Second Order
Scans web applications for second-order subdomain takeover by crawling the app, and collecting URLs (and other data) that match certain rules, or respond in a certain way.
Usage Ideas
This is a list of tips and ideas (not necessarily related to second-order subdomain takeover) on what to use Second Order for.
- Check for second-order subdomain takeover: takeover.json. (Duh!)
- Collect inline and imported JS code: javascript.json.
- Find where a target hosts static files cdn.json. (S3 buckets, anyone?)
- Collect <input> names to build a tailored parameter bruteforcing wordlist: parameters.json.
- Feel free to contribute more ideas!
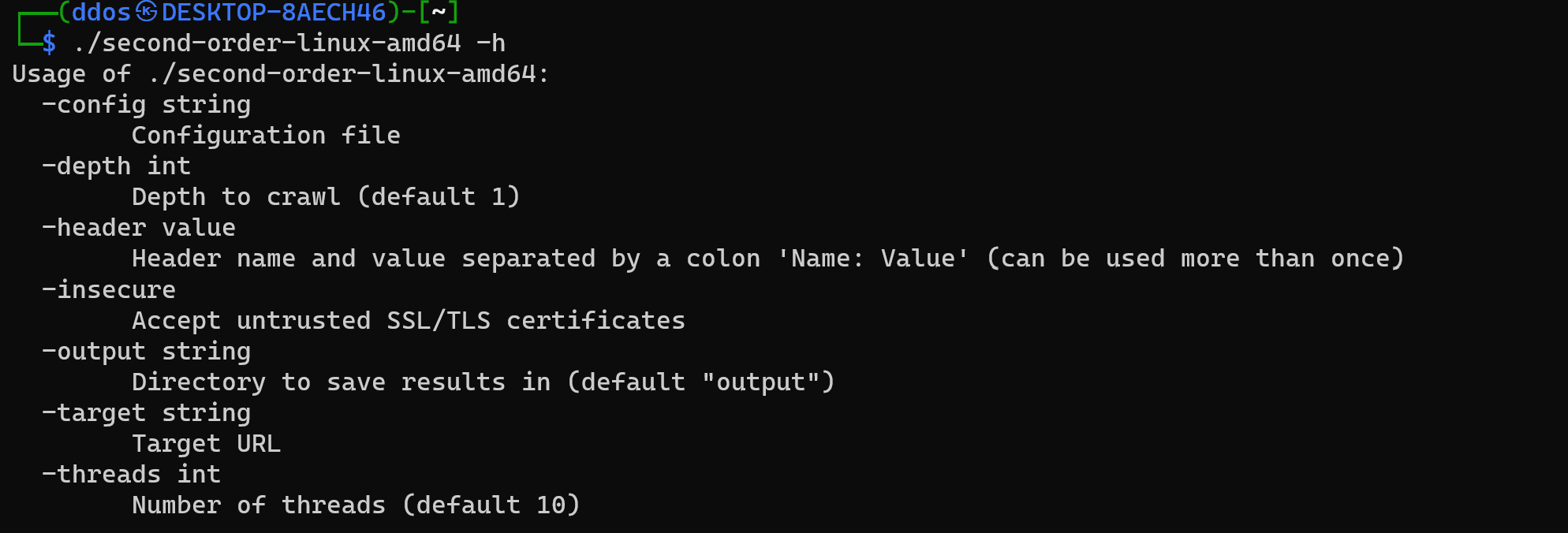
Use

Configuration File
Example configuration files are in config
- LogQueries: A map of tag-attribute queries that will be searched for in crawled pages. For example, “a”: “href” means log every href attribute of every a tag.
- LogNon200Queries: A map of tag-attribute queries that will be searched for in crawled pages, and logged only if they contain a valid URL that doesn’t return a 200 status code.
- LogInline: A list of tags whose inline content (between the opening and closing tags) will be logged, like title and script
Output
All results are saved in JSON files that specify what and where data was found
- The results of LogQueries are saved in attributes.json
- The results of LogNon200Queries are saved in non-200-url-attributes.json
- The results of LogInline are saved in inline.json
Changelog v3.2
- Add random useragent by @hazanasec in #14
Install
Copyright (c) 2022 Mohammed Diaa