Recently, Hudson Rock conducted a comprehensive analysis of a series of data breaches across various hacker forums, subsequently publishing an illuminating report on their findings. The investigation revealed that a staggering 120,000 computers were infected with information-stealing malware, leading to the exposure of approximately 100,000 hackers affiliated with renowned cybercrime forums.
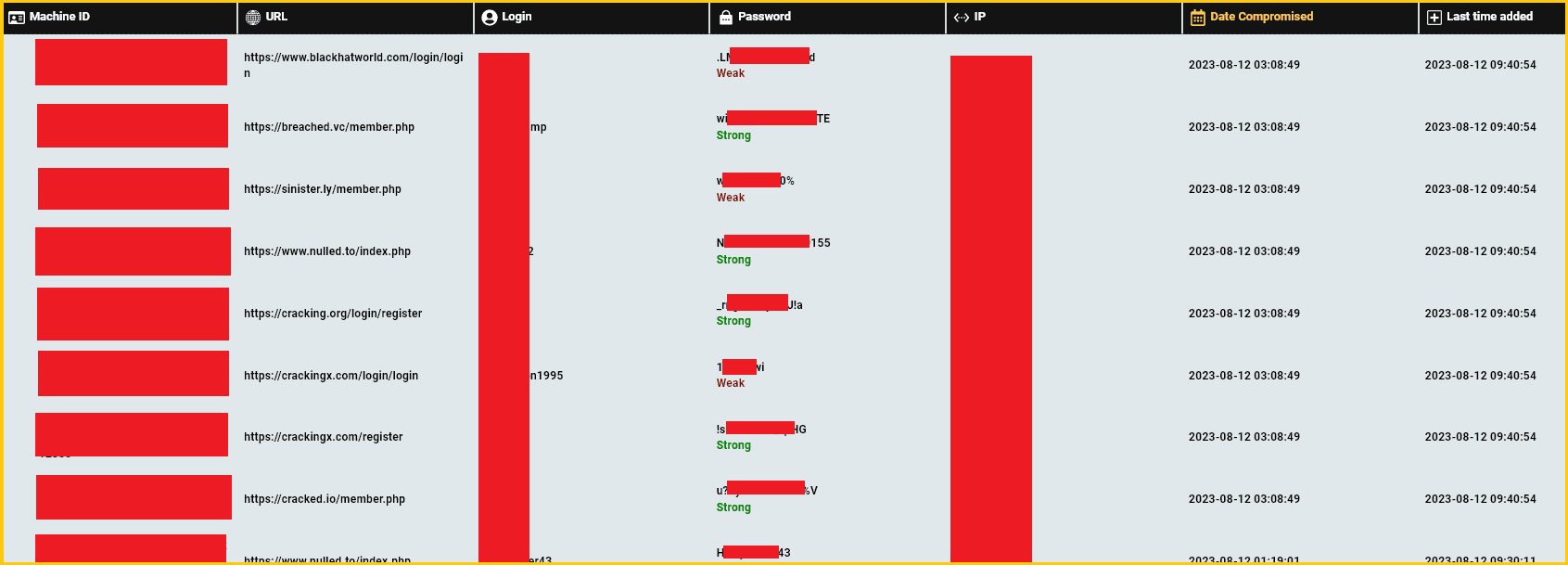
The report elucidates that member data from over 100 prominent cybercrime forums was compromised. This compromised data encompassed details such as hackers’ email addresses, usernames, auto-fill information (including names, addresses, and phone numbers), as well as intricate system details like computer names and IP addresses.
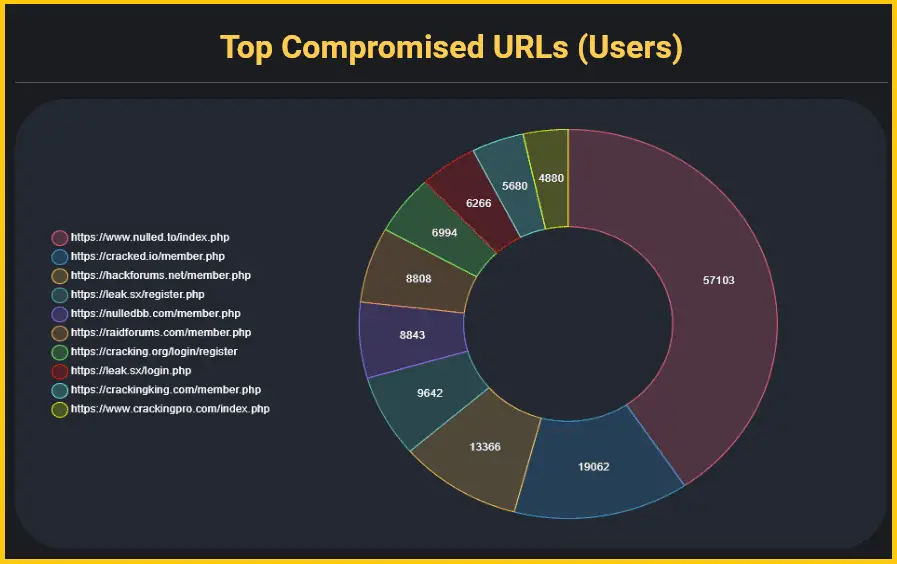
Of all the forums affected, “Nulled.to” bore the brunt of the malware infection. A staggering 57,000 of its users’ devices were contaminated, vastly outnumbering the second and third most affected forums, “Cracked.io” and “Hackforums.net”.
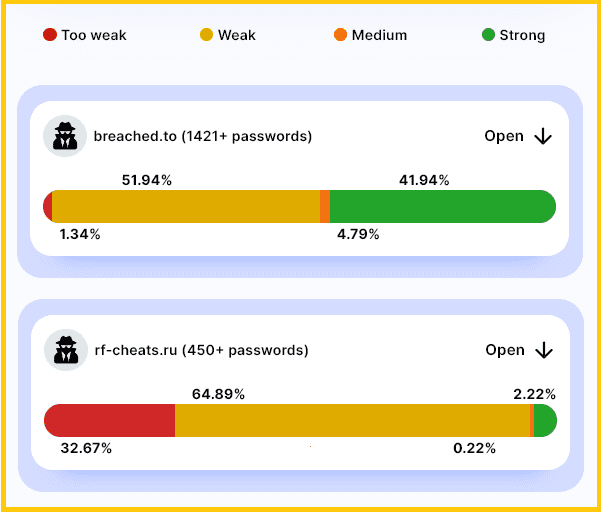
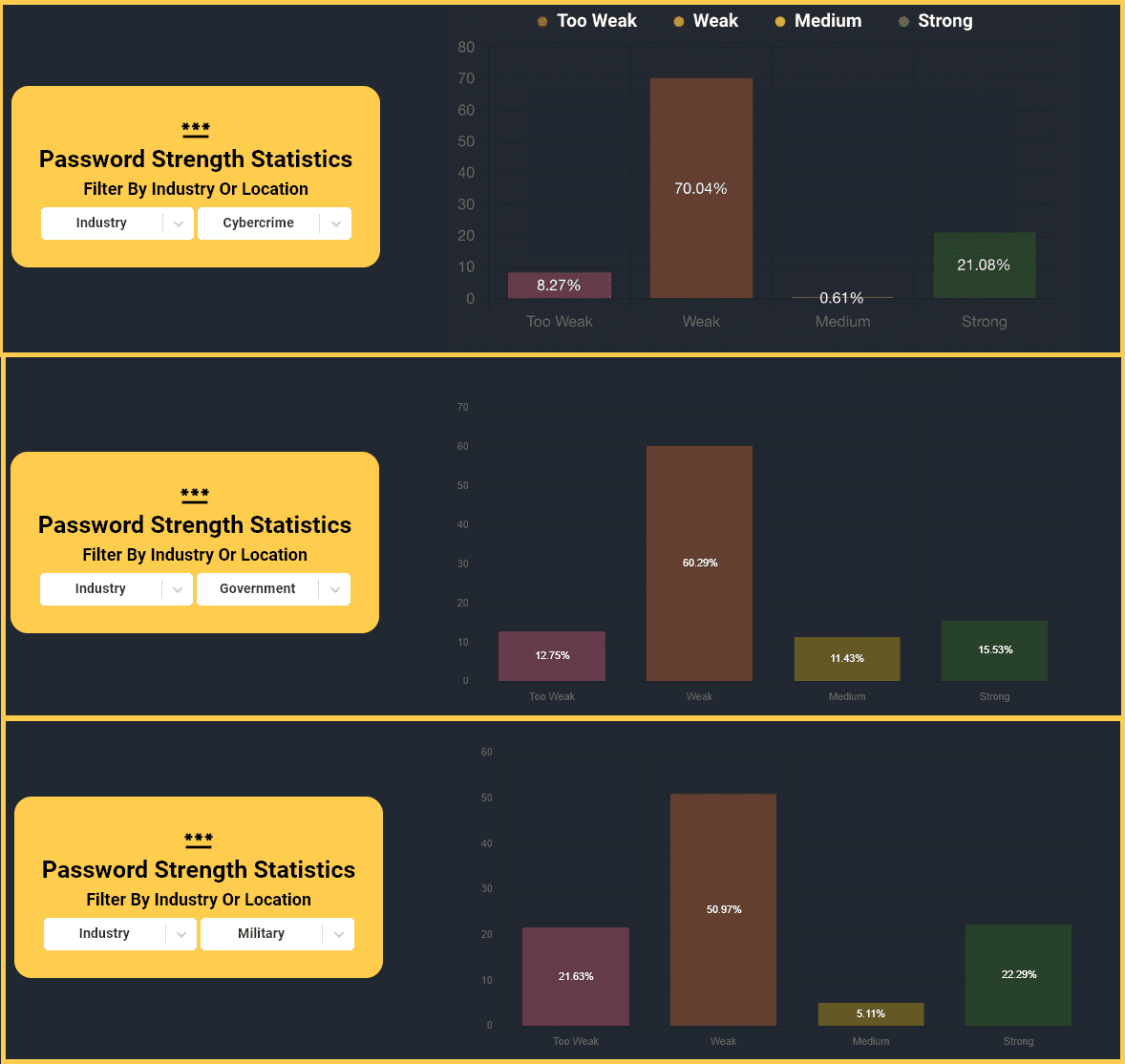
Delving deeper, the report scrutinized password security across various forums. It highlighted that the “Breached.to” forum boasted the most secure user passwords, while the Russian site “Rf-cheats.ru” had the most vulnerable ones. Intriguingly, the leaked passwords from these cybercrime forums were found to be substantially more robust than those used on governmental websites, even surpassing those in sectors such as defense.

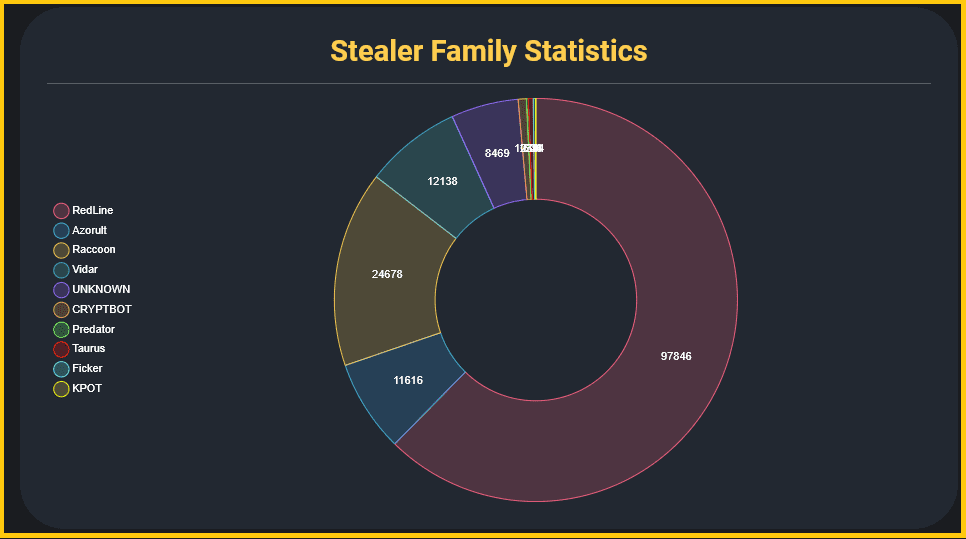
Predominantly, the primary culprit behind the majority of these hacker forum data breaches was the Redline stealer, closely followed by Raccoon and Azorult.
Geographically, the top five countries with the highest number of hackers impacted by this malware were:
- Tunisia, accounting for 7.55% of total infections,
- Malaysia with 6%,
- Belgium at 5.14%,
- The Netherlands with 4.8%, and
- Israel at 4.43%.
Hudson Rock emphasized that since 2018, there has been a meteoric 6000% surge in the trend of infections by information-stealing malware. This nefarious tactic has emerged as the primary initial attack medium for threat actors, enabling them to infiltrate organizations, launch ransomware attacks, execute data breaches, hijack accounts, and engage in corporate espionage.