Cybersecurity researchers at Wiz have uncovered a series of critical vulnerabilities in SAP AI Core, a service designed to develop and deploy AI models. These flaws, collectively dubbed “SAPwned,” could have enabled attackers to access sensitive customer data, manipulate AI models, and even launch widespread supply-chain attacks.
The vulnerabilities, rooted in misconfigurations and inadequate security controls, could have allowed malicious actors to exploit SAP AI Core’s intricate infrastructure. Attackers could have potentially accessed vast amounts of confidential customer data, including AI models, training datasets, and proprietary algorithms. Moreover, the exposed vulnerabilities could have facilitated the manipulation of AI models, leading to tainted data and compromised outcomes.
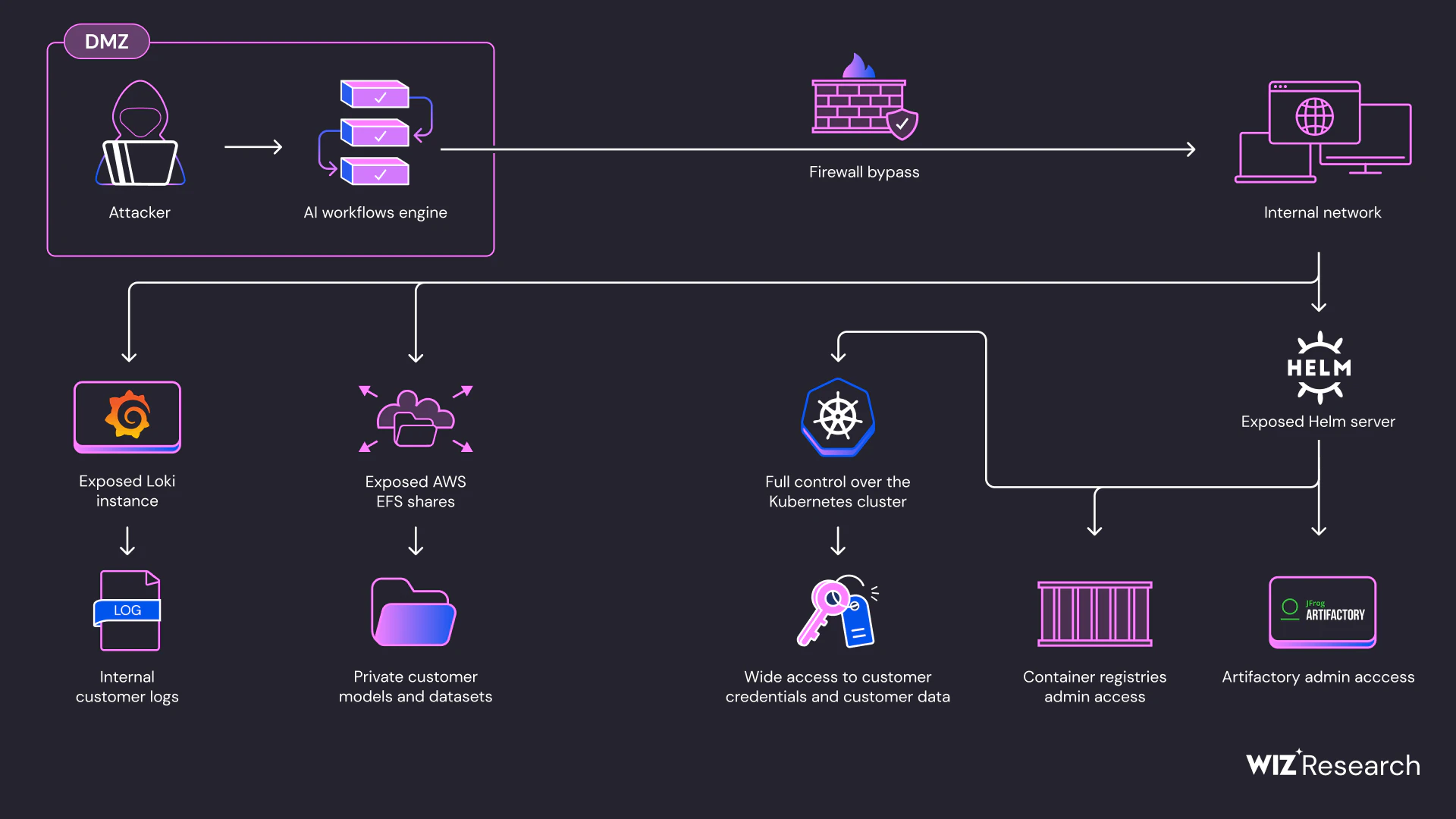
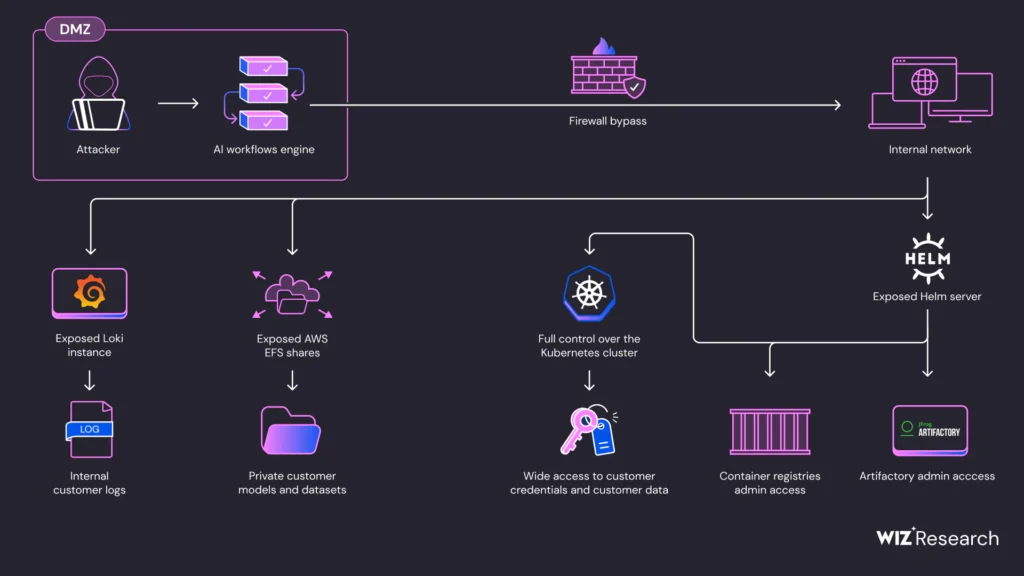
The research commenced with the creation of a standard AI application on SAP AI Core, which utilizes Argo Workflow to spawn Kubernetes Pods. Initially, the environment was restricted, with limited network access enforced by an Istio proxy sidecar. However, researchers found a way to bypass these restrictions using specific Pod configurations that were not blocked by SAP’s admission controller.
- Bug #1: Bypassing Network Restrictions
By configuring the Pod with shareProcessNamespace and runAsUser (with UID 1337, Istio’s UID), the researchers were able to share the process namespace with the Istio proxy sidecar. This provided them with access to Istio’s configuration and an access token to the cluster’s centralized Istiod server, effectively removing network traffic restrictions.
- Bug #2: Loki Leaks AWS Tokens
The researchers discovered an instance of Grafana Loki, which exposed its configuration via the /config endpoint. This included AWS secrets that granted access to an S3 bucket containing logs from AI Core services and customer Pods.
- Bug #3: Unauthenticated EFS Shares
Several AWS Elastic File System (EFS) instances were found with public configurations, allowing free access to their contents without credentials. This exposed large amounts of AI data, including code and training datasets categorized by customer ID.
- Bug #4: Unauthenticated Helm Server
An exposed Helm server component, Tiller, allowed the researchers to access privileged secrets for SAP’s Docker Registry and Artifactory server. This access could be used to extract commercial secrets and conduct supply-chain attacks.
- Bug #5: Full Cluster Takeover
The Helm server’s write access enabled a complete Kubernetes cluster takeover. By deploying a malicious Helm package, researchers gained cluster-admin privileges, allowing them to access and manipulate customer Pods, steal sensitive data, and interfere with AI model integrity. They also accessed customer secrets beyond the scope of SAP AI Core, including AWS, SAP HANA, and Docker Hub credentials.
SAP has acknowledged and addressed the vulnerabilities, assuring customers that no data was compromised. However, the incident serves as a stark reminder of the ever-present cyber threats facing businesses, particularly those relying on cloud-based AI platforms.
The SAPwned vulnerabilities have raised the alarm for the entire AI industry. The incident underscores the critical need for proactive security measures to safeguard sensitive data, protect AI integrity, and mitigate the risk of supply-chain attacks.