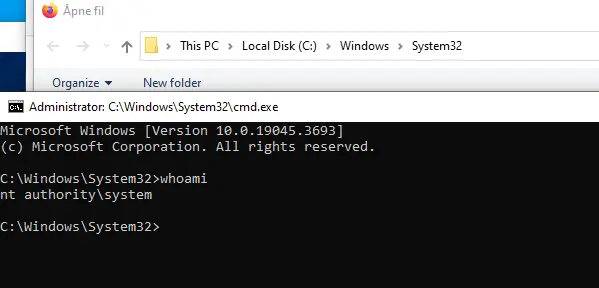
New command window with SYSTEM privileges opens | Image: SEC Consult Vulnerability Lab
A patched zero-day vulnerability (CVE-2024-38014) affecting Microsoft Windows MSI installers has been discovered and exploited in the wild, according to an analysis by security researcher Michael Baer of the SEC Consult Vulnerability Lab. This critical vulnerability, which allows attackers to escalate their privileges to SYSTEM rights, is tied to the repair functions of MSI installers and has been actively exploited before a recent patch from Microsoft.
MSI (Microsoft Installer) files are widely used to install, update, and repair software on Windows systems. While installation and removal generally require elevated permissions, MSI repair functions can be executed by low-privileged users. The problem arises because these repair functions are performed in the context of NT AUTHORITY\SYSTEM, giving the operation one of the highest levels of access in Windows.
Baer’s research highlights how attackers can exploit these MSI repair functions to gain elevated privileges. By taking advantage of briefly opened command windows during the program execution of MSI installers, attackers can escalate their rights to SYSTEM, gaining full control of the affected machine.
While many previous exploit attempts required attackers to slow down the system to keep the elevated windows open long enough for exploitation, Baer’s team has devised a more reliable technique. The new method involves completely pausing the program execution during the MSI repair process. By doing this, attackers can safely manipulate the command window that appears, making it far easier to escalate privileges.
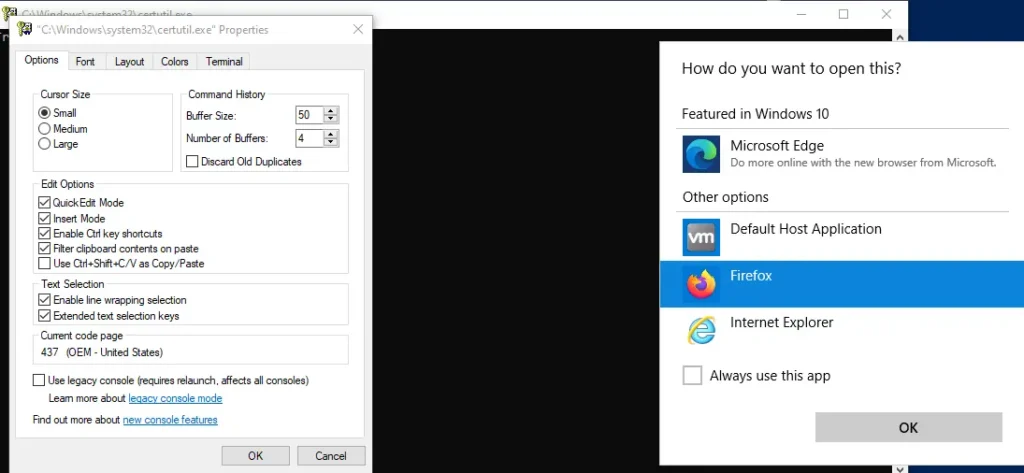
The attack requires GUI access and relies on specific conditions to succeed. Notably, certain browsers like Firefox and Chrome are key to executing the exploit, as newer versions of Edge or Internet Explorer don’t allow the attack to proceed. Once the exploit is executed, the attacker gains full SYSTEM-level privileges, allowing them to take complete control of the machine.
To help administrators and security professionals identify potential vulnerabilities in MSI installers, Baer’s team has released an open-source analyzer tool called “msiscan.” This tool automatically scans MSI files for insecure configurations and potential privilege escalation pathways.
Msiscan provides an efficient way to detect vulnerable installers, focusing particularly on MSI files that invoke custom actions with elevated privileges. The tool performs static analysis, examining the commands executed by the installer and identifying risky behavior, such as the opening of a terminal window or the use of unsafe scripts.
After being contacted by SEC Consult, Microsoft issued a patch for CVE-2024-38014 as part of its September 2024 updates. This patch introduces a User Account Control (UAC) prompt when an MSI repair function is executed with elevated privileges, helping to block unauthorized access. If the UAC prompt is denied, the repair process is aborted, mitigating the risk of privilege escalation.
However, Microsoft’s patch isn’t the only measure organizations should consider. For software vendors, Baer recommends using secure coding practices when developing MSI installers. Custom actions, particularly those involving console applications, should be invoked without visible windows, preventing attackers from interacting with elevated processes.
Administrators should apply the patch as soon as possible and consider disabling the repair functionality in vulnerable MSI installers until the software is fully patched. Additionally, disabling the use of certain installers via registry keys and implementing strong security practices can help mitigate the risks posed by this vulnerability.
Related Posts:
- Intel’s new processor may not be able to repair the new Spectre variant vulnerability
- Microsoft Releases Emergency Repair Patch for Intel CPU Vulnerabilities
- AMD responds to security vulnerabilities: It will be completely repaired in the coming weeks
- Intel: CPUs affected by the vulnerabilities will be fully repaired by the end of January