Sekoia.io, in collaboration with Intrinsec, conducted an in-depth analysis of the Quad7 (7777) botnet, which utilizes TCP port 7777 on infected routers and carries out brute-force attacks on Microsoft 365 accounts worldwide. Experts detected attacks on 0.11% of monitored accounts.
Key insights highlighted by researchers:
- Botnet Evolution: Quad7 has been active for a long time and continues to evolve. The number of unique IP addresses has decreased from 16,000 in August 2022 to 7,000 in July 2024. The highest number of infected devices are in Bulgaria, Russia, the USA, and Ukraine.
- Botnet Targets: Quad7 targets various IoT devices, including IP cameras, NAS devices, and SOHO routers, primarily TP-Link.
- TP-Link Detection: Botnet operators disable the TP-Link management interface after compromise, making detection difficult. Researchers used the hping3 tool and found that most devices have a TCP window size characteristic of older Linux kernel versions used in TP-Link routers.
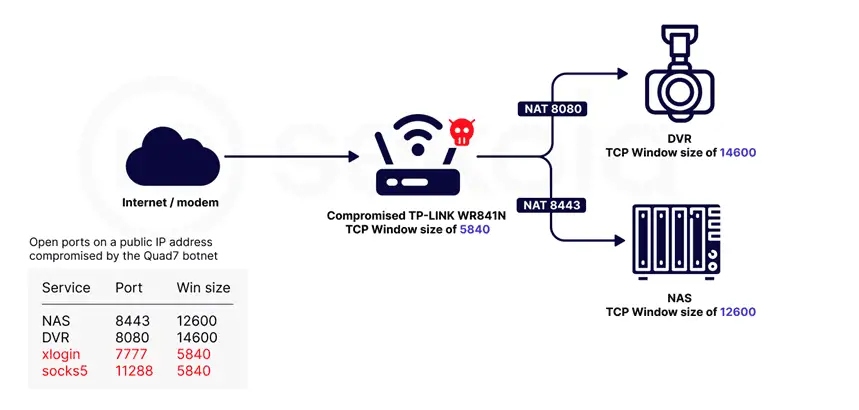
Researchers monitored a TP-Link WR841N router with vulnerable firmware, providing access from five different IP addresses. Experts configured remote analysis and used the Scapy library to monitor authentication attempts.
After several days of observation, an attack was recorded where the attacker exploited a vulnerability to disclose files and execute code. The hacker launched Dropbear (a lightweight SSH agent) on a higher port and transferred a BusyBox utility package via an SSH session, then exited the router, erasing traces.
In another instance, monitoring an infected Archer C7 v2.0 router revealed suspicious processes: telnetd, xlogin, and socks5. The attacker deactivated the web interface by killing the httpd process. The analysis yielded binary files uploaded to the router.
The Telnet binary listens on TCP/7777 and redirects incoming connections to a simple authenticated shell named xlogin. Additionally, a Socks5 proxy server listens on SOCKS/11288, through which brute force attacks on Microsoft 365 accounts are conducted.
Network traffic analysis indicated that the Quad7 botnet is used for Password Spraying attacks on Microsoft 365 accounts. Connections to servers for IP address verification and binary file updates were observed. Despite the research conducted, unanswered questions remain – the attribution of attacks, the vulnerabilities exploited, and the geographical distribution of the botnet. Sekoia.io researchers urge companies with a broader perspective to help solve these mysteries.
Related Posts:
- Old Vulnerability, New Attacks: Botnets Swarm Exploited CVE-2023-1389 in TP-Link Routers
- Mirai Botnet Exploits TP-Link Router’s CVE-2023-1389 Vulnerability
- CISA Adds Seven New Vulnerabilities in Known Exploited Vulnerabilities Catalog
- PoC Released for Unauthenticated RCE Vulnerability in TP-Link VIGI NVR4032H Network Video Recorder
- Millions of Routers at Risk: CVE-2024-21833 Threatens TP-Link Devices