s a n d s i f t e r
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s instruction set, and monitoring execution for anomalies. Sandsifter has uncovered secret processor instructions from every major vendor; ubiquitous software bugs in disassemblers, assemblers, and emulators; flaws in enterprise hypervisors; and both benign and security-critical hardware bugs in x86 chips.
With the multitude of x86 processors in existence, the goal of the tool is to enable users to check their own systems for hidden instructions and bugs.
Install
sudo apt-get install libcapstone3 libcapstone-dev
sudo pip install capstone
git clone https://github.com/xoreaxeaxeax/sandsifter.git
cd sandsifter
make
Use
To run a basic audit against your processor:
sudo ./sifter.py –unk –dis –len –sync –tick — -P1 -t

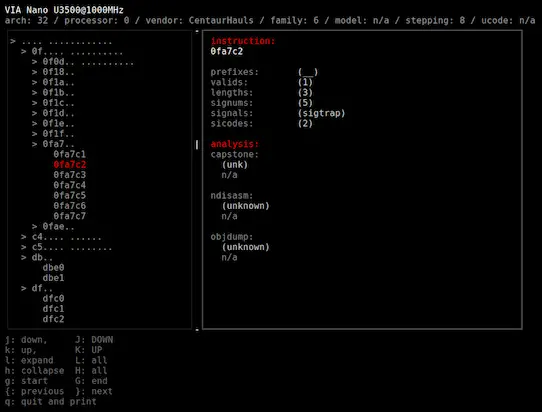
The computer is systematically scanned for anomalous instructions. In the upper half, you can view the instructions that the sandsifter is currently testing on the processor. In the bottom half, the sandsifter reports anomalies it finds.
The search will take from a few hours to a few days, depending on the speed of and complexity of your processor. When it is complete, summarize the results:
./summarize.py data/log

Typically, several million undocumented instructions on your processor will be found, but these generally fall into a small number of different groups. After binning the anomalies, the summarize tool attempts to assign each instruction to an issue category:
- Software bug (for example, a bug in your hypervisor or disassembler),
- Hardware bug (a bug in your CPU), or
- Undocumented instruction (an instruction that exists in the processor, but is not acknowledged by the manufacturer)
Press ‘Q’ to quit and obtain a text-based summary of the system scan:
The results of a scan can sometimes be difficult for the tools to automatically classify, and may require manual analysis.
Results
Scanning with the sandsifter has uncovered undocumented processor features across dozens of opcode categories, flaws in enterprise hypervisors, bugs in nearly every major disassembly and emulation tool, and critical hardware bugs opening security vulnerabilities in the processor itself.
Details of the results can be found in the project whitepaper.
Tutorial
Copyright (c) 2017, Battelle Memorial Institute
All rights reserved.