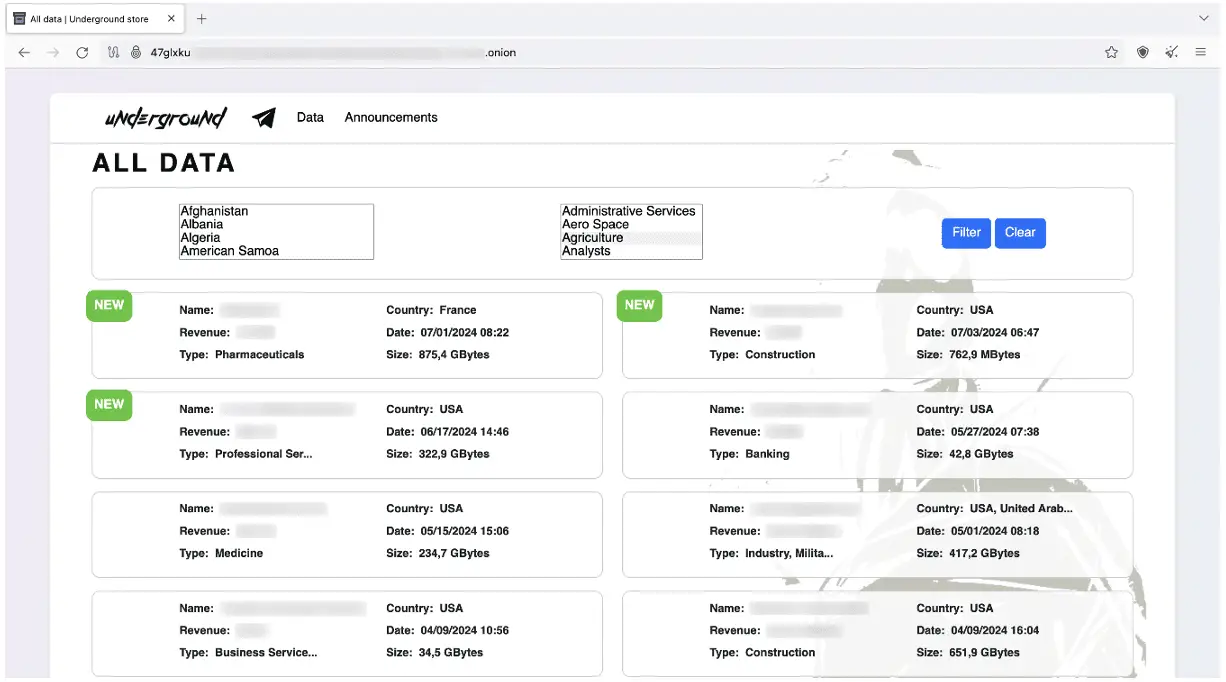
The data leak site for Underground ransomware
FortiGuard Labs found a new ransomware variant, Underground, that has been linked to the Russia-based RomCom group (also known as Storm-0978). This insidious malware encrypts files on victims’ Windows machines, demanding a ransom for decryption. Underground has been active since July 2023 and has targeted a diverse range of sectors, including construction, pharmaceuticals, banking, manufacturing, and more.
The RomCom group is known to exploit a vulnerability in Microsoft Office and Windows HTML (CVE-2023-36884). However, it’s likely they also employ more common tactics like phishing emails and purchasing access from Initial Access Brokers (IABs).
Once Underground infiltrates a system, it systematically disables security measures, deletes shadow copies and event logs, and then encrypts files, leaving a ransom note demanding payment. The group maintains a data leak site where they publish stolen information from victims who refuse to pay.
The Underground ransomware operates by encrypting files on victims’ Windows machines and demanding a ransom for decryption. Unlike some ransomware strains, Underground does not append or change file extensions, making it more challenging for victims to identify which files have been compromised. A ransom note, titled “!!readme!!!.txt,” is left behind, outlining the attackers’ demands.
Underground’s reach is global. The data leak site currently lists 16 victims from various countries, including the USA, France, Germany, Spain, Korea, Taiwan, Singapore, and Canada. The group also utilizes a Telegram channel and the cloud storage service Mega to further disseminate stolen data.
Organizations are urged to ensure their systems are up-to-date, particularly with patches for known vulnerabilities like CVE-2023-36884, and to educate employees about the dangers of phishing and other common attack vectors.
Related Posts:
- 200 million Japanese netizens’ personal data offered on the underground market
- Cybercriminals have been earned over $16 million by distributing ransomware for 2 years
- Millions of Routers at Risk: CVE-2024-21833 Threatens TP-Link Devices