
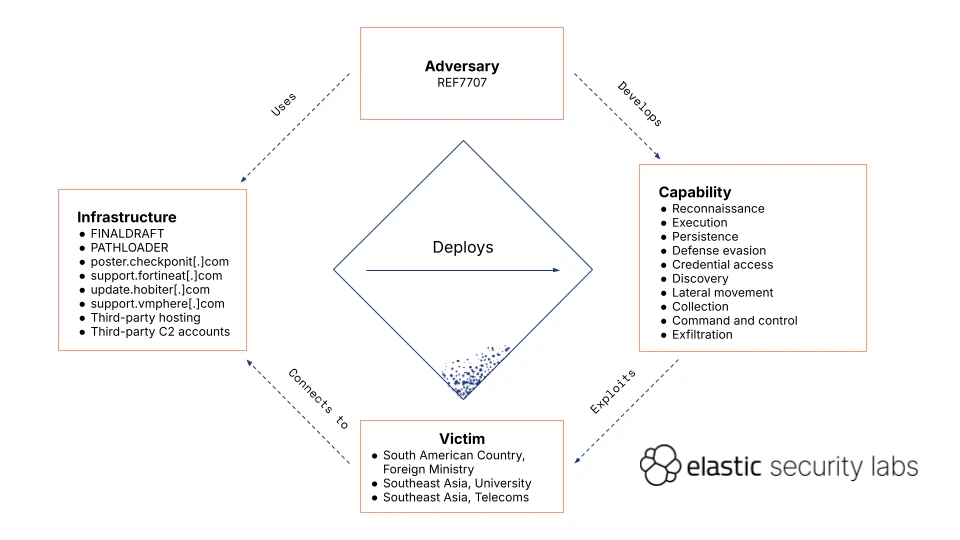
Elastic Security Labs has recently uncovered an expansive cyber espionage campaign, codenamed REF7707, that spans across South America and Southeast Asia. The campaign, which initially targeted the Foreign Ministry of a South American nation, was later found to have deeper connections with a broader set of compromises in Southeast Asia.
The attackers behind REF7707 deployed novel malware families—FINALDRAFT, GUIDLOADER, and PATHLOADER—to gain persistence and execute highly sophisticated intrusions. However, despite their technical proficiency, the threat actors exhibited poor operational security, which inadvertently exposed additional malware, infrastructure, and victims.
REF7707 was first identified in November 2024 when Elastic Security Labs detected an unusual spike in endpoint behavioral alerts at the Foreign Ministry of a South American country. Further investigation revealed a large-scale intrusion set characterized by both high technical sophistication and tactical missteps.
While the attack demonstrated an advanced level of planning and execution, the threat actors inadvertently exposed their own operational footprint. “Numerous tactical oversights exposed malware pre-production samples, infrastructure, and additional victims,” Elastic noted.
The attack leveraged a diverse malware toolkit designed to evade detection and gain persistence within victim networks.
- FINALDRAFT: A Covert Remote Administration Tool
FINALDRAFT is a stealthy, full-featured remote administration tool (RAT) with modular capabilities. Elastic Security Labs found that FINALDRAFT abuses Microsoft’s Graph API for C2 communications, making it difficult to detect using traditional network-based intrusion detection. Once inside a system, it allows attackers to:
- Inject shellcode into trusted processes like mspaint.exe to evade detection.
- Proxy network traffic internally across infected hosts.
- Execute arbitrary commands and payloads using built-in OS functions.
- GUIDLOADER and PATHLOADER: The Malware Delivery Mechanisms
These malware loaders are responsible for downloading and executing encrypted shellcode directly in memory, avoiding traditional disk-based detection mechanisms. The loaders were found communicating with Google Firebase, Pastebin, and Southeast Asian university web storage systems to retrieve FINALDRAFT payloads.
The attackers cleverly leveraged Windows-native tools to carry out their attack, reducing their reliance on custom malware. For example:
- Microsoft’s certutil was used to download and execute payloads from a compromised web server.
- Windows Remote Management’s Remote Shell (WinrsHost.exe) was used for lateral movement, suggesting that attackers had already gained valid credentials from a previous breach.
Elastic Security Labs traced REF7707’s infrastructure across a network of adversary-controlled domains and compromised third-party services. Some key findings include:
- Attackers used adversary-owned infrastructure such as digert.ictnsc[.]com and support.vmphere[.]com.
- Graph API abuse – legitimate Microsoft domains like graph.microsoft[.]com were leveraged to blend in with normal enterprise traffic.
- Suspicious registrations – domains like hobiter[.]com and vm-clouds[.]net were linked to the same service banner hash, indicating a common infrastructure behind the attacks
Despite their technical sophistication, the REF7707 operators made critical mistakes that led to the exposure of their operations. Key errors included:
- Use of debug strings and non-functional malware samples, indicating incomplete testing before deployment.
- Poor domain hygiene, with several REF7707-linked domains still accessible, allowing researchers to intercept malware traffic.
- Failed encryption mechanisms, where certain GUIDLOADER samples had broken decryption routines, revealing adversary TTPs (Tactics, Techniques, and Procedures)
Related Posts:
- High-Profile Organizations in Southeast Asia Hit by Targeted Cyberattacks
- China-Linked Phishing Campaign Exploits Geopolitical Tensions, Ravages Asian Finance Sector
- Bank of America admitted that cryptocurrencies are threatening its business model
- Southeast Asian lose $171 billion due to Cybercrime activity