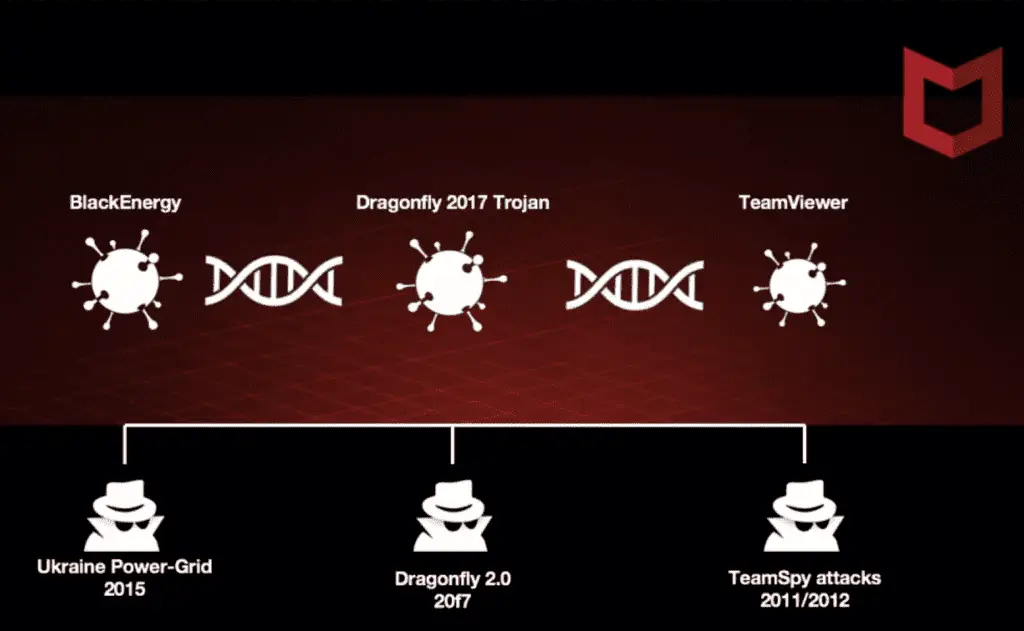
McAfee Labs used the evidence gathered to show that DragonFly malware has a lot to do with other hacking activities such as BlackEnergy and TeamSpy, all of which are technical, tactically, and procedurally similar.
In September, Symantec released a detailed analysis of “DragonFly 2.0”, a hacker-targeted analysis of dozens of energy companies. After further investigation into the cyber attacks on the pharmaceutical, financial and accounting sectors, Symantec The team found similarities in technology, tactics, and procedures (such as spear phishing, specific vulnerabilities, and supply chain contamination). They suspected that the “DragonFly 2.0 Action” was associated with DragonFly observed in 2014 Behind the attack is the same hacker organization.
Link between DragonFly and TeamSpy
Using correlation analysis of the malware, the researchers found that the first two malware used the same TeamViewer in the TeamSpy malware (proposed by Hungarian security firm Crysys Analytics).
TeamSpy hacking has attacked many top institutions, including the Russian Embassy in China, several research and educational institutions in France and Belgium, an Iranian electronics company and a Russian-based industrial manufacturer.
Although previous analyzes tend to attribute hacking attacks to one or more hacking groups and believe they share attack tactics and tools with each other, the researchers also said that the motivation behind hacking team TeamSpy is similar to that of DragonFly.
The link between DragonFly and BlackEnergy
As shown above, the researchers found that the DragonFly malware samples captured this year contained code blocks related to the 2016 BlackEnergy malware.
Although this self-deleting block of code is very common in malware, it is usually done by creating a batch file and executing a batch instead of calling the delete command directly. And by comparing the BlackEnergy sample code and the DragonFly sample captured in Ukraine on October 31, 2015, the researchers found that the code between them was almost always the same, thus revealing the correlation between BlackEnergy and Dragonfly.
More details can be read:
McAfee Report: ” Operation Dragonfly Analysis Suggests Links to Earlier Attacks “
Source: SecurityAffairs