[Reconnaissance Phase]: Passive information gathering
Prior to an attack, the penetration tester should know as much as possible about the target environment and the characteristics of the system. The more targeted information the penetration tester finds, the better the chances of identifying the easiest and fastest way to succeed. Black-box testing requires more reconnaissance than white-box testing because testers do not get too much data. Scouting services may include Internet footprints for investigating targets, monitoring resources, monitoring personnel, processes, etc., scanning network information (such as IP addresses and system types), and social engineering public services such as helpdesks.
Reconnaissance is the first step in penetration testing, whether the penetration tester is known to confirm the target system, or to find known intelligence. When reconnaissance, the target environment must be defined according to the work area. Once the target is identified, a survey is performed to gather information about the target, such as which ports are used for communication, where the target is hosted, what services it provides to the customer, and so on. This data can be used to develop a plan to see what the best way to get the desired results. The results of the reconnaissance process should include a list of all target assets, what applications are associated with the asset, services to be used, and possible asset owners.
Kali Linux provides a category labeled “Information Gathering”, which is a reconnaissance resource. Tools include tools for investigating networks, data centers, wireless networks, and host systems. The following is a checklist of reconnaissance goals: Acknowledging the goals Defining the use of applications and services Acknowledging the type of system, confirming the available ports, confirming the running services, social engineering information, document discovery.
Passive information gathering
Passive information collection refers to the information available through open channels, does not directly interact with the target system, and tries to avoid the detection of all traces of information. The information collected by passive detection technology can be roughly divided into two categories, namely configuration information and status information.
Passive detection can be collected the info below
| Information | Technique |
| The IP address or address segment
|
Whether the probe is alive |
| MAC address
|
Internal sniffing ARP, DHCP |
| Domain name information and hostname | External sniffing DNS, internal sniffing NetBIOS, ARP, DHCP |
| Operating system and version | Fingerprint information |
| Running application | Fingerprint information |
| user name and password | Fingerprint information |
| Device type (server, client) | Port and protocol usage, ICMP |
| Running service | Use of ports and protocols |
| Equipment operating status | Activity level and ICMP |
| Application status | The level of external activity of the device on the application port |
| Link running status | Activity level and ICMP |
| Link utilization | Activity level |
| Device logical location | TTL-based distance hops |
| Email address, company address, company organization structure, contact telephone/fax number, name/job of staff | Social engineering |
| Document image data | Social engineering |
| Public business information | Social engineering |
Domain name system (DNS)
The Domain Name System (DNS) is a service of the Internet. It acts as a distributed database that maps domain names and IP addresses to each other, making it easier for people to access the Internet. DNS uses TCP and UDP port 53. Currently, the limit for the length of each domain name is 63 characters, and the total length of the domain name cannot exceed 253 characters.
DNS and FQND
FQDN: (Fully Qualified Domain Name) Fully qualified domain name/full name domain name refers to the hostname plus the full path. All domain members in the sequence are listed in the full path. The full domain name can logically and accurately indicate where the host is. It can also be said that the full domain name is a complete representation of the hostname. (Example: DNS: google.com; FQND: www.google.com)
There are two ways to map hostnames to IP addresses:
1) Static mapping, each device is configured with a mapping from host to IP address, each device independently maintains its own mapping table, and is only used by the device;
2) Dynamic mapping, establish a set of domain name resolution system (DNS), configure host-to-IP address mapping only on a dedicated DNS server. Devices that need to use hostname communication on the network must first query the DNS server for the host. IP address.
Domain structure
Generally, the general structure of an Internet host domain name is a hostname, third-level domain name, second-level domain name, top-level domain name. The top-level domain name of the Internet is registered and managed by the Internet Network Association domain name registration query committee responsible for network address allocation. It also assigns a unique IP address to each host on the Internet. There are three major network information centers in the world: Inter-NIC in the United States, responsible for the United States and other regions; RIPE-NIC in the Netherlands, responsible for Europe; APNIC in Japan, responsible for the Asia-Pacific region.
Nslookup
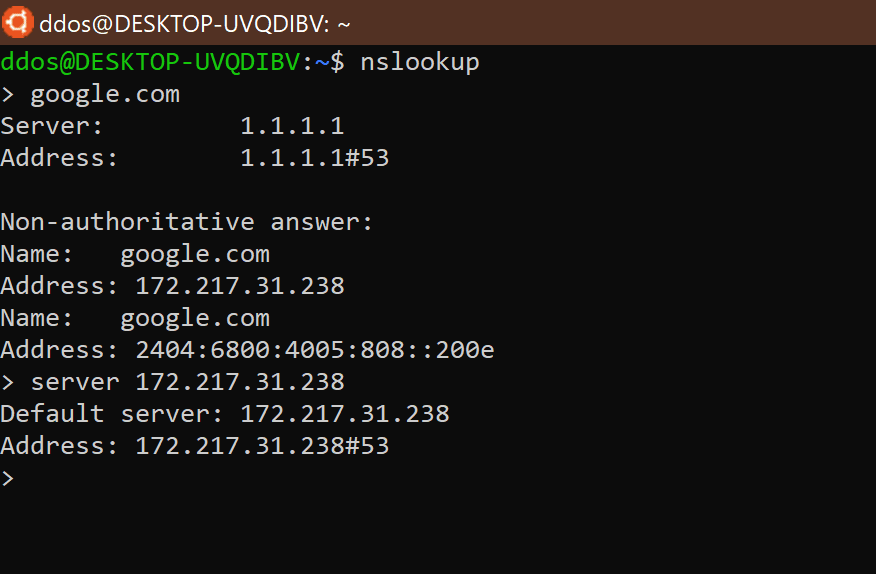
Nslookup is a command-line tool that monitors whether DNS servers on the network can properly resolve domain names. Used to query the DNS records, check whether the domain name resolution is normal, and use it to diagnose network problems when the network is faulty.
Example: