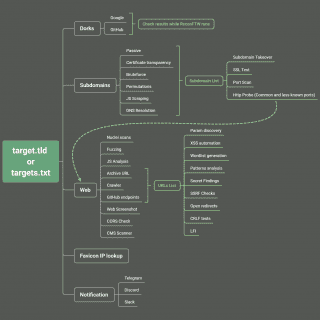
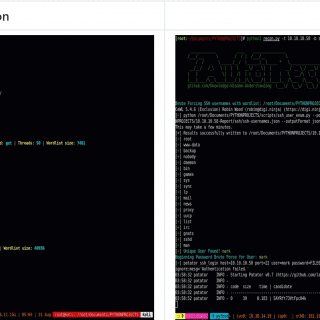
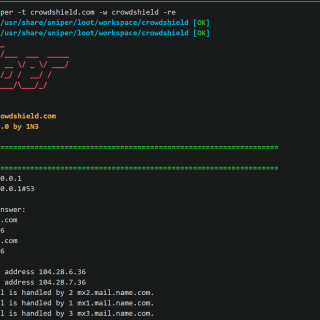
Recon: perform a full recon on a target with the main tools to search for vulnerabilities
Recon The step of recognizing a target in both Bug Bounties and Pentest can be very time-consuming. Thinking about it, I decided to create my own recognition script with all the tools I use...