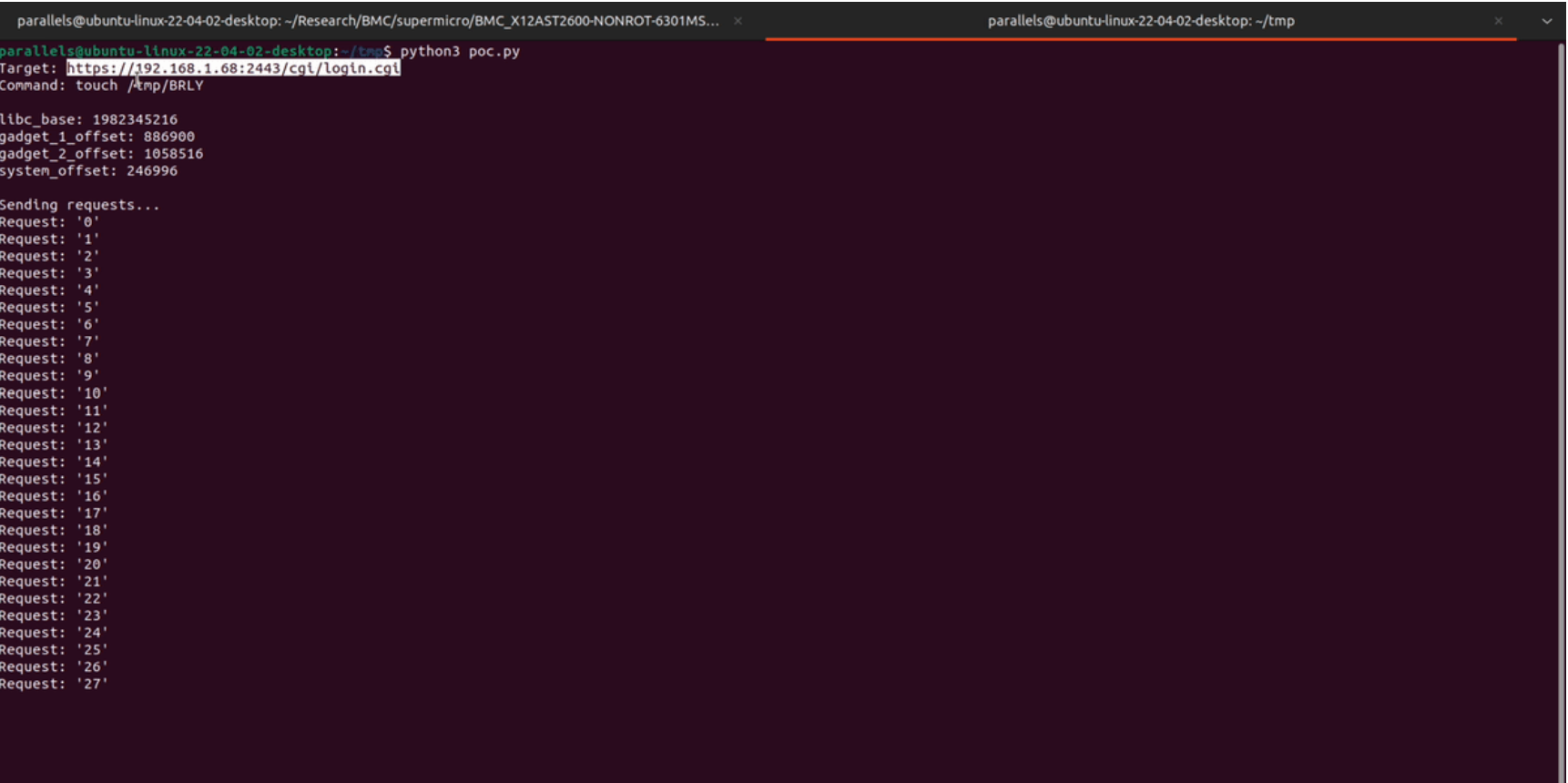
A newly discovered critical vulnerability, CVE-2024-36435, has been uncovered in several Supermicro enterprise products, potentially exposing organizations to significant security risks. Discovered by Alexander Tereshkin from NVIDIA’s Offensive Security Research Team and thoroughly analyzed by the Binarly Research Team, this flaw allows unauthenticated attackers to exploit a buffer overflow in the Baseboard Management Controller (BMC), leading to Remote Code Execution (RCE).
The vulnerability resides within the Baseboard Management Controller (BMC) firmware, responsible for out-of-band management of Supermicro servers. The Binarly Research Team’s analysis reveals a stack-based buffer overflow in the “GetValue” function. This function fails to properly check the size of the input buffer, allowing an attacker to post specially crafted data to the BMC web interface. By manipulating the data sent to the vulnerable /cgi/login.cgi endpoint, the attacker can trigger a stack buffer overflow, which may lead to arbitrary remote code execution.
When a POST request is sent to /cgi/login.cgi, the login.cgi binary retrieves user input parameters such as name and pwd (password). The cgiGetPostVariable function is tasked with extracting these values but does not enforce proper size limits on the input, leading to a mismatch between the actual size of the input data and the size of the buffer allocated for storage (128 bytes).
Furthermore, if the request contains a check parameter, it signals the webserver to Base64 decode the input parameters, which are then stored in smaller stack-allocated buffers (256 bytes). This mismatch opens the door for buffer overflow attacks, as the decoded values can be much larger than the buffer itself.
In the absence of stack canaries, a common protection mechanism in modern systems, this vulnerability becomes trivial to exploit. A skilled attacker can use Return-Oriented Programming (ROP) gadgets from libc to execute arbitrary code on the BMC system, even with NX (No-Execute) mitigations enabled. The researcher published a proof-of-concept exploit code on Github.
The vulnerability has been found to affect a broad range of Supermicro products. Notable among them are:
- MBD-B11SCG-CTF
- MBD-X12DPT-B6
- SYS-4028GR-TVRT
- SSG-2028R-DN2R20L
In total, dozens of Supermicro BMC systems are affected by this vulnerability, impacting servers across industries that rely on Supermicro hardware for critical infrastructure.
What makes CVE-2024-36435 particularly dangerous is its potential to be chained with other known vulnerabilities. For example, combining this flaw with BRLY-2024-023 allows an attacker to manipulate the boot process of the affected server systems, granting persistence on the BMC.
Once root access is achieved via the buffer overflow, attackers can exploit additional vulnerabilities—such as PKfail—to deliver malicious BMC updates signed with compromised keys. This would give attackers long-term access to the system, enabling them to control firmware updates and maintain persistence even after reboots or firmware resets.
Supermicro has acknowledged the severity of this vulnerability and is currently testing and validating affected products.
Related Posts:
- Supermicro Motherboards Vulnerable to Critical RCE Flaw (CVE-2024-36435)
- NVIDIA Fixes Security Vulnerabilities in DGX-1 Firmware
- Urgent Firmware Alert: NVIDIA Tackles Critical DGX A100/H100 Flaws
- Researchers found a new variant of spectre security flaw