reFlutter: Flutter Reverse Engineering Framework
reFlutter
This framework helps with Flutter apps reverse engineering using the patched version of the Flutter library which is already compiled and ready for app repacking. This library has a snapshot deserialization process modified to allow you to perform dynamic analysis in a convenient way.
Key features:
- socket.cc is patched for traffic monitoring and interception;
- dart.cc is modified to print classes, functions, and some fields;
- display absolute code offset for functions
- contains minor changes for successful compilation;
- if you would like to implement your own patches, there is a manual Flutter code change is supported using a specially craftedDockerfile
Supported engines
- Android: arm64, arm32;
- iOS: arm64;
- Release: Stable, Beta
Install
# Linux, Windows, MacOS
pip3 install reflutter==0.7.1
Use
Traffic interception
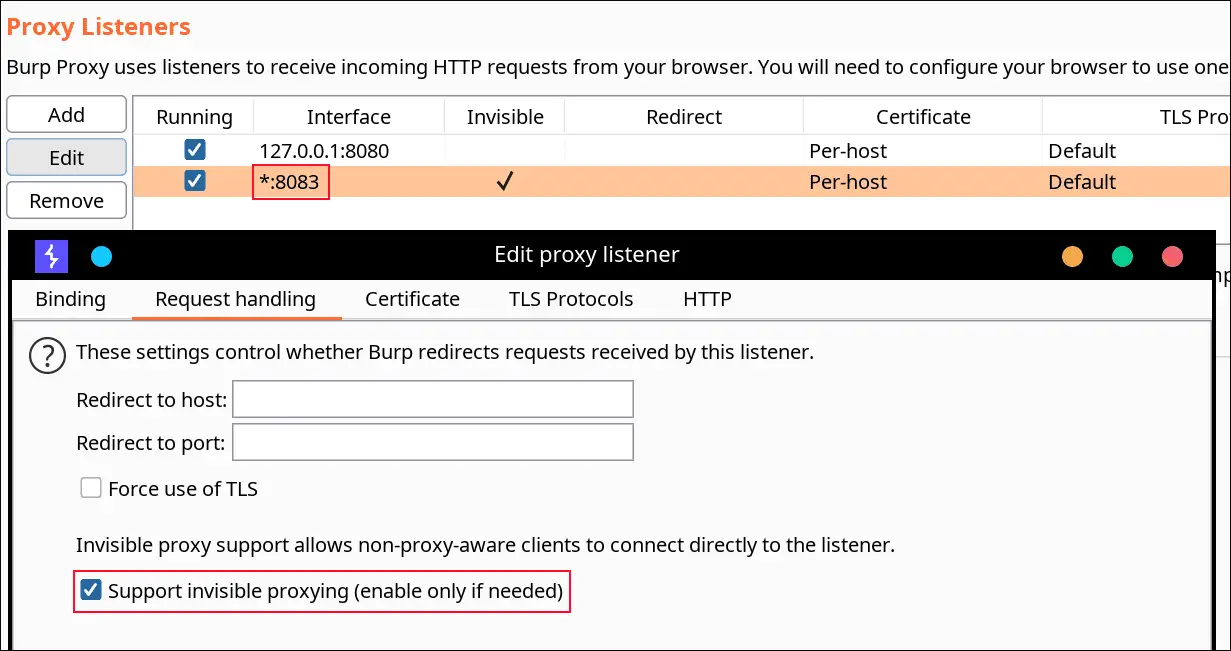
You need to specify the IP of your Burp Suite Proxy Server located in the same network where the device with the flutter application is. Next, you should configure the Proxy in BurpSuite -> Listener Proxy -> Options tab
- Add port: 8083
- Bind to address: All interfaces
- Request handling: Support invisible proxying = True

You don’t need to install any certificates. On an Android device, you don’t need root access as well. reFlutter also allows bypassing some of the flutter certificate pinning implementations.
Usage on Android
The resulting apk must be aligned and signed. I use uber-apk-signer java -jar uber-apk-signer.jar –allowResign -a release.RE.apk. To see which code is loaded through DartVM, you need to run the application on the device. Note that you must manually find what _kDartIsolateSnapshotInstructions (ex. 0xB000 ) equals to using a binary search. reFlutter writes the dump to the root folder of the application and sets 777 permissions to the file and folder. You can pull the file with the adb command.
Usage on iOS
Use the IPA file created after the execution of the reflutter main.ipa command. To see which code is loaded through DartVM, you need to run the application on the device. reFlutter will print the dump file path to the Xcode console logs with the reFlutter tag Current working dir: /private/var/mobile/Containers/Data/Application/<UUID>/dump.dart Next, you will need to pull the file from the device
Frida
The resulting offset from the dump can be used in the frida script
frida -U -f <package> -l frida.js –no-pause
To get value for _kDartIsolateSnapshotInstructions you can use readelf -Ws libapp.so Where is the value you need in the Value field.
Copyright (C) 2022 Impact-I





