Illustration of the “Revival Hijack” PyPI attack | Image: Jfrog
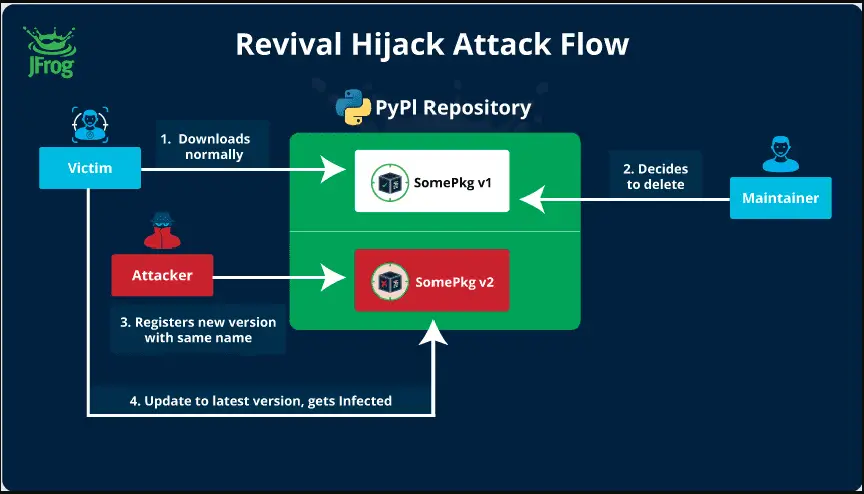
The JFrog security research team has uncovered a novel PyPI package hijacking method known as “Revival Hijack,” which has put over 22,000 packages at risk of exploitation. Unlike traditional typosquatting attacks, which rely on users making spelling errors when installing packages, this new method targets the removal of packages from the Python Package Index (PyPI) repository, creating a new attack vector for malicious actors.
The Revival Hijack technique exploits a critical flaw in the PyPI policy regarding removed packages. When a developer deletes a project from PyPI, the package name becomes immediately available for reuse by anyone. Malicious actors can then register the same package name and release a new, infected version. This creates a serious vulnerability because users and automated systems like CI/CD pipelines, which frequently reinstall packages, will unknowingly pull the hijacked version, mistaking it for a legitimate update.
This hijacking method is particularly dangerous because it doesn’t rely on human error. Users who believe they are simply updating a “trusted” package can unwittingly download a malicious version, making the attack much harder to detect.
The JFrog research team tested this attack by registering a new version of a deleted PyPI package under a different account. Their results were alarming—pip, the Python package manager, did not display any warnings or notices about the package being hijacked. The updated package appeared to be a legitimate new version, when in fact it was under the control of a different user.
The scope of the vulnerability is vast. The team identified over 120,000 removed packages that could be susceptible to Revival Hijack. After refining this list by filtering out malicious or spam packages, and focusing on those with significant download numbers or activity, they discovered that over 22,000 packages were at risk.
The attack surface is further expanded by the 309 packages removed from PyPI each month, leaving new opportunities for attackers to exploit this vulnerability regularly. The use of such packages in automated environments only amplifies the potential for widespread damage, as CI/CD pipelines automatically pull and install packages without user interaction.
The research team found that several popular packages had already been subject to Revival Hijack attacks. The JayDeBeApi3 package, for example, had accumulated 178,000 downloads after being hijacked and re-registered under a new, malicious account. Similarly, other packages like discord-components and gingerit were identified as dependencies in numerous GitHub repositories, making them prime targets for supply chain attacks.
These real-world hijacks serve as a warning to developers and organizations that even abandoned or lesser-known packages can be used to infiltrate sensitive environments. With nearly 200,000 downloads of “safely hijacked” packages observed in the span of just a few months, the danger of this technique cannot be overstated.
The JFrog team has proactively taken measures to protect the PyPI ecosystem by reserving the names of abandoned packages, releasing empty, benign versions to prevent real attackers from claiming them. This mirrors similar efforts seen in the Node Package Manager (NPM) ecosystem.
However, these efforts are not a long-term solution. The JFrog team has recommended that PyPI adopt stricter policies, such as disallowing the reuse of package names once they are removed. Until such measures are implemented, developers are encouraged to block automatic package installations from PyPI and to review any outdated or deleted packages in their environments.
Related Posts:
- CVE-2024-6915 (CVSS 9.3): JFrog Artifactory Flaw Exposes Software Supply Chains to Cache Poisoning
- JFrog Artifactory Vulnerabilities: Patch Now to Protect Your Software Supply Chain
- PyPI Poisoned: 116 Malicious Packages Target Windows and Linux
- Python’s New Threat: Malicious PyPI Packages Targeting Linux Devices