Researcher Details Critical Buffer Overflow Vulnerability in Popular Factorio Game
In the world of video gaming, Factorio has carved out a unique niche. Known for its intricate factory automation gameplay, it has captivated a diverse audience, ranging from avid gamers to computer science students. With over 3.5 million copies sold across various platforms including Windows, Linux, macOS, Steam Deck, and Nintendo Switch, Factorio’s popularity is undeniable. However, the game’s unique programming architecture recently led to an unexpected turn of events—a security vulnerability discovered by a vigilant researcher.
In September 2023, security researcher Valentin-Metz unveiled a critical buffer overflow vulnerability in Factorio. This flaw, lurking within the game’s custom-engine C++ code, posed a significant risk. It allowed for arbitrary code execution when loading or previewing a modified save file, a scenario alarmingly feasible in a game celebrated for its robust modding community.
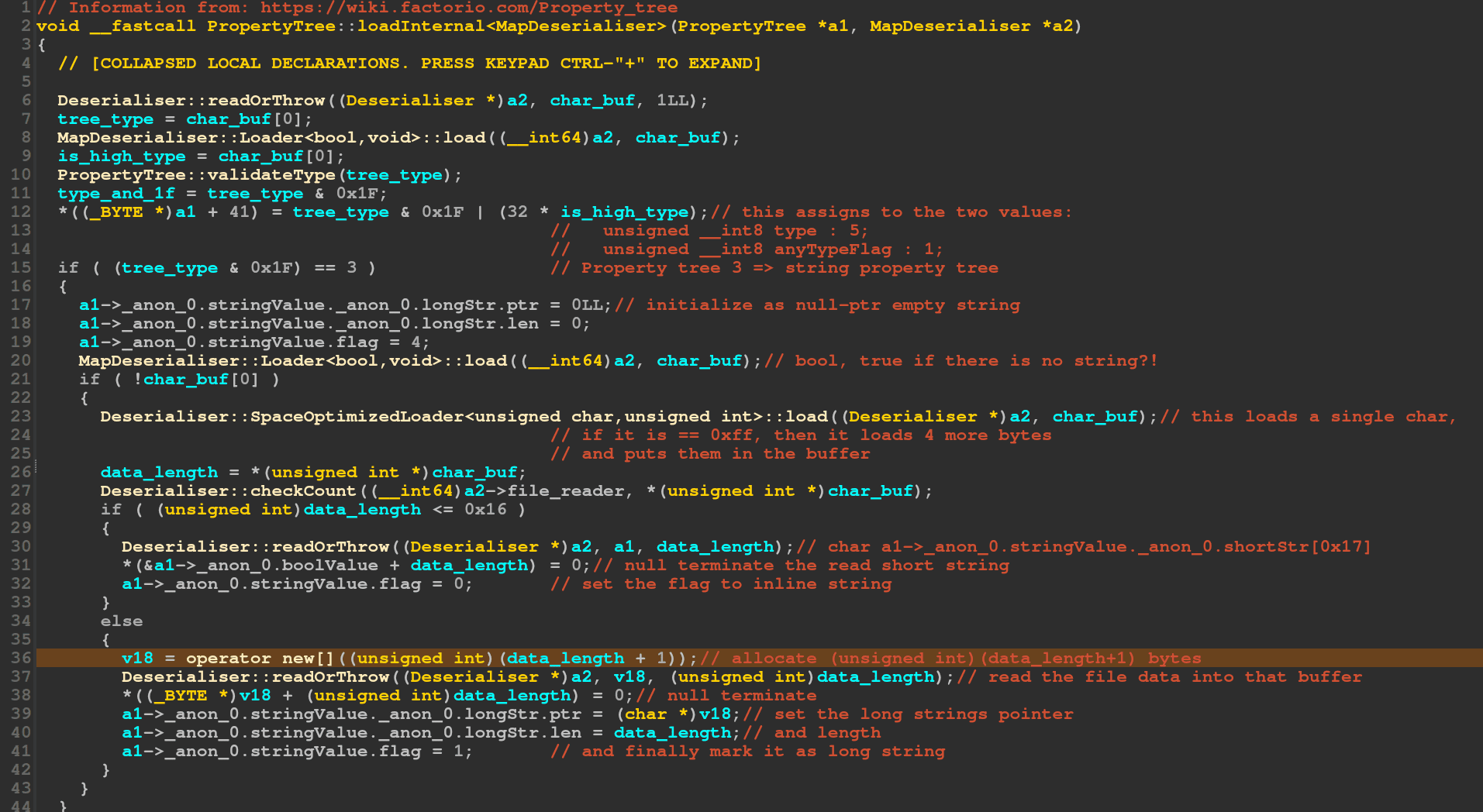
The vulnerability’s roots lay in the calculation of bytes allocation (specifically marked at line 36 in the code). Due to the casting of `data_length + 1` to a 32-bit unsigned integer, a particular input could trigger a wrap-around to zero. Consequently, the deserializer, expecting to read `data_length` bytes, would instead write these bytes into an inadequately sized buffer of one byte. This miscalculation led to a massive heap overwrite.
The specifics of the overflow were intriguing. It consistently resulted in an overflow of 4GiB multiples. The exploit, however, had a caveat; it required the map file to be precisely one byte short of 4 gigabytes. Any deviation and the MapDeserializer would flag an insufficient data error, thwarting the attempt at deserialization.

An interesting aspect of this vulnerability was Factorio’s implementation of the custom `new[]` operator. In standard scenarios, a zero-sized allocation returns a null pointer. However, in Factorio’s code, a zero allocation size defaulted to one, ensuring no allocation returned a null pointer. This nuance played a pivotal role in the exploit’s feasibility.
The researcher has developed the proof of concept exploit on an amd64 Linux machine, and is using the Linux native version of Factorio.
The Factorio team, upon receiving Valentin-Metz’s report and proof-of-concept, acted swiftly. By October 30th, 2023, version 1.1.94 of the game was released, patching the vulnerability.
The Factorio buffer overflow vulnerability serves as a reminder of the complexities and nuances in game development and cybersecurity. It underscores the importance of diligent code review and security practices, especially in applications with large user bases and modding capabilities.





