Recon: perform a full recon on a target with the main tools to search for vulnerabilities
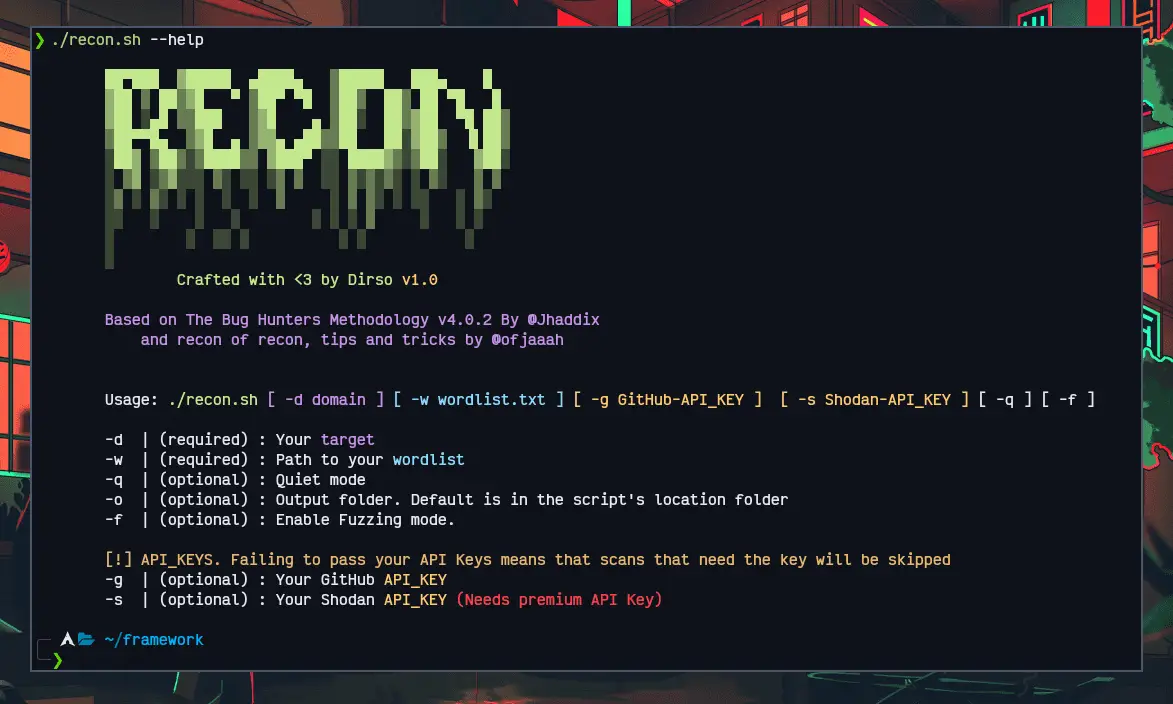
Recon
The step of recognizing a target in both Bug Bounties and Pentest can be very time-consuming. Thinking about it, I decided to create my own recognition script with all the tools I use most in this step. All construction of this framework is based on the methodologies of @ofjaaah and @Jhaddix. These people were my biggest inspirations to start my career in Information Security and I recommend that you take a look at their content, you will learn a lot!
Feature
ASN Enumeration
Subdomain Enumeration
- Assetfinder
- Subfinder
- Amass
- Findomain
- Sublist3r
- Knock
- SubDomainizer
- GitHub Sudomains
- RapidDNS
- Riddler
- SecurityTrails
Alive Domains
WAF Detect
Domain organization
- Regular expressions
Subdomain Takeover
DNS Lookup
Discovering IPs
DNS Enumeration and Zone Transfer
Favicon Analysis
Directory Fuzzing
Google Hacking
- Some Dorks that I consider important
- CredStuff-Auxiliary
- Googler
GitHub Dorks
Credential Stuffing
- CredStuff-Auxiliary
Screenshots
Port Scan
Link Discovery
Endpoints Enumeration and Finding JS files
Vulnerabilities
- Nuclei ➔ I used all the default templates
403 Forbidden Bypass
XSS
LFI
RCE
- My GrepVuln function
Open Redirect
- My GrepVuln function
SQLi
Installation
git clone https://github.com/dirsoooo/Recon.git
cd Recon/
chmod +x recon.sh
chmod +x installation.sh
./installation.sh
Use
Tutorial
Copyright (c) 2021 Dirso





