
Recently, researchers at the Austrian SEC Consult found a key set of vulnerabilities in the Mi-Cam Infant Monitor that vulnerable over 52,000 baby monitors and user accounts. Exploiting these vulnerabilities, attackers have free access to these devices and open a video stream to monitor children without being authenticated.

Mi-Cam baby monitor manufactured by China MiSafes company, which is equipped with an online video surveillance system and 720P HD camera, parents can connect monitors through Android and iOS devices to care for children.
The researchers said there are six major vulnerabilities in this group, one of which is that an attacker could use a proxy server to intercept communications between the monitor and the smartphone without the need for a client-side SSL certificate or password.

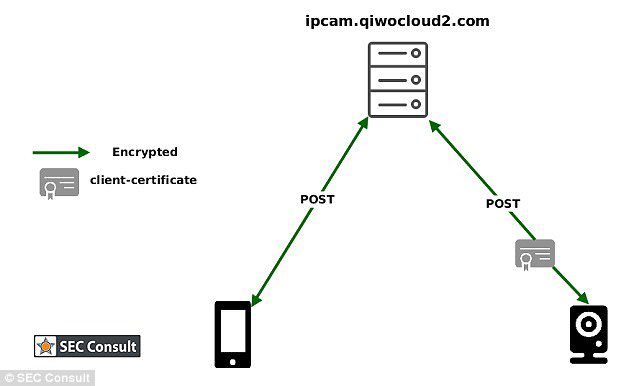
Another loophole comes from the device’s forgotten password feature, which allows Mi-Cam to reset the password, in order to verify that the user will send a 6-digit verification key to the email address the customer was using when registering. For hackers, it’s easy to crack a client’s account and get a key.
In addition, one of the vulnerabilities allows an attacker to extract the firmware to confirm the four-digit default password, which has a very weak security effect.
The researchers said the software used in these baby monitors is outdated and contains many well-known vulnerabilities. The SEC Consult repeatedly informed MiSafes device security issues since December 2017, but the company did not respond.
Source: dailymail