Researcher Releases PoC for Critical RCE Ghostscript (CVE-2023-36664) Vulnerability
A proof-of-concept (PoC) exploit code has been made available for the recently disclosed critical security flaw, tracked as CVE-2023-36664, affecting the popular Ghostscript open-source PDF library, making it imperative that users move quickly to apply the patches.
The flaw, a remote code execution vulnerability with a CVSS score of 9.6, is as treacherous as it sounds. A remote attacker, armed with a malicious and specially crafted file, can carry out nefarious operations, and the mechanisms to prevent this have been found wanting.

Ghostscript’s ubiquity across various Linux distributions, as well as its integration into software such as LibreOffice, GIMP, Inkscape, Scribus, ImageMagick, and the CUPS printing system, amplifies the concern. Opportunities to trigger CVE-2023-36664 are not rare but rather abundant in most cases.
At its core, the CVE-2023-36664 flaw revolves around OS pipes—channels that allow different applications to converse and exchange data. It arises from a specific function in Ghostscript: “gp_file_name_reduce()“, a seemingly benign component that takes multiple paths, combines them, and simplifies them by removing relative path references.
If a specially crafted path is given to this vulnerable function, the outcome is as unexpected as it is dangerous, overriding validation mechanisms and opening a gate to potential exploitation.
Furthermore, Ghostscript’s attempt to open a file involves another function, “gp_validate_path”, to ensure the location’s safety. But since the vulnerable function alters the location details before that check, an attacker can easily exploit the loophole, forcing Ghostscript to engage with files in locations that should remain hidden.
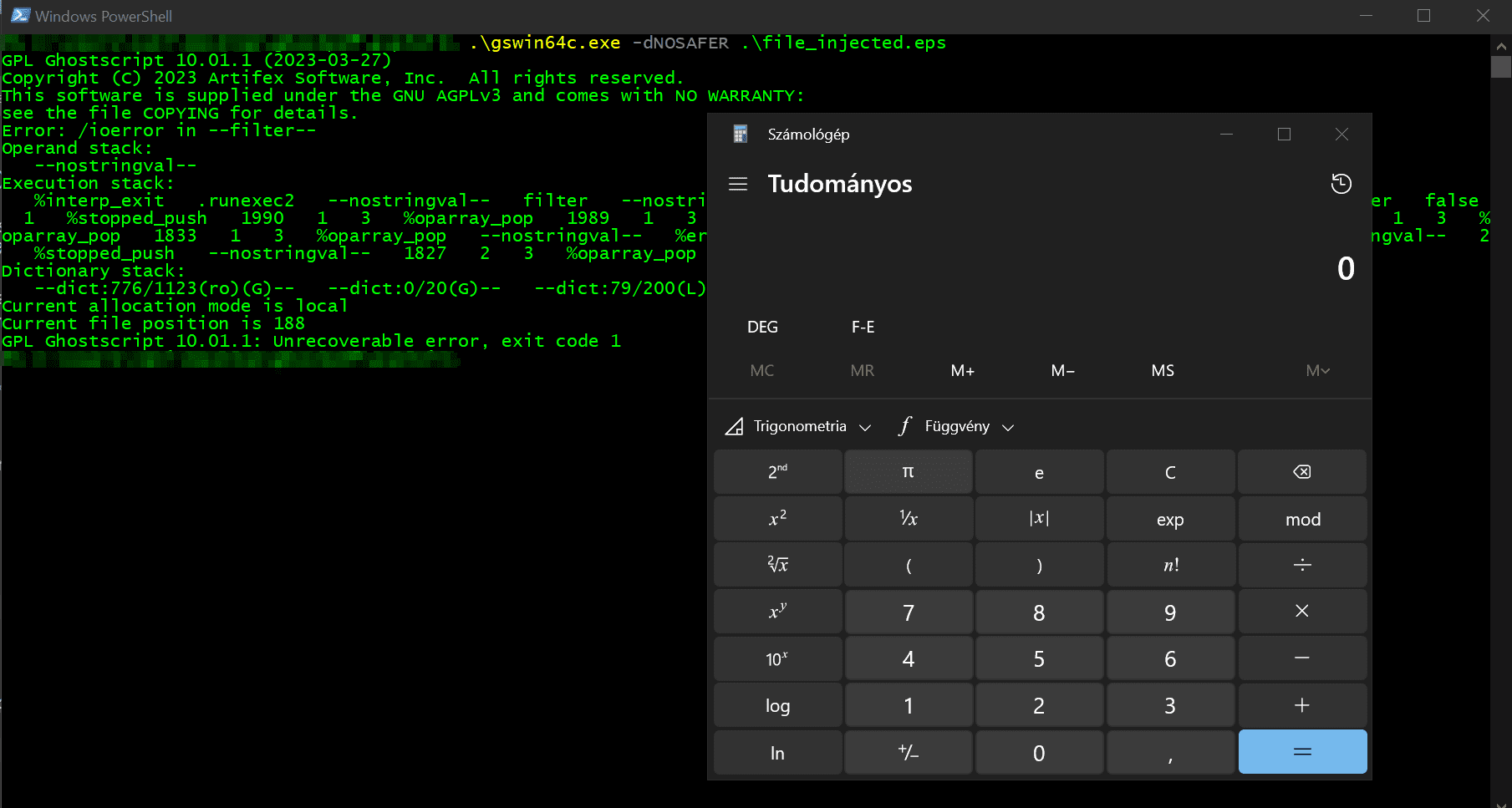
A proof-of-concept (PoC) exploit for CVE-2023-36664 has been created by Ákos Jakab. This PoC exploit is triggered by opening a PS (PostScript) or EPS (Embedded Postscript) file on any application using Ghostscript.
If you are using Ghostscript, it is important to update to the latest version as soon as possible. The latest version, 10.01.2, fixes the vulnerability. You can update Ghostscript using your distribution’s package manager.
If the latest version of Ghostscript is not yet available in your distribution’s software repositories, you can compile it from the source. Instructions for compiling Ghostscript from source can be found on the Ghostscript website.
In addition to updating Ghostscript, you can also take steps to protect yourself from this vulnerability by being careful about opening files from unknown sources. If you are not sure if a file is safe, it is best to avoid opening it.





