Security Joes Unveils Stealthy Windows Hijack Technique via WinSxS
In the ever-evolving landscape of cybersecurity, threat actors continuously seek new methods to compromise systems. A groundbreaking development in this field has been recently unveiled by the cybersecurity firm Security Joes. Their research has refined the classic DLL Search Order Hijacking technique, leveraging executables in the trusted WinSxS folder of the Windows operating system. This novel approach significantly enhances the efficacy and stealth of attacks, creating new challenges for cybersecurity defenses.
Before diving into the specifics of this new technique, it’s essential to understand the fundamentals of the WinSxS folder and DLL Search Order Hijacking. The WinSxS (Windows Side by Side) folder is a crucial component of the Windows OS, responsible for storing different versions of system files and DLLs to maintain system integrity and compatibility.
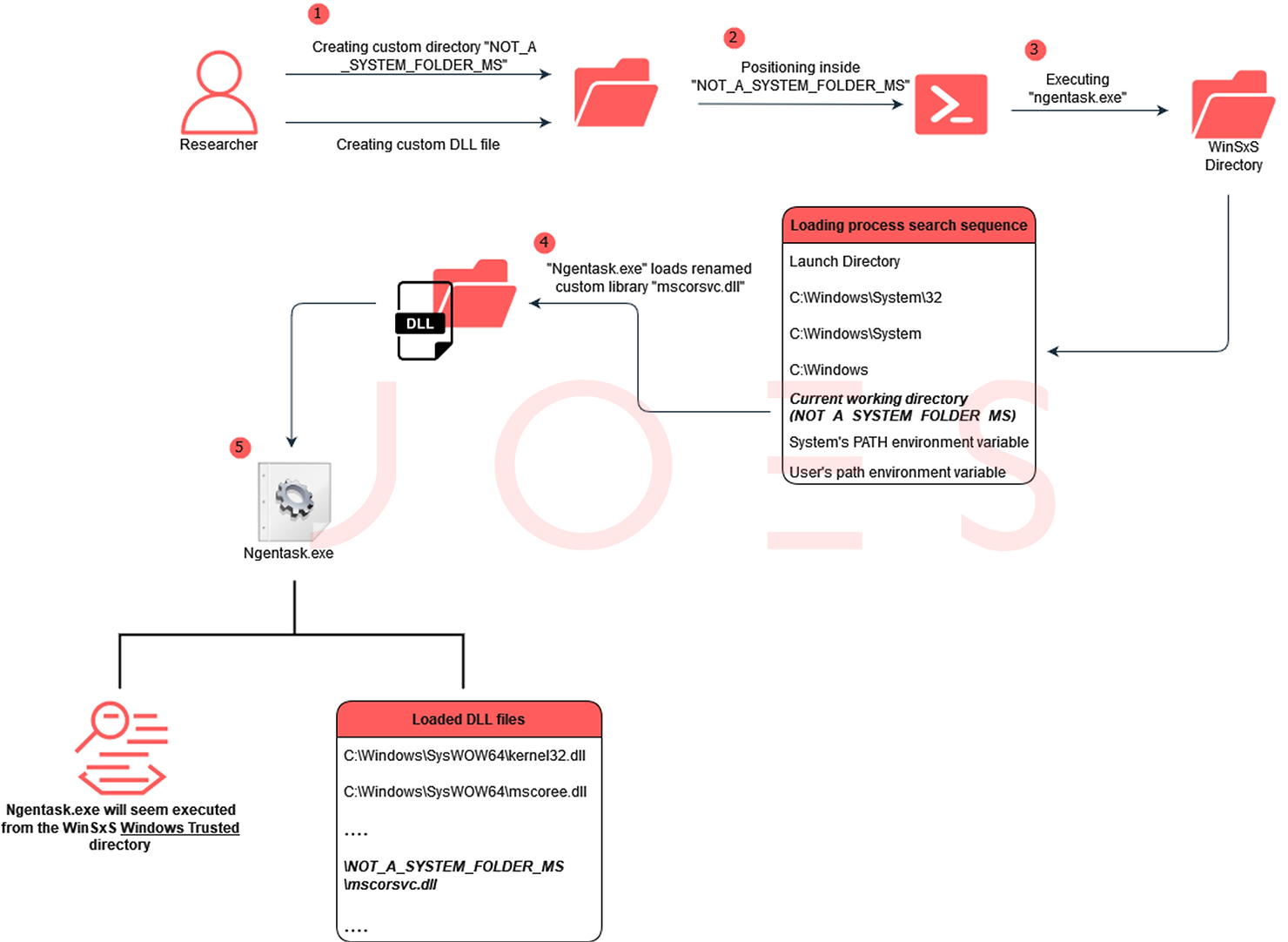
DLL Search Order Hijacking, meanwhile, is a well-known technique where threat actors exploit the way Windows applications load Dynamic Link Libraries (DLLs). By placing a malicious DLL in a directory that the system searches before the legitimate one, attackers can execute unauthorized code.

Execution flow of the DLL Search Order Hijacking targeting WinSxS applications | Image Credit: Security Joes
Security Joes’ approach innovates on this method by targeting binaries located in the WinSxS folder. This strategy has several advantages:
1. Circumvention of High Privilege Requirements: The technique eliminates the need for elevated privileges, as the malicious code is executed within applications in the WinSxS folder, which is inherently trusted by the system.
2. Elimination of Additional Binaries: This method does not require the introduction of additional, potentially detectable binaries. Windows already indexes the files in the WinSxS folder, which can be leveraged for the attack.
3. Enhanced Stealth: The malicious code operates within the memory space of a trusted application, reducing the likelihood of detection by security tools.
The exploitation process involves identifying a vulnerable binary in the WinSxS folder and comprehending the precise loading order Windows adheres to when searching for system files. The custom DLL is then strategically placed to be loaded by the targeted binary, replacing the legitimate DLL.
This new technique presents a significant challenge in cybersecurity, as it utilizes trusted components within the Windows environment, making detection more difficult. However, Security Joes offers strategies for addressing this exploitation method, focusing on parent process analysis and behavior analysis of binaries in the WinSxS folder.
The advancement of DLL Search Order Hijacking by targeting WinSxS binaries represents a significant shift in the cybersecurity landscape. It underscores the need for continuous vigilance and adaptation in security practices. As threat actors evolve their techniques, so must our defenses to protect against these sophisticated attacks.





