ReconUI: base-web reconnaissance tool
ReconUI

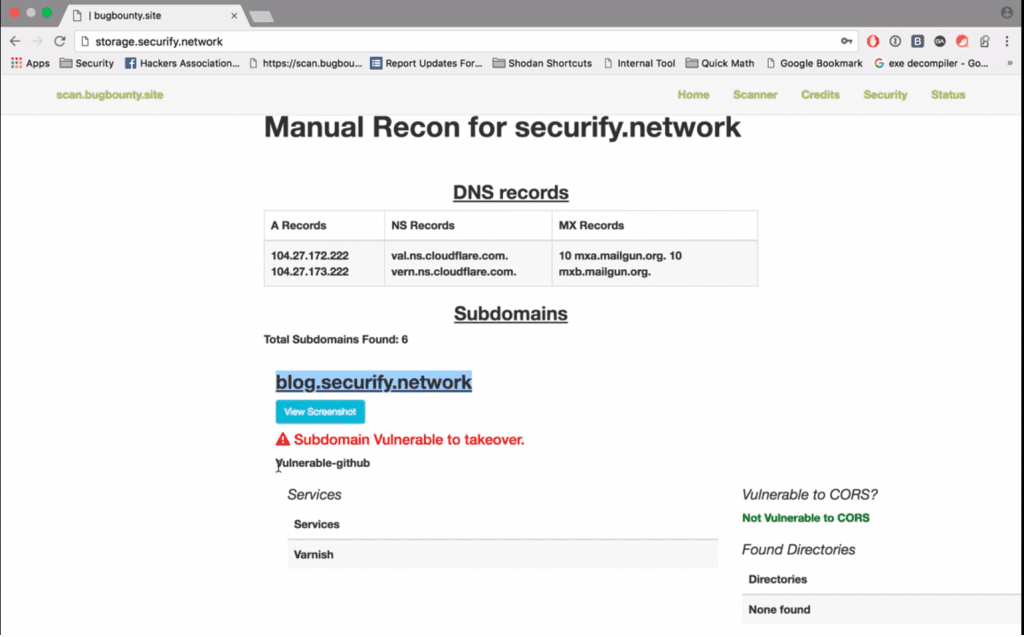
Current Features
- Subdomain bruteforcing
- Directory bruteforce for each subdomain.
- Basic CORS vulnerability check.
- Auto subdomain takeover for AWS S3 Bucket and Heroku
- Censys IPv4 lookups.
- Public XSS search from open bug bounty.
- Screenshot grab of each subdomain.
Install
Automated Setups Before running this check the custom/required setup section below
- To setup basically everything, simply run installer.sh as sudo.
Custom/Required Setup
There are some setups that you need to do manually.
Heroku
- Install and setup Heroku CLI: https://devcenter.heroku.com/articles/heroku-cli
- Make sure you have a valid Heroku account when you set this up. In Heroku to add custom domains, you need a credit/debit card in your account.
- Create an app that will be used for takeovers. Heroku allows adding multiple custom domains so one app is sufficed. Once you add the app, make sure it has some code.
- The easiest way to deploy the app is through Dropbox. Simply link your Dropbox, upload your code and make sure your Heroku app has the build back ready. For PHP, simply create an index.php (or any php file name) and also a composer.json file (this can be empty like this {}). Then put that in Dropbox and added a PHP build back and deploy it.
AWS
- Make sure you have a valid AWS account. Once that is there, use AWS CLI to configure your account.
- To configure simply do aws configure and paste in your keys as requested.
URLScan.io API
For the screenshot feature, instead of using custom code and manually taking a picture, the tool will send an external request to generate a private report in URLScan. To do so you need an API key. For that, you will have to email the URLScan.io personnel.
Censys Make sure you signup on Censys to get the API Key Id and Secret.
git clone https://github.com/rojan-rijal/ReconUI.git
cd ReconUI
./installer.sh
Use
Source: https://github.com/rojan-rijal/





