
AhnLab Security Emergency Response Center (ASEC) has issued a warning about a new distribution method for the Rhadamanthys infostealer, a type of malware designed to steal sensitive information from infected computers. This new tactic involves the use of MSC extension files, a format typically associated with the Microsoft Management Console (MMC).
MSC files are XML-based and can be used to execute various tasks, including running scripts, commands, and programs. This flexibility makes them attractive to cybercriminals who can exploit them to deliver malware.
There are two main ways that MSC files are being used maliciously:
- Exploiting a vulnerability in apds.dll (CVE-2024-43572): This method involves using a specific syntax within the MSC file to access and execute code from a vulnerable DLL file. However, this vulnerability has been patched, so this method is no longer effective.
- Using Console Taskpad: This method involves embedding commands within the MSC file that are then interpreted and executed by MMC. This method does not rely on any vulnerabilities and can still be used to deliver malware.
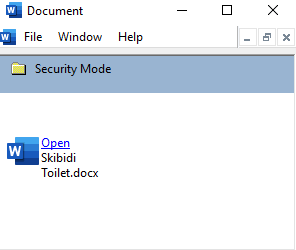
The recent Rhadamanthys infostealer campaign uses the second method, the Console Taskpad. The malicious MSC file is often disguised as a harmless document, such as an MS Word file. When the victim opens the file, it downloads and executes a PowerShell script from an external server. This script then decodes and runs the Rhadamanthys infostealer.
The infostealer itself is designed to steal a variety of sensitive data from the infected machine, including:
- Browser history and cookies
- Cryptocurrency wallets
- System information
- VPN credentials
ASEC warns that the distribution of MSC malware has been on the rise since June 2024. While the vulnerability in apds.dll has been patched, the Console Taskpad method is still a viable way for attackers to deliver malware.
To protect themselves from this threat, users should be cautious when opening MSC files from unknown sources. It is also important to keep software up to date, including security patches, and to use a reputable antivirus program.
Related Posts:
- Tax-Themed Campaign Exploits Windows MSC Files to Deliver Stealthy Backdoor
- New Cyber Threat: RHADAMANTHYS Infostealer Targets Israel
- Rhadamanthys Stealer: MaaS Malware Hits Oil & Gas
- Rhadamanthys Evolves: AI-Powered Crypto Theft with Version 0.7.0
- Hackers Target System Admins with Fake PuTTY Website, Deploy Rhadamanthys Stealer