PHP released the latest security bulletin on June 9, which contains two vulnerabilities (CVE 2022-31626 & CVE-2022-31625). These flaws’ severity is high. The CVE 2022-31626 vulnerability is heap-based buffer overflow located in a function that handles the legacy mysql auth method. The flaw was reported by security researcher cfreal_.
In PHP versions 7.4.x below 7.4.30, 8.0.x below 8.0.20, and 8.1.x below 8.1.7, there is a buffer overflow vulnerability when processing passwords in mysqlnd/pdo in mysqlnd_wireprotocol.c. When using the pdo_mysql extension with mysqlnd driver, if the third party is allowed to supply a password to the host for the connection, a password of excessive length can trigger a buffer overflow in PHP. This flaw allows a remote attacker to pass a password (with an excessive length) via PDO to the MySQL server, triggering arbitrary code execution on the target system.
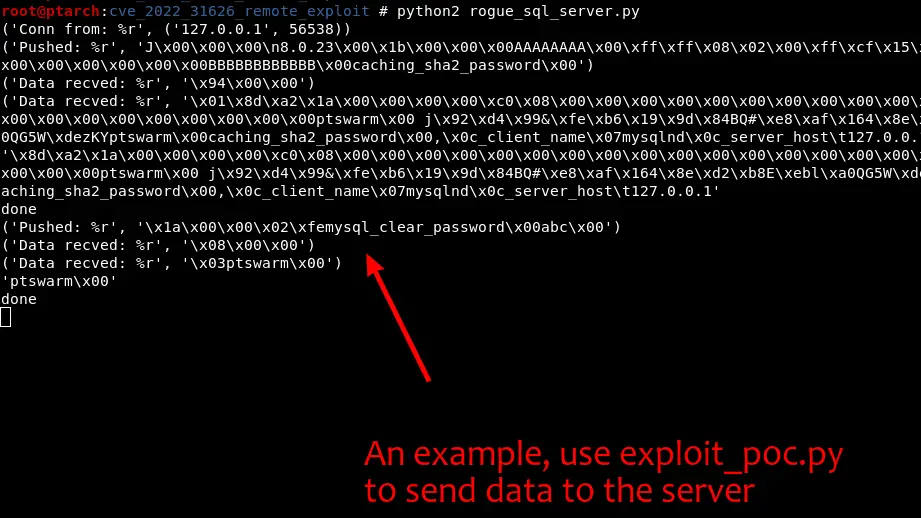
Recently, security researchers from PT SWARM shared the CVE 2022-31626 PoC with the detailed technique, which can be triggered via a rogue MySQL/MariaDB server.

The CVE 2022-31626 PoC includes three files:
- mysql_admin.php – simple web application
- rogue_sql_server.py – script to run fake mysql server (run with python2)
- exploit_poc.py – script to send http-requests to web app.
The researcher writes on the cve_writeup:
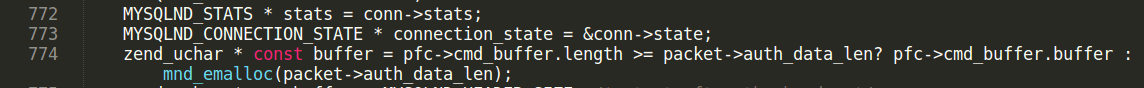
At phase of authorization process, server sends auth switch packet, to do auth with “mysql_clear_password” method. Client accepts it and sends a clear-text password to server. Here the bug happens. File ext/mysqlnd/mysqlnd_wireprotocol.c:
pfc→cmd_buffer.length is length of buffer allocated by mysqlnd to store auth packet by default it is 0x1000. packet→auth_data_len is length of password sent by client. If length of pfc->cmd_buffer.buffer is not enough to store received password, new buffer is allocated using mnd_emalloc. mnd_emalloc uses memory on PHP heap.
CVE 2022-31626 has been fixed in PHP 7.4.30. It’s recommended that users update PHP immediately.