Secure Email Gateways Fail to Stop Advanced Phishing Campaign Targeting Multiple Industries

A detailed report from Group-IB reveals a sophisticated global phishing campaign targeting employees across 30 companies in 15 jurisdictions. By leveraging trusted domains and dynamic personalization, the threat actors have successfully exploited Secure Email Gateways (SEGs) and deceived victims across diverse industries, including finance, government, aerospace, and energy.
Group-IB’s investigation began in July 2024, uncovering a campaign characterized by advanced obfuscation techniques and multi-layered deception. The attackers distributed over 200 phishing links, embedding them within legitimate platforms like Adobe’s InDesign cloud service and Google AMP. This approach enabled them to evade detection mechanisms that typically block suspicious or unknown domains.
“Nine out of ten cyberattacks start with a phishing email, making it the most common entry point for threat actors,” the report states. These emails mimicked well-known brands, using familiar logos and professional formatting to build trust. For instance, phishing links impersonating DocuSign prompted victims to sign contracts, while links embedded in Adobe domains disguised fake login pages as critical documents.
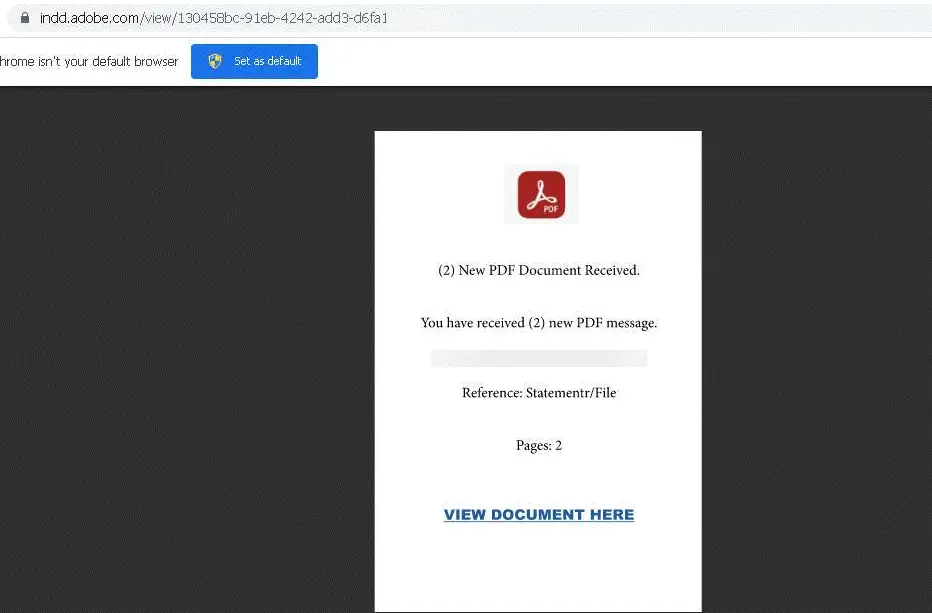
Example of a phishing link embedded in a file hosted on Adobe.com | Source: Group-IB
The campaign’s hallmark was its ability to dynamically personalize phishing pages. By extracting a victim’s email domain, the attackers tailored the visual elements of their phishing sites, including logos and page titles, to match the targeted organization. This method significantly increased the credibility of the phishing attempt.
“Scammers use a technique that dynamically pulls company logos from the official website to make the phishing links look legitimate,” the report notes. Using APIs like https://logo.clearbit.com/[company domain], the attackers seamlessly integrated accurate branding into their phishing pages, reducing suspicion and increasing user engagement.
To conceal their malicious intent, the attackers employed URL redirections via Google AMP and encoded parameters to create a complex trail. This multi-layered strategy not only bypassed SEGs but also complicated manual detection efforts.
For example, phishing URLs wrapped in Google redirection led victims to professionally crafted login pages pre-filled with their email addresses, further enhancing the illusion of legitimacy. Once credentials were entered, they were transmitted in real-time to the attackers’ Command-and-Control (C2) servers or Telegram bots via API endpoints.
The stolen data was exfiltrated to dedicated C2 servers or directly to Telegram bots. Group-IB identified JavaScript snippets within phishing sites that sent victim credentials to attacker-controlled endpoints. These scripts used techniques like Base64 encoding to obscure the exfiltration process and evade detection during static analysis.
“The JSON response from Telegram’s API confirms that the stolen credentials were successfully sent to a private chat controlled by the attacker,” Group-IB analysts observed. The credentials, formatted for easy parsing, provided attackers with immediate access to compromised accounts, enabling further exploitation.
Group-IB warns, “Threat actors are quickly adapting, constantly refining and improving their techniques to bypass security measures and exploit vulnerabilities.”
Related Posts:
- The Cobalt hacker group is still active, although the leader was arrested
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs
- India Post Customers Targeted in Massive Phishing Scam
- Beware: Hackers Use Google Drawings & WhatsApp Links to Steal Data
- The Escalating Threat of the EV Code Signing Certificate Black Market





