Image: Netskope Threat Labs
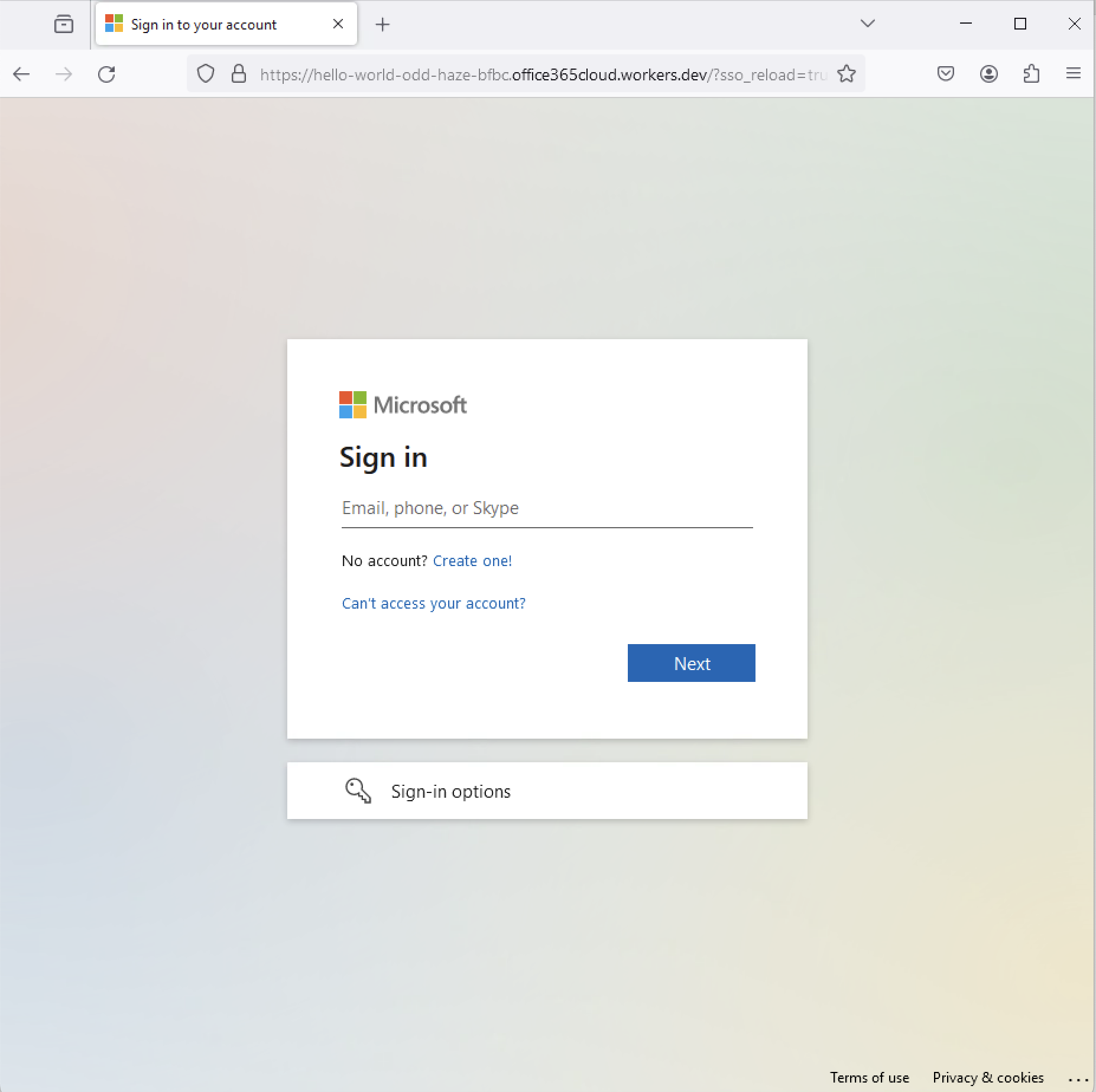
In a recent analysis, Netskope Threat Labs has revealed a disturbing trend of malicious actors exploiting Cloudflare Workers, a serverless computing platform, to launch sophisticated phishing campaigns. These campaigns, potentially orchestrated by multiple threat actors, employ two distinct and concerning techniques: HTML smuggling and transparent phishing.
HTML Smuggling: Evading Detection
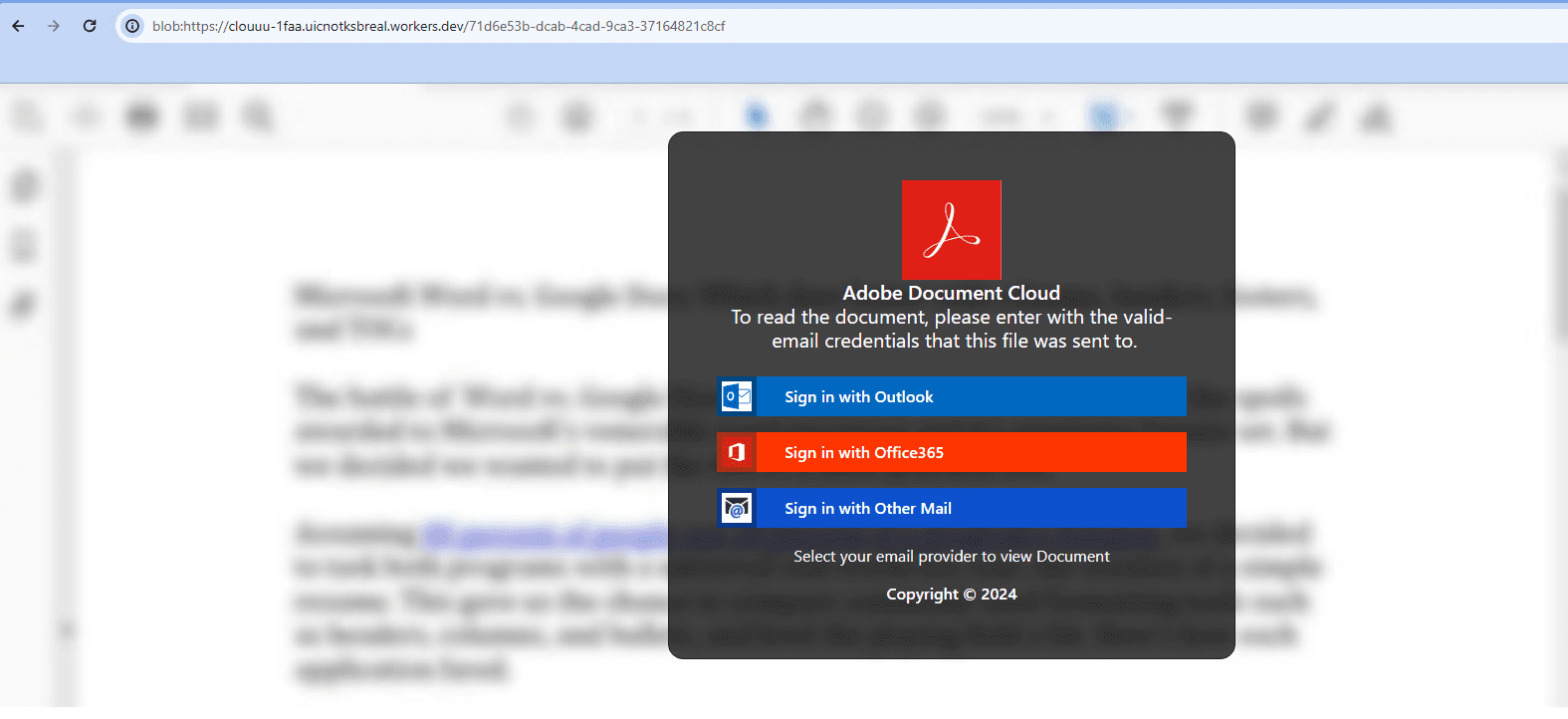
One of the identified techniques involves HTML smuggling, a method where attackers embed malicious code within benign web pages. This code then assembles the phishing page directly on the victim’s device, effectively bypassing traditional network security measures. By delivering phishing content directly to the user’s browser, attackers can evade detection and increase the likelihood of success.
Transparent Phishing: The Invisible Threat

The second technique, known as transparent phishing or adversary-in-the-middle phishing, represents a more sophisticated approach. Attackers position themselves as intermediaries between the victim and legitimate login pages, capturing and forwarding traffic seamlessly. This allows them to steal credentials, cookies, and tokens while providing the victim with a seemingly authentic login experience, making it difficult to detect the ongoing attack.
Scope and Impact
Netskope Threat Labs has observed a steady increase in users targeted by malicious content hosted on Cloudflare Workers throughout 2023 and into 2024. These campaigns have primarily targeted individuals in Asia, North America, and Southern Europe, impacting a wide range of sectors, including technology, financial services, and banking. Notably, Microsoft login credentials have been a primary target for these phishing attacks.
Cloudflare Workers: A Double-Edged Sword
While Cloudflare Workers offers legitimate benefits for developers, its accessibility and features, such as free tiers and generous access limits, have made it an attractive tool for malicious actors. Attackers can create multiple Cloudflare Worker applications, each capable of serving up to 100,000 requests per day, using a publicly accessible domain and a valid TLS certificate.
Mitigation and Recommendations
To protect against these evolving threats, Netskope Threat Labs urges individuals and organizations to remain vigilant and adopt a multi-layered security approach. Users should exercise caution when interacting with URLs ending in “*.workers.dev,” as these may indicate phishing attempts. Additionally, accessing sensitive pages like banking portals or webmail by typing the URL directly into the browser rather than clicking on links is crucial to avoid falling victim to transparent phishing attacks.
Organizations should prioritize security awareness training to educate employees about the latest phishing techniques and encourage them to report suspicious activity promptly. Implementing robust security measures, such as web filtering, email security solutions, and multi-factor authentication, can also significantly reduce the risk of successful phishing attacks.