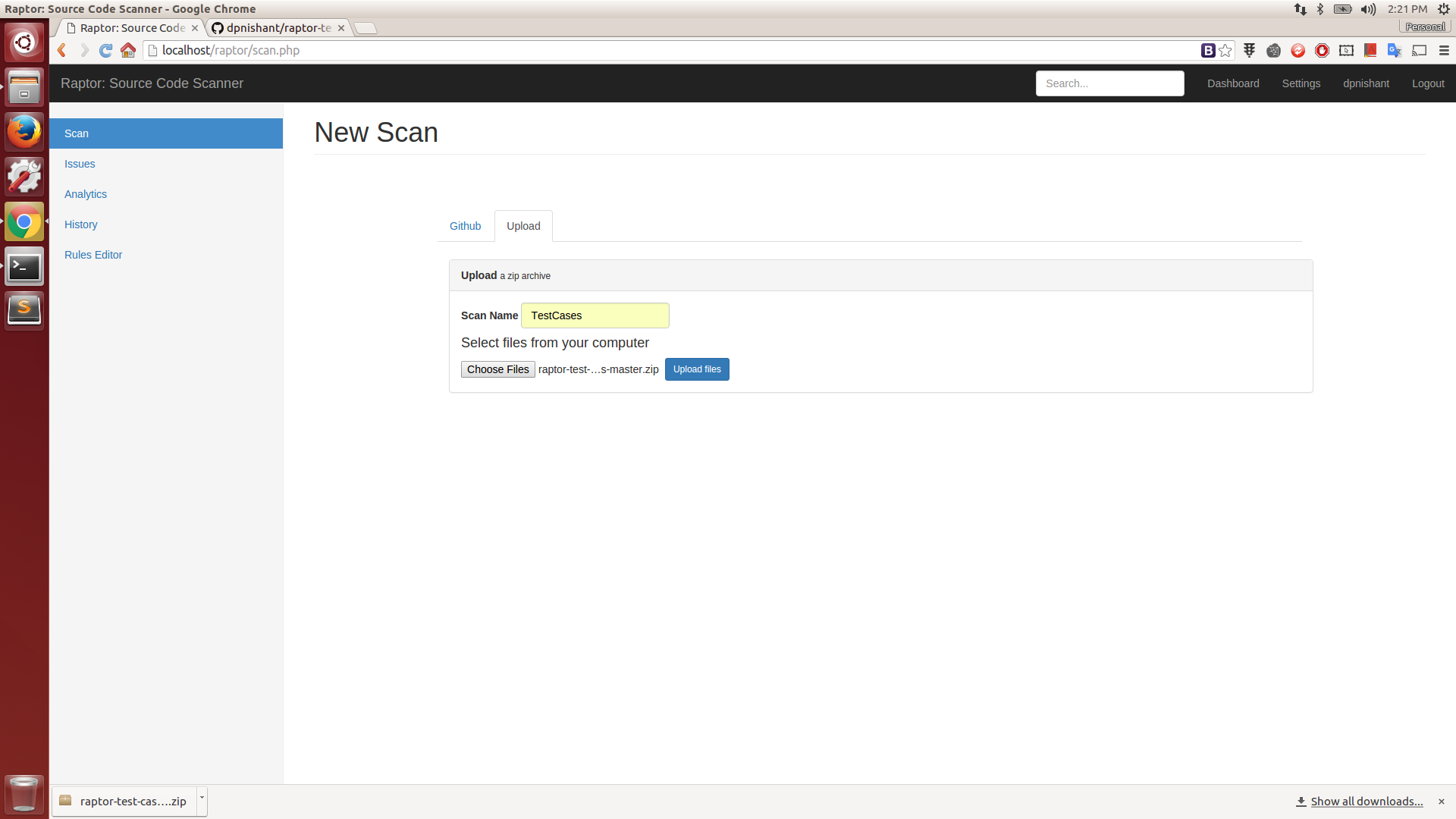
Zip Scan
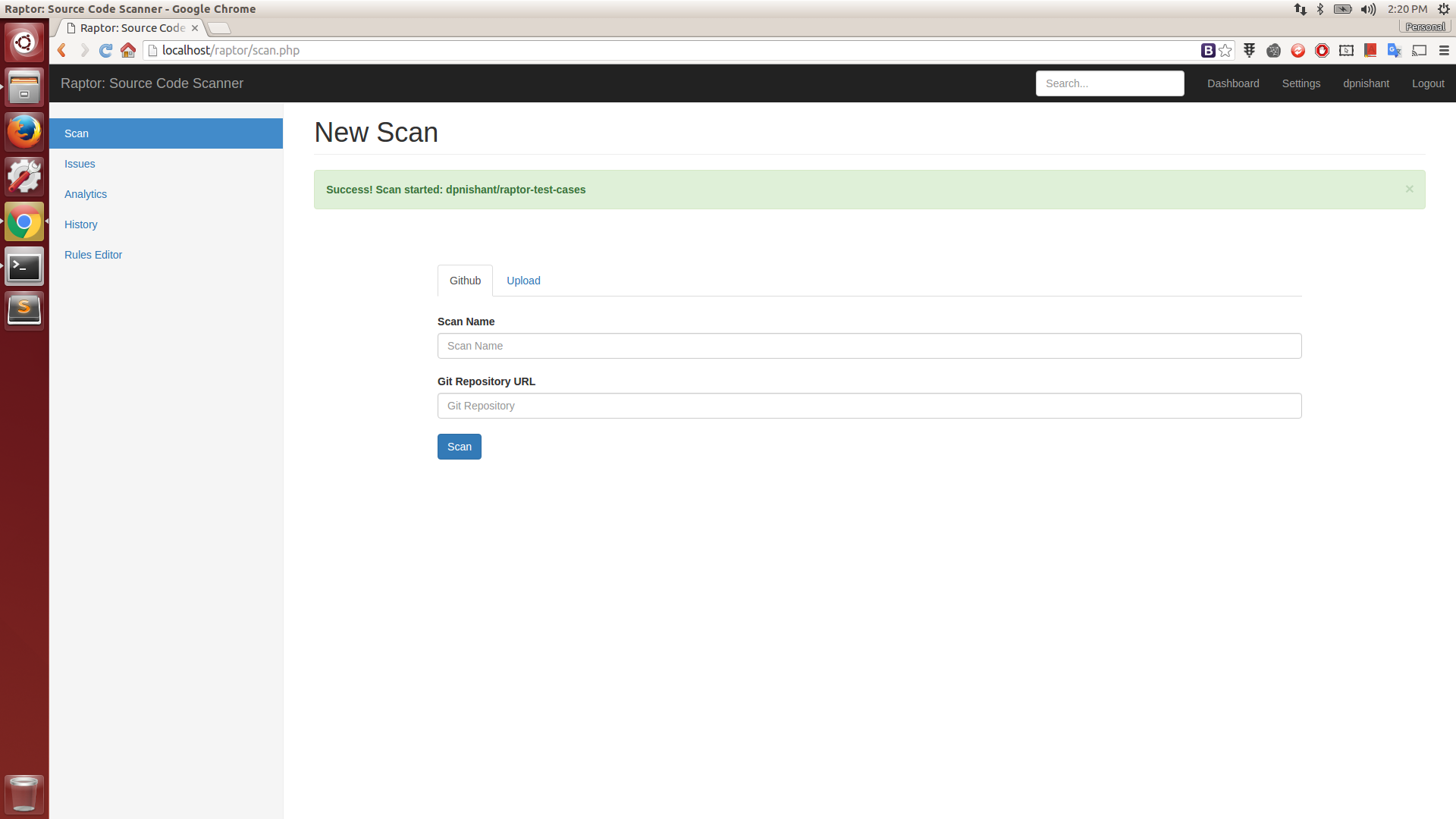
Scan Started
Scan in progress
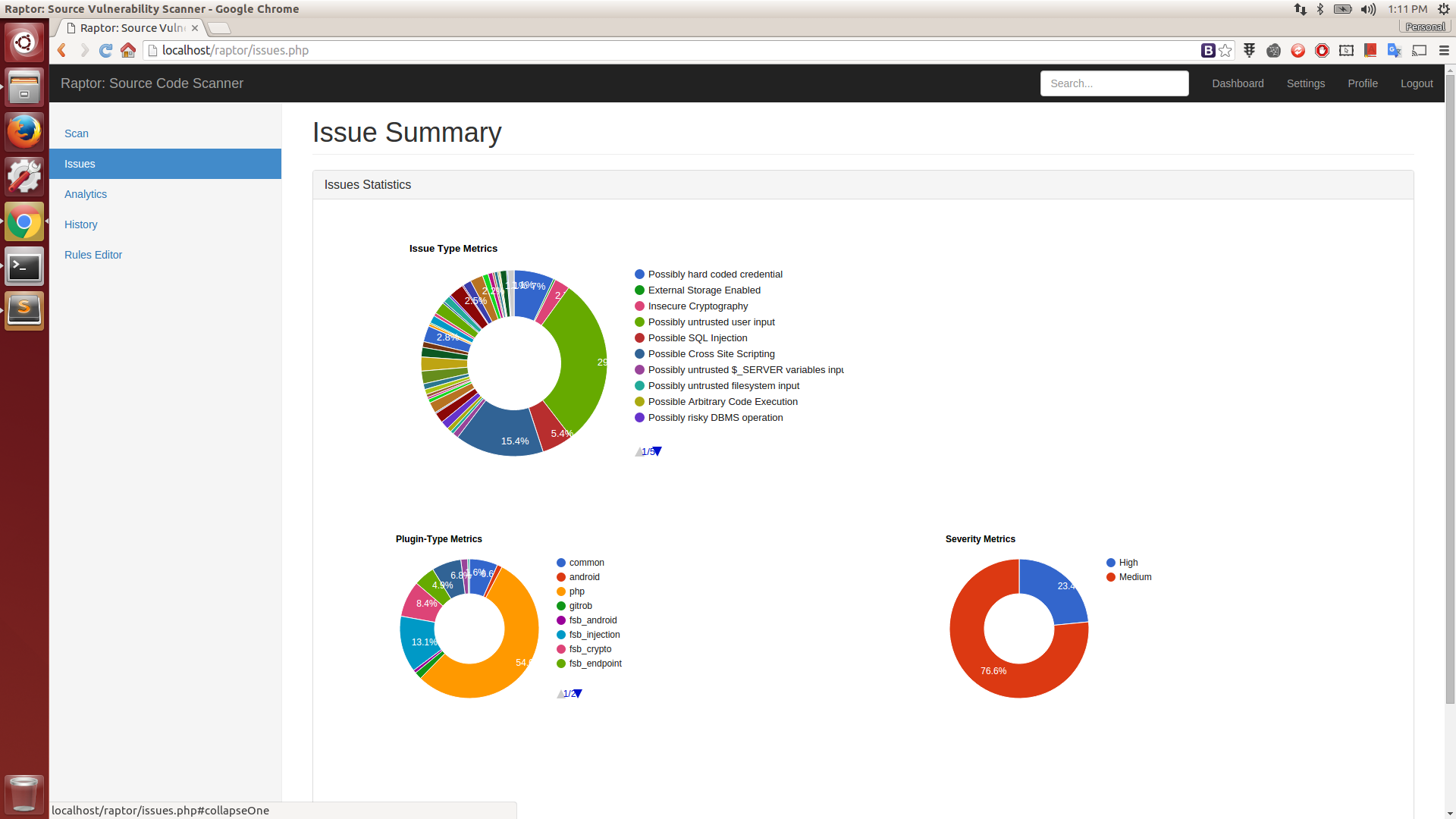
Report Statistics
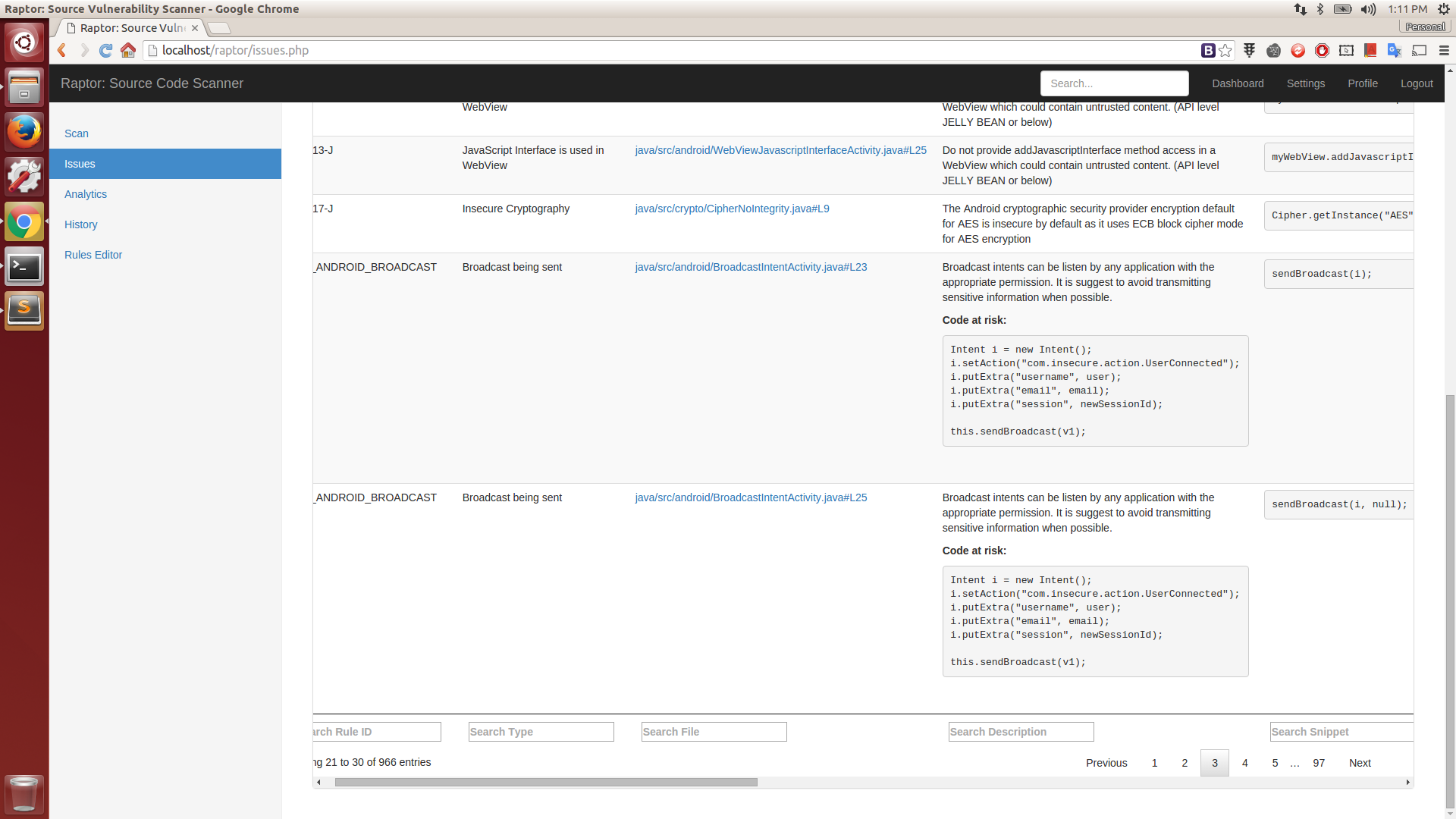
Issue Details
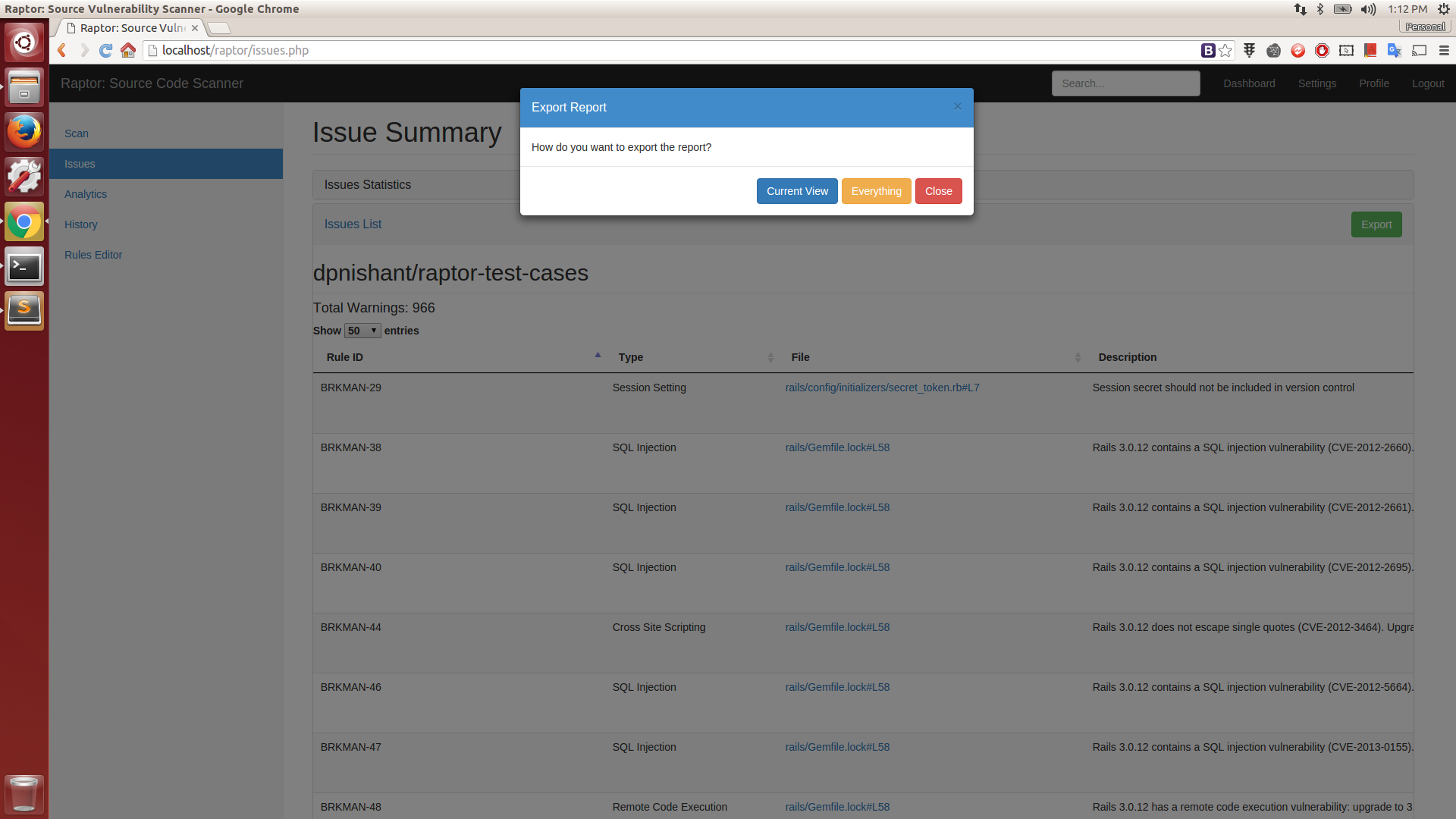
Export Report
Scan History
Rules Editor
Server Error
Copyright (C) 2015 dpnishant
Source: https://github.com/dpnishant/