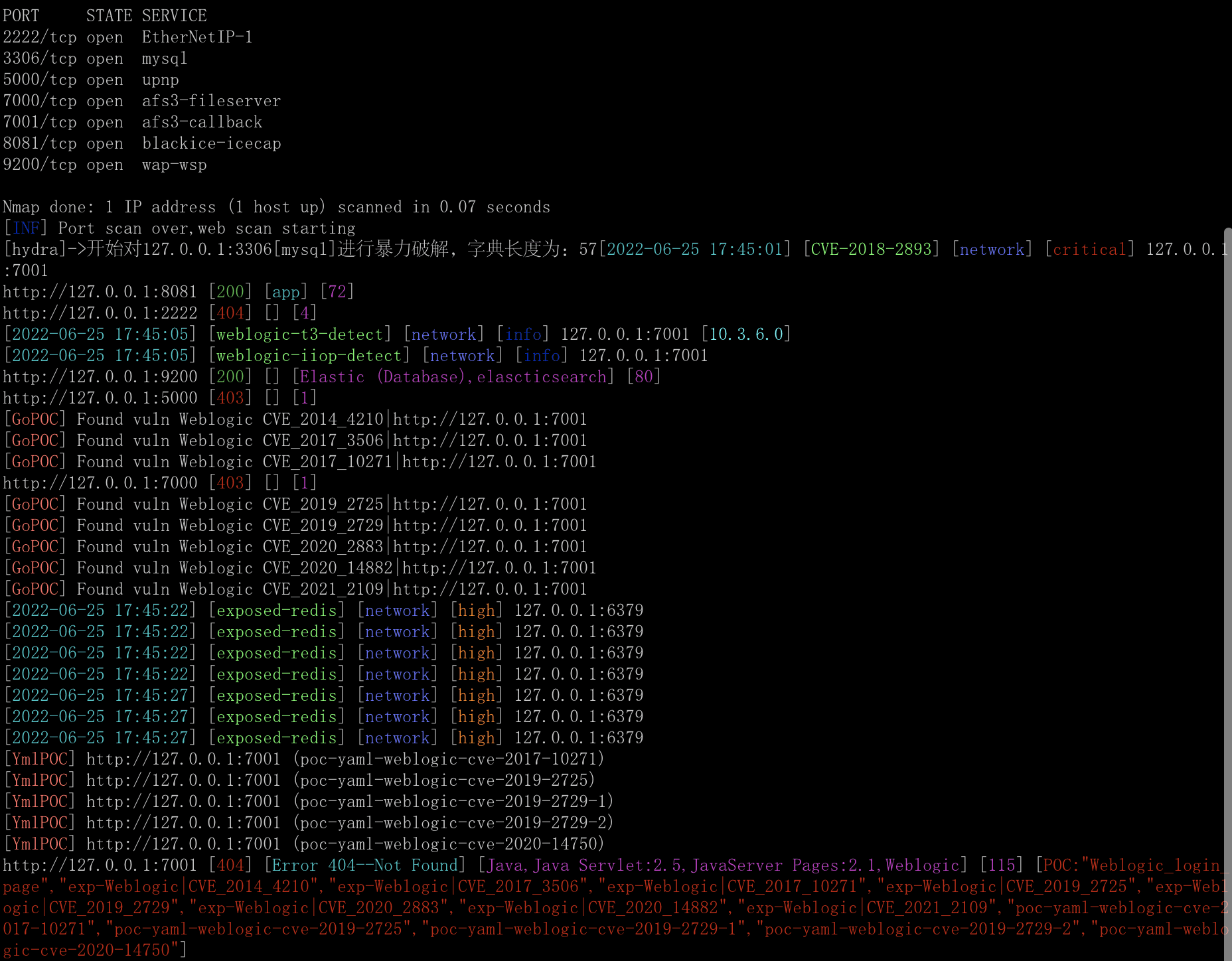
scan4all v2.9.1 releases: Vulnerabilities Scan: 15000+PoCs; 7000+Web fingerprints
scan4all
Vulnerabilities Scan: 15000+PoCs; 20 kinds of application password crack; 7000+Web fingerprints; 146 protocols and 90000+ rules Port scanning; Fuzz, HW, awesome BugBounty…
Features

- What is scan4all: integrated vscan, nuclei, ksubdomain, subfinder, etc., fully automated and intelligent。red team tools Code-level optimization, parameter optimization, and individual modules, such as vscan filefuzz, have been rewritten for these integrated projects. In principle, do not repeat the wheel, unless there are bugs, problems
- Cross-platform: based on golang implementation, lightweight, highly customizable, open source, supports Linux, windows, mac os, etc.
- Support [20] password blasting, support custom dictionary, open by “priorityNmap”: true
- RDP
- SSH
- rsh-spx
- Mysql
- MsSql
- Oracle
- Postgresql
- Redis
- FTP
- Mongodb
- SMB, also detect MS17-010 (CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0147, CVE-2017-0148), SmbGhost (CVE- 2020-0796)
- Telnet
- Snmp
- Wap-wsp (Elasticsearch)
- RouterOS
- HTTP BasicAuth
- Weblogic, enable nuclei through enableNuclei=true at the same time, support T3, IIOP and other detection
- Tomcat
- Jboss
- Winrm(wsman)
- By default, http password intelligent blasting is enabled, and it will be automatically activated when an HTTP password is required, without manual intervention
- Detect whether there is nmap in the system, and enable nmap for fast scanning through priorityNmap=true, which is enabled by default, and the optimized nmap parameters are faster than masscan Disadvantages of using nmap: Is the network bad, because the traffic network packet is too large, which may lead to incomplete results Using nmap additionally requires setting the root password to an environment variable
export PPSSWWDD=yourRootPswd
More references: config/doNmapScan.sh By default, naabu is used to complete port scanning -stats=true to view the scanning progress Can I not scan ports?
noScan=true ./scan4all -l list.txt -v
# nmap result default noScan=true
./scan4all -l nmapRssuilt.xml -v
- Fast 15000+ POC detection capabilities, PoCs include:
- nuclei POC
Nuclei Templates Top 10 statistics
| TAG | COUNT | AUTHOR | COUNT | DIRECTORY | COUNT | SEVERITY | COUNT | TYPE | COUNT |
|---|---|---|---|---|---|---|---|---|---|
| cve | 1294 | daffainfo | 605 | cves | 1277 | info | 1352 | http | 3554 |
| panel | 591 | dhiyaneshdk | 503 | exposed-panels | 600 | high | 938 | file | 76 |
| lfi | 486 | pikpikcu | 321 | vulnerabilities | 493 | medium | 766 | network | 50 |
| xss | 439 | pdteam | 269 | technologies | 266 | critical | 436 | dns | 17 |
| wordpress | 401 | geeknik | 187 | exposures | 254 | low | 211 | ||
| exposure | 355 | dwisiswant0 | 169 | misconfiguration | 207 | unknown | 7 | ||
| cve2021 | 322 | 0x_akoko | 154 | token-spray | 206 | ||||
| rce | 313 | princechaddha | 147 | workflows | 187 | ||||
| wp-plugin | 297 | pussycat0x | 128 | default-logins | 101 | ||||
| tech | 282 | gy741 | 126 | file | 76 |
281 directories, 3922 files.
- vscan POC
- vscan POC includes: xray 2.0 300+ POC, go POC, etc.
- scan4all POC
-
Support 7000+ web fingerprint scanning, and identification:
- httpx fingerprint
- vscan fingerprint
- vscan fingerprint: including eHoleFinger, localFinger, etc.
- scan4all fingerprint
- httpx fingerprint
-
Support 146 protocols and 90000+ rule port scanning
- Depends on protocols and fingerprints supported by nmap
-
Fast HTTP sensitive file detection, can customize the dictionary
-
Landing page detection
-
Supports multiple types of input – STDIN/HOST/IP/CIDR/URL/TXT
-
Supports multiple output types – JSON/TXT/CSV/STDOUT
-
Highly integratable: Configurable unified storage of results to Elasticsearch [strongly recommended]
-
Smart SSL Analysis:
- The in-depth analysis automatically correlates the scanning of domain names in SSL information, such as *.xxx.com, and complete subdomain traversal according to the configuration, and the result will automatically add the target to the scanning list
- Support to enable *.xx.com subdomain traversal function in smart SSL information, export EnableSubfinder=true, or adjust the configuration file
-
Automatically identify the case of multiple IPs associated with a domain (DNS), and automatically scan the associated multiple IPs
-
Smart processing:
-
- When the IPs of multiple domain names in the list are the same, merge port scans to improve efficiency
- Intelligently handle http abnormal pages, and fingerprint calculation and learning
-
-
Automated supply chain identification, analysis, and scanning
-
Link python3 log4j-scan
- This version blocks the bug that your target information is passed to the DNS Log Server to avoid exposing vulnerabilities
- Added the ability to send results to Elasticsearch for batch, touch typing
- There will be time in the future to implement the golang version and how to use.
mkdir ~/MyWork/;cd ~/MyWork/;git clone https://github.com/hktalent/log4j-scan
- Intelligently identify honeypots and skip targets. This function is disabled by default. You can set EnableHoneyportDetection=true to enable
- Highly customizable: allow you to define your own dictionary through config/config.json configuration, or control more details, including but not limited to: nuclei, httpx, naabu, etc.
- support HTTP Request Smuggling: CL-TE、TE-CL、TE-TE
- Support via parameter Cookie=’PHPSession=xxxx’ ./scan4all -host xxxx.com, compatible with nuclei, httpx, go-poc, x-ray POC, filefuzz, http Smuggling
Changelog v2.9.1
Install & Use
Copyright (c) 2021, hktalent
All rights reserved.





