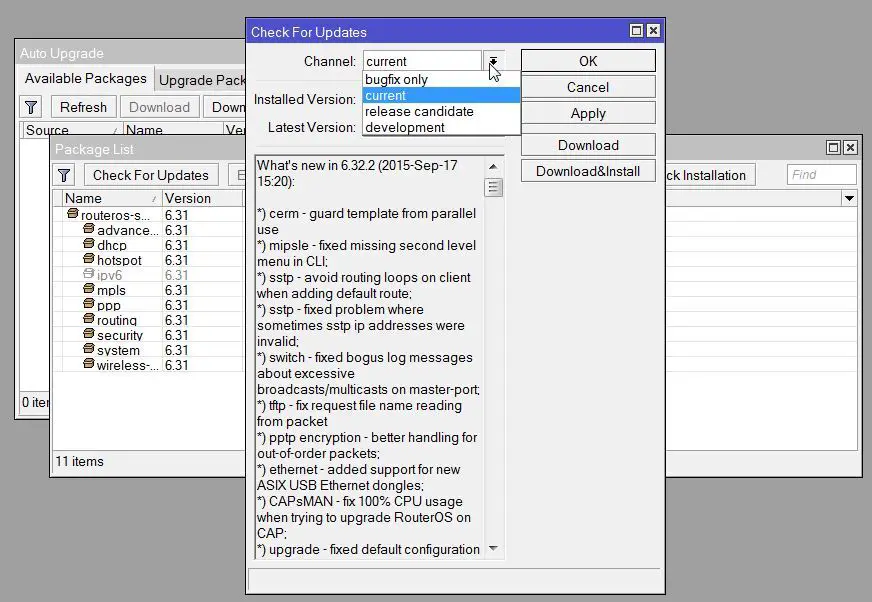
Security experts from security firm Core Security have disclosed details of a buffer overflow vulnerability that affected all architectures and all devices running prior to MikroTik RouterOS 6.41.3/6.42rc27.
MikroTik was founded in 1995 and is headquartered in Riga, Latvia. It is mainly engaged in the development of routers and wireless ISP systems. Its products are currently distributed all over the world. The RouterOS developed by the company is a routing operating system based on the Linux v3.3.5 kernel and can turn a standard PC into a professional router.
The vulnerability is tracked as CVE-2018-7445, and remote attackers who have access to the MikroTik RouterOS SMB service can exploit this vulnerability to execute arbitrary code on the system.
In its announcement, Core Security wrote: “A buffer overflow was found in the MikroTik RouterOS SMB service when processing NetBIOS session request messages. Remote attackers with access to the service can exploit this vulnerability and gain code execution on the system.”
At the same time, the announcement also released proof-of-concept code for use with MikroTik’s x86 Cloud Hosted Router (CHR).
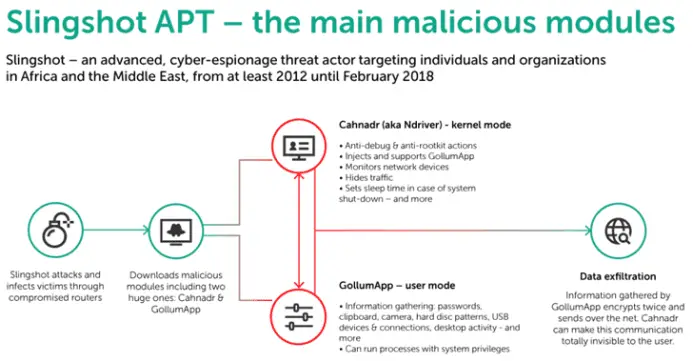
Just a few days ago, Kaspersky Lab’s security experts announced that they had discovered a new APT organization. The organization has been active since at least 2012 and used a malicious software called “Slingshot” to target computer users in the Middle East and African countries.

The infected computers are mainly distributed in Kenya, Yemen, Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia, and Tanzania. Kenya and Yemen became the most affected areas. Most of the victims were individuals, not businesses, as well as a few government organizations.
According to Kaspersky Lab’s security experts, the APT organization used the zero-day vulnerability in the Mikrotik router (CVE-2007-5633, CVE-2010-1592, and CVE-2009-0824) to spyware. The victim’s computer.
No one is currently able to determine whether the APT organization will also use CVE-2018-7445 loopholes to carry out attacks, but since the vulnerability has been discovered and the proof of concept code has also been announced, then all users need to use their own RouterOS is upgraded to version 6.41.3 to avoid potential attack risks. In addition, if users cannot install updates for some reason, we recommend that users can mitigate this problem by disabling the SMB service.
Source: securityaffairs