Image: TRT
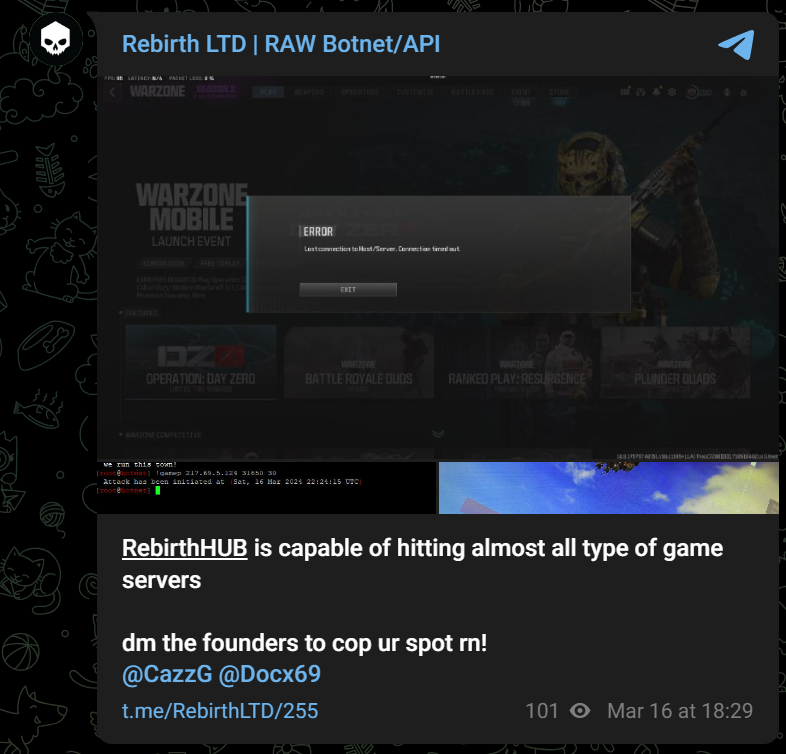
The Sysdig Threat Research Team (TRT) has exposed the alarming activities of the Rebirth botnet, a Mirai-based DDoS-as-a-Service (DDoSaaS) platform that primarily targets the video gaming community. Based on the notorious Mirai malware family, Rebirth’s operators market their services through Telegram and an online store, rebirthltd.mysellix[.]io. While initially focused on disrupting video game streamers and engaging in “DDoS trolling,” the botnet’s reach extends beyond gaming, potentially impacting organizations across various sectors.

Rebirth botnet operates as a sophisticated cybercrime enterprise, offering a range of DDoS attack services through a web-based storefront and advertising its capabilities on Telegram. The botnet boasts a wide array of attack types, including TCP and UDP floods, reflection attacks, and more, making it a potent weapon for disrupting online services and extorting victims. These services are available through various subscription packages on a web-based storefront. Prices start at $15 for basic access to the botnet’s executables, with more expensive plans offering API access, C2 server availability, and enhanced features like higher attack rates.
The botnet’s creators, identified as “CazzG” and “Docx69,” appear to have a history of cybercrime activities, including the operation of other botnets and participation in hacking forums. They actively promote Rebirth’s services on social media platforms like TikTok and YouTube, demonstrating a brazen disregard for law enforcement.
While Rebirth’s primary targets seem to be video game streamers, its capabilities extend beyond gaming. The botnet’s operators claim it can “hit almost all types of game servers,” raising concerns about potential attacks against other online services, including critical infrastructure and financial institutions.
Rebirth uses multiple methods to evade detection and maintain persistence:
- Anti-Debugging Techniques: Utilizes prctl system calls to mask processes, making them appear as /bin/bash.
- Dynamic Analysis: Reads /proc/net/tcp to scan for vulnerable devices, sets up network listeners on specific ports, and uses socket options to manipulate network connections.
- Infection Vectors: Distributes malicious ELF files through bash scripts that download and execute payloads. Scripts attempt to navigate common directories, download multiple files, and execute them, leveraging vulnerabilities like CVE-2023-25717.
The rise of DDoS attacks in the gaming community is a growing concern, with streamers often being targeted for financial gain or simply to disrupt gameplay. The ease with which individuals can purchase DDoS services from platforms like Rebirth has amplified this threat, making it accessible to anyone with malicious intent.