Researchers from UC San Diego, UNC Chapel Hill, Purdue University, Georgia Tech, and Google have exposed a flaw in modern computer processors, revealing a new breed of attacks capable of stealing sensitive information and subtly hijacking the way programs work. The exploit, dubbed ‘Pathfinder‘, zeros in on a crucial but often overlooked component within CPUs called the conditional branch predictor (CBP).
Modern Intel CPUs utilize a feature known as branch prediction to improve processing efficiency. Branch prediction is a mechanism used in high-performance CPUs to enhance processing efficiency. It predicts the paths that program execution might take, allowing the CPU to prepare ahead of time. When predictions are accurate, the CPU operates seamlessly and swiftly; however, inaccurate predictions can introduce delays. While generally beneficial for performance, this feature can be manipulated for malicious purposes.
The researchers introduced new attack primitives that exploit the CPU’s conditional branch predictor. By manipulating the path history register (PHR) and the prediction history tables (PHTs), attackers can both leak (read) and inject (write) information within these structures.
The Pathfinder attack exposes two high-resolution side-channel attacks leveraging the Conditional Branch Predictor (CBP):
- Leakage of Historical Execution Data: The first attack revealed by Pathfinder is particularly novel because it manipulates the branch predictor to leak sensitive information about thousands of recently executed branch instructions. This leakage includes not just outcomes but also precise locations and sequences, allowing an attacker deep visibility into the workings of a secure program.
- High-Resolution Spectre-Style Exploit: The second attack is an advanced form of the notorious Spectre vulnerability. It enables attackers to generate complex patterns of mispredictions intentionally, steering a victim’s CPU into executing unintended code paths, potentially leading to arbitrary code execution or data leakage.
The researchers showcased the potency of these attacks through two vivid case studies:
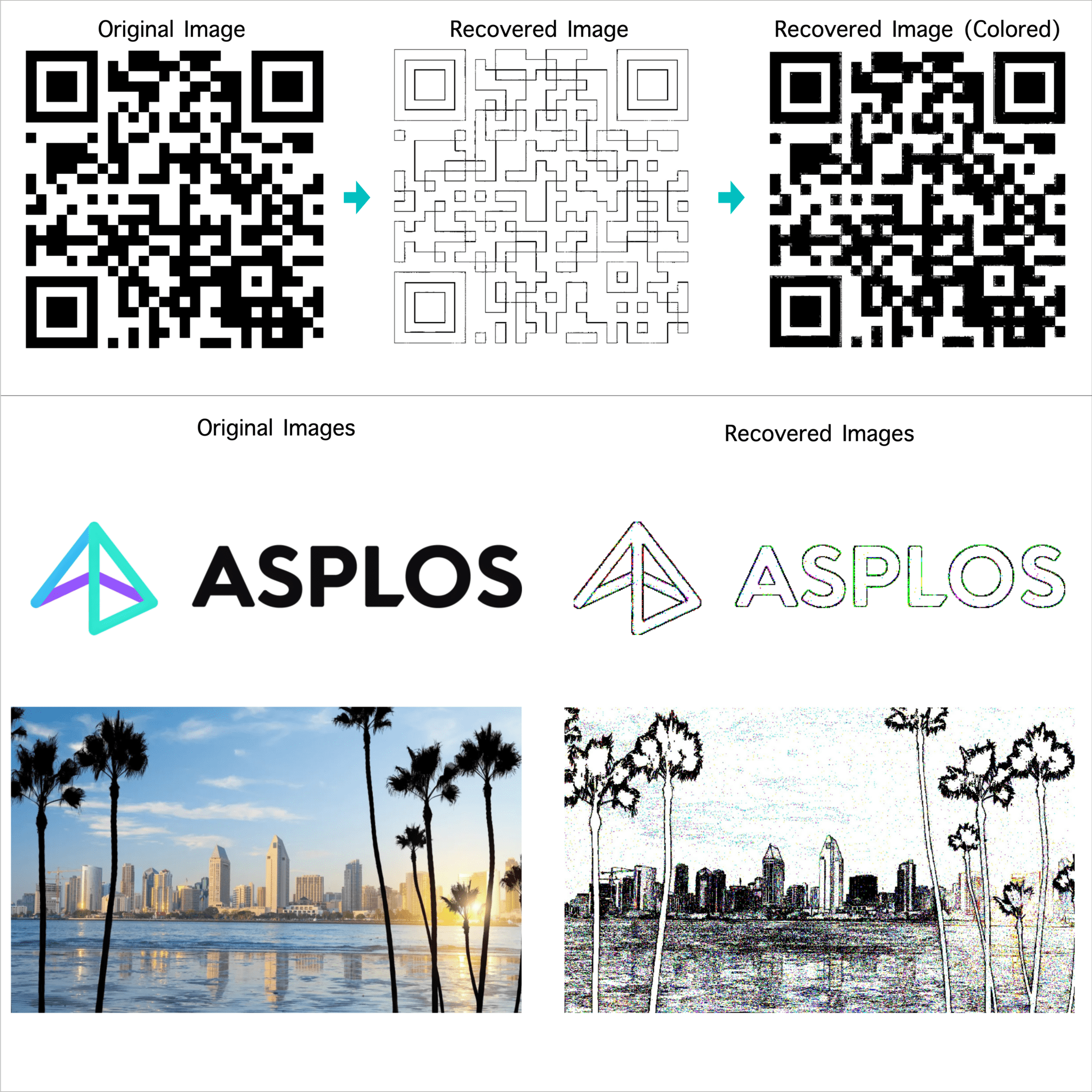
- Speculative Execution Attack Against AES: They executed an attack against the AES encryption algorithm that manipulated speculative execution to reveal intermediate cryptographic values, potentially leading to full key recovery.
- Stealing Images with libjpeg: In another demonstration, the team used their techniques to capture the complete control flow of image processing routines within the libjpeg library, effectively allowing them to steal secret images being processed on the victim machine.

Following responsible disclosure practices, the research team communicated their findings to both Intel and AMD in November 2023. Intel has reportedly informed other affected vendors and planned a security announcement to address the concerns. AMD is also preparing a security bulletin in response to the disclosed vulnerabilities.
To combat these vulnerabilities, the researchers propose several mitigation strategies:
- Flushing the PHR: They suggest using 194 unconditional direct branches to flush the Path History Register (PHR) during context switches between security domains, thus erasing any remnants that could be exploited.
- Randomizing the PHR: Introducing non-deterministic branches during context switching could prevent attackers from predicting or manipulating the PHR effectively.
- Enhanced PHT Security Measures: Suggestions include flushing Prediction History Tables (PHTs) during context switches, partitioning PHTs between security domains, and encrypting index/tag hash functions to safeguard against direct manipulation.