Security Alert: BianLian Deploys New PowerShell Weapon
Security researchers at GuidePoint have uncovered a new weapon in the BianLian ransomware gang’s arsenal – a PowerShell backdoor. This shift in tactics appears to be a direct response to the release of a BianLian decryptor by Avast in January 2023.
The new intrusion analyzed by Guidepoint’s DFIR team began with the exploitation of a vulnerable TeamCity server, likely using either CVE-2024-27198 or CVE-2023-42793. Once inside the network, the attackers employed a range of native Windows tools for discovery and lateral movement.
Several thwarted attempts to deploy their standard GO backdoor led the BianLian operators to pivot. They opted for a “living off the land” approach, creating a PowerShell backdoor to maintain their foothold.

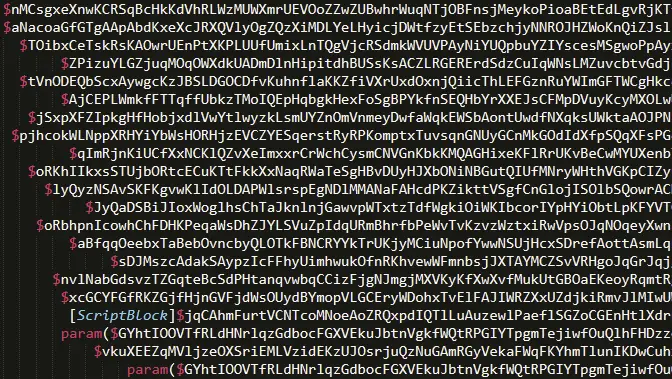
Obfuscated Second Stage PowerShell Script | Image: GuidePoint
The analysis revealed two pivotal functions within the PowerShell script: ‘cakes’ and ‘cookies’, the latter being instrumental in managing network connections and executing high-level commands. This script showcased advanced capabilities, including the use of Runspace Pools for asynchronous code execution and SSL streams for encrypted communications with the C2 server. These findings not only highlight the technical sophistication of BianLian’s latest toolkit but also its resemblance to the group’s GO backdoor, particularly in the use of certificates for authentication.
The attribution to BianLian was corroborated through several indicators, including shared infrastructure and AV detections. A noteworthy piece of evidence was the IP address associated with the C2 server, which linked back to the BianLian GO backdoor’s known activities. This web of connections, combined with the tactical evolution observed in the malware’s implementation, solidifies the DFIR team’s assessment of the PowerShell script as BianLian’s new avatar.
Inside the PowerShell Backdoor
- Under the Hood: The deobfuscated PowerShell script reveals a backdoor built for stealthy command execution. It establishes an encrypted communication channel with the C2 server, mimicking the functionality of the GO backdoor.
- Asynchronous Assault: Noteworthy is the use of Runspace Pools alongside the .NET PowerShell.Create() method. This combination facilitates asynchronous code execution within the encrypted channel, potentially making detection more challenging.
- Signature Fingerprints: The backdoor incorporates the same certificate validation techniques BianLian has used previously. This tactic allows researchers and security solutions to proactively identify connected infrastructure.
BianLian’s switch to a PowerShell backdoor is a stark reminder that adaptable adversaries demand dynamic security measures. Heightened awareness, focus on core cybersecurity principles, and integration of threat intelligence are paramount to outmaneuver these ever-changing threats.





