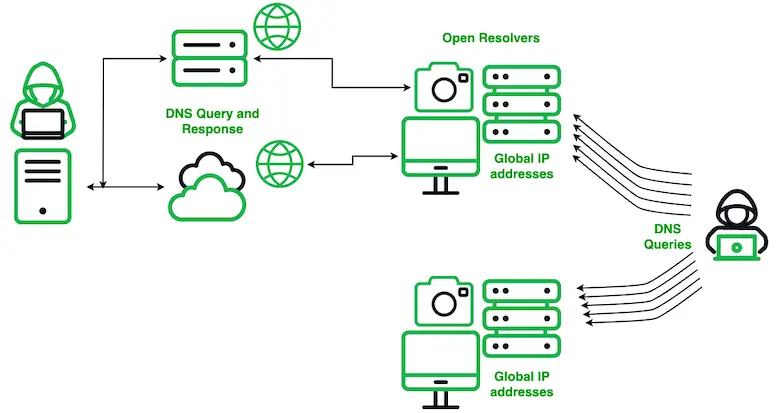
A simplified view of the Secshow DNS probing operations; open resolvers result in queries sent to the Secshow actor for resolution
A massive DNS probing operation, dubbed “Secshow,” has been underway since June 2023, targeting open DNS resolvers worldwide. Researchers at Infoblox Threat Intel and Dave Mitchell discovered that this operation not only identifies vulnerable resolvers but also measures their reactions to different responses.
The Secshow actor, operating from the China Education and Research Network (CERNET), utilizes name servers that return random IP addresses for many queries. This triggers an amplification of queries by Palo Alto’s Cortex Xpanse product, a security tool designed for attack surface management. This amplification results in the pollution of passive DNS collections, hindering cybersecurity research and resource burdens on DNS providers globally.

The ultimate goal of Secshow remains unknown, but the information gathered could be used for malicious activities. The operation involves sending DNS queries to IP addresses globally, encoding the target IP address and a timestamp. Open resolvers respond, providing information that could be exploited for cyberattacks.
The scale and complexity of the Secshow operation raise concerns. Its utilization of wildcard configurations and Cortex Xpanse’s unfiltered scanning have dramatically increased the volume of malicious traffic, making it difficult to differentiate between genuine threats and amplified noise.
While designed to enhance security, Cortex Xpanse’s behavior has inadvertently amplified the impact of Secshow’s probes. It treats domain names in DNS queries as URLs and attempts to retrieve content from the random IP addresses returned by Secshow’s name servers. This triggers a chain reaction of DNS queries, resulting in significant amplification of malicious traffic.
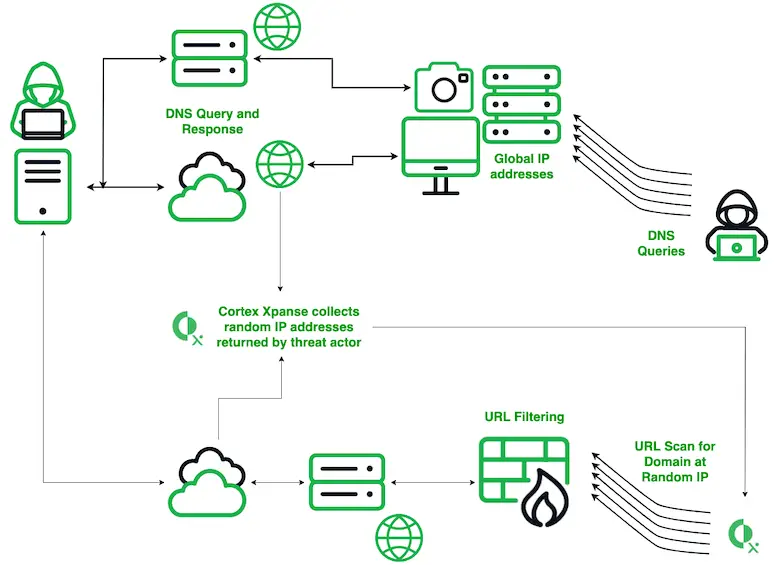
The consequences are far-reaching. Passive DNS collections are polluted, hindering threat research, and network resources are strained. Cortex Xpanse’s inability to filter wildcard DNS responses or recognize DNS malware exacerbates the problem.
Secshow and the amplification caused by Cortex Xpanse highlight the evolving challenges in cybersecurity. The incident emphasizes the need for transparency and cooperation within the security industry. It also calls for a reevaluation of security tools and practices to ensure they don’t inadvertently contribute to the problem they aim to solve.
As cyber threats become more sophisticated, proactive measures are crucial. Organizations must regularly assess their DNS configurations, patch vulnerabilities, and remain vigilant against potential threats. By understanding and mitigating the risks posed by operations like Secshow, we can better protect our digital infrastructure.