Image Credit: WatchTowr
A significant security flaw has been uncovered by researchers from WatchTowr, allowing them to obtain Transport Layer Security (TLS) certificates for any .MOBI domain. This exploit raises serious concerns about the current methods used for domain verification and certificate issuance.
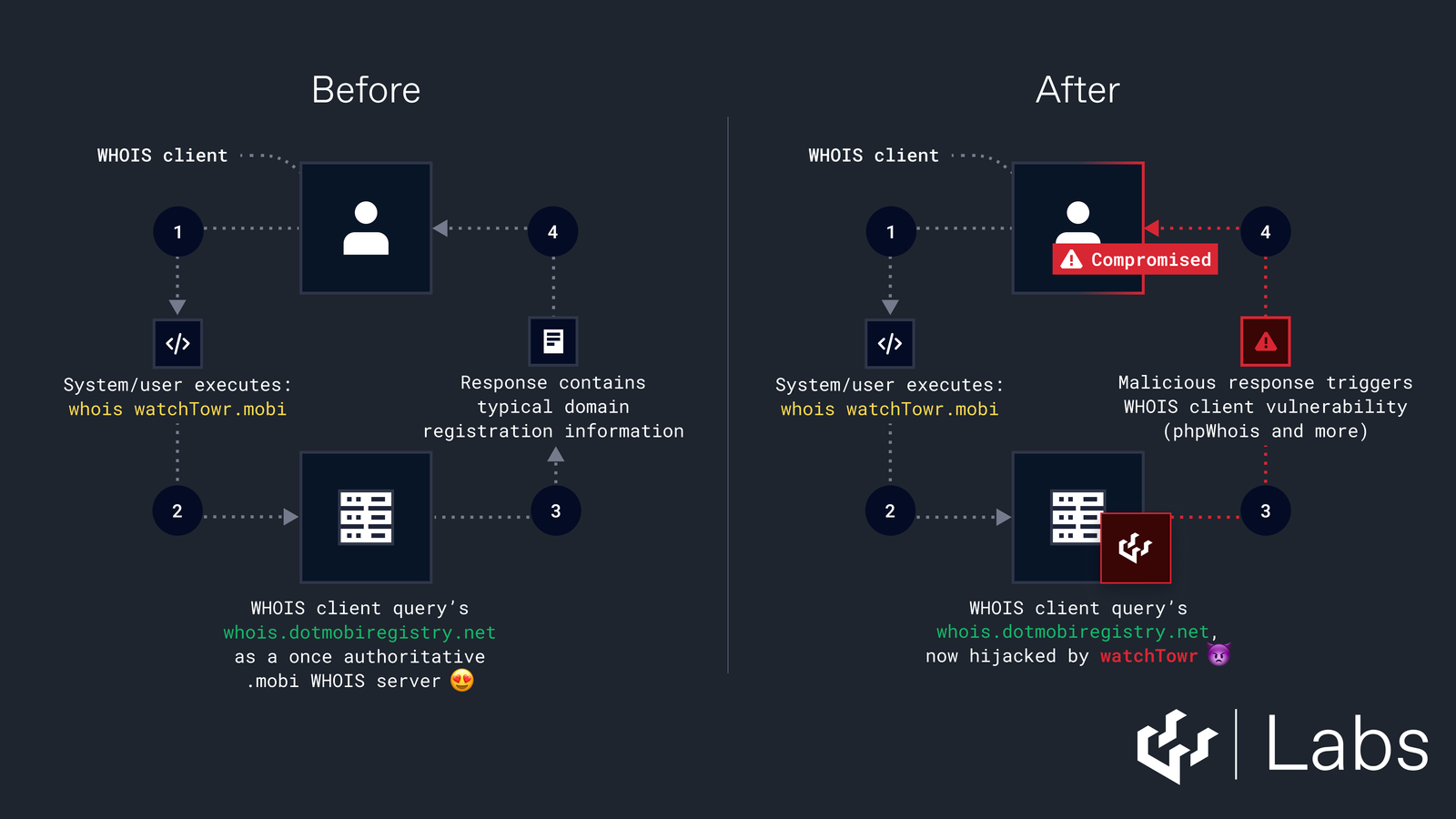
The root of the issue lies in an outdated domain verification process that relies on the WHOIS database. Years ago, the CA/Browser Forum—responsible for setting policies for TLS certificates—implemented a simplified mechanism where Certificate Authorities (CAs) would send an email to the domain administrator. Clicking a link in this email would confirm the certificate request. This method depended on the domain administrator’s email address listed in the WHOIS records.
For .MOBI domains, the official WHOIS server was previously hosted at dotmobiregistry.net. After the registry migrated its services, the domain dotmobiregistry.net was allowed to expire. WatchTowr researchers capitalized on this lapse by registering the expired domain. Despite the migration, several CAs continued to reference dotmobiregistry.net as the official WHOIS server for .MOBI domains. This oversight enabled the researchers to forge WHOIS data and apply for TLS certificates for any .MOBI domain.
Security experts at SecurityOnline have pointed out that this is not just a failure on the part of the registry but highlights an inherent flaw in the verification process established by the CA/Browser Forum. Relying on outdated or unsecured WHOIS data poses significant risks, especially when domains change hands or registries update their infrastructure.
In response to the vulnerability, Google has proposed discontinuing the use of WHOIS data for TLS certificate issuance. The company plans to implement this change by early November 2024. However, other industry players express concerns that this transition period is too short. Major entities like Amazon AWS and leading CAs such as DigiCert advocate for extending the deadline to the end of April 2025. They argue that this extension would provide IT administrators still using WHOIS-based verification ample time to switch to more secure methods like file-based or DNS validation.
DigiCert has proposed adopting the Registration Data Access Protocol (RDAP) to replace WHOIS for domain verification. Established by the Internet Engineering Task Force (IETF) in 2015, RDAP is designed as a successor to WHOIS. It offers secure access to domain registration data, IP addresses, and Autonomous Systems (AS). RDAP supports modern features like standardized queries, secure access, and internationalization, making it a robust alternative for domain verification processes.