Image Credit: Rhinosecuritylabs
During an external network penetration test, David Yesland of Rhino Security Labs unearthed a quartet of vulnerabilities within the Extreme Operating System (EXOS) of ExtremeNetworks. These findings are crucial, considering over 1,000 devices were exposed to the internet, running vulnerable versions of EXOS.
CVE-2023-43121: Unauthenticated root file read disclosing password hashes for the device
This vulnerability presents a severe risk, allowing unauthenticated users to read root files, thereby exposing password hashes for the device. Such a flaw can lead to catastrophic breaches, giving attackers the keys to the kingdom.
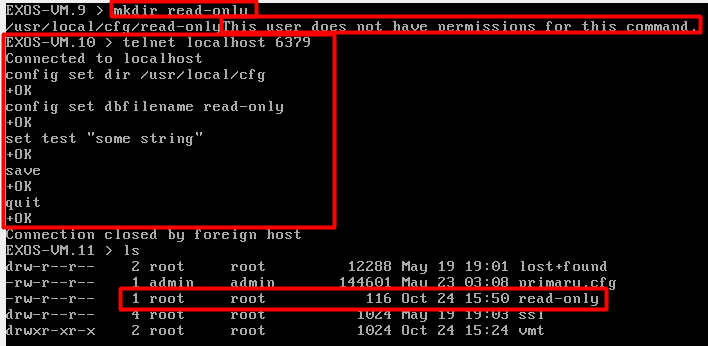
CVE-2023-43120: Privilege escalation from read-only user to read-write admin
A critical issue where a read-only user can escalate their privileges to a read-write admin level. This vulnerability essentially opens a backdoor for attackers to gain extensive control over the network devices, manipulating data and operations at will.
CVE-2023-43118: Cross-Site Request Forgery to Remote Code Execution
This vulnerability is a dangerous pathway from Cross-Site Request Forgery (CSRF) to Remote Code Execution (RCE). It represents a sophisticated attack vector where seemingly benign web requests can lead to complete system takeover.
CVE-2023-43119: Arbitrary file write as root via read-only user
Perhaps the most alarming, this vulnerability enables arbitrary file writing as root through a read-only user. It’s akin to giving a guest key access to every room, including the most secure areas.

Patching the Gaps: Extreme Networks’ Response
Extreme Networks has diligently responded to these vulnerabilities, releasing patches in various versions:
- CVE-2023-43121, CVE-2023-43120: Fixed in 22.7.5.1-patch1-6 or later.
- CVE-2023-43118: Fixed in 31.3.100.20 or later.
- CVE-2023-43119: Fixed in 31.7.2.28-patch1-35 or later.
Fortify your EXOS device security by enabling the “Enhanced Security Mode” during installation. This mode bolsters configuration security and mandates custom user passwords, preventing reliance on default credentials.
Furthermore, proactively alter the default passwords on all deployed devices, regardless of their perceived importance. Overlooking password changes on seemingly less critical devices can create opportune entry points for attackers.
Finally, refrain from exposing management interfaces to the internet. These interfaces possess elevated privileges, and unnecessary exposure expands the potential attack surface.