SecureFiware: Proposing security measures and security analysis in the Fiware IoT environment
SecureFiware
Overview
End-to-end encryption
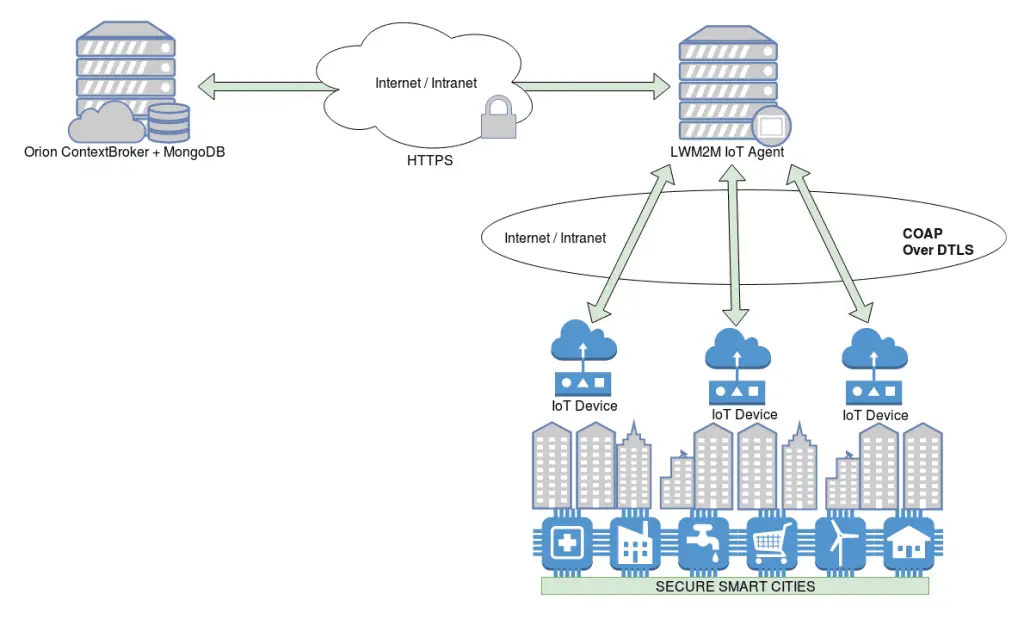
COAP Device to LWM2M IoT Agent encrypted communication
For the encrypted communication between the device and the IoT agent, we’ve embedded a DTLS server feature in the lwm2m-node-lib source code that forwards any request to the plain-text lwm2m udp server via localhost network then forwards the response back to the client. We designed this solution to be set up easily in the configuration .js file and is totally compatible with the lightweightm2m-iotagent as described here and also demonstrated on the PoC below. Notice that the other lightweightm2m-iotagent features are totally unaffected by this modifications. The dtls-proxy library was also developed by us and already have more than 300 downloads in the npm (search for node-dtls-proxy)
- Positive points:
- Enables DTLS communication between UDP servers and UDP clients (of any kind) with minimal or none source code modifications.
- Really quick to set up.
- Negative points:
- A bit slower than a Pure DTLS solution.
- The client requires dtls support or be able to run a software that implements the dtls proxy downgrade service.
- Links:
- goldy – IBM Lightweight DTLS proxy
- node-dtls-proxy
Orion ContextBroker and LWM2M IoT Agent HTTPS Communication and Support
For the HTTPS support on the Orion ContextBroker we’ve added a nginx container in the docker-compose.yml file that acts like an HTTPS reverse-proxy to the ContextBroker in HTTP context (SSL/TLS Termination), then we’ve modified the iotagent-node-lib used by the lightweightm2m-iotagent to support the ContextBroker in HTTPS context, the configuration can be set up in the .js configuration file of the IoTa described here, also we modified the IoT Agent with a new feature that starts the NGSI server in HTTPS context too. the configuration can be easily set up in the .js configuration file of the IoTA as described here just like the https Orion configuration.









