Security Onion 2.4.30 releases: Linux distro for intrusion detection, enterprise security monitoring, and log management

Security Onion
Security Onion is a free and open-source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
Below are several diagrams to represent the current architecture and deployment scenarios for Security Onion on the Elastic Stack.
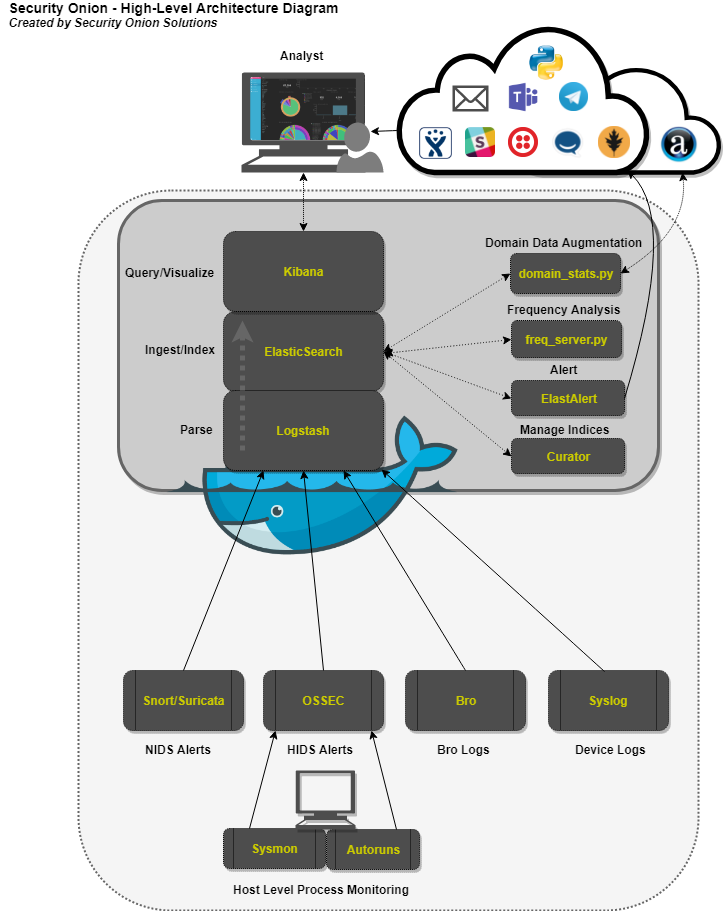
High-Level Architecture Diagram
Core Components
Logstash – Parse and format logs.
Elasticsearch – Ingest and index logs.
Kibana – Visualize ingested log data.
Auxiliary Components
Curator – Manage indices through scheduled maintenance.
ElastAlert – Query Elasticsearch and alert on user-defined anomalous behavior or other interesting bits of information.
FreqServer -Detect DGAs and find random file names, script names, process names, service names, workstation names, TLS certificate subjects and issuer subjects, etc.
DomainStats – Get additional info about a domain by providing additional context, such as creation time, age, reputation, etc.
Changelog v2.4.30
- FEATURE: Additional Supported Integrations #11513
- FEATURE: Allow for BPF comments in SOC #11738
- FEATURE: Dedicated Fleet node should have an nginx entry and cert that works for /artifacts
- FEATURE: OpenID Connect (OIDC) support
- FEATURE: so-elastic-fleet-reset #11697
- FEATURE: Sublime Platform Integration #11579
- FIX: Add the socore user to the Suricata container and adjust perms
- FIX: Add -watch to soctopus saltstate for file SOCtopus.conf. Makes container restart @ highstate if file is updated. #11700
- FIX: Allow ICMP to allow a node to respond to ping #11495
- FIX: Allow standalone install type to work with 16GB of ram #11699
- FIX: Allow the setting up of data_warm to the nodes list in ES
- FIX: Data not returned from mine for network.ip_addrs #11502
- FIX: Delete all obsolete scripts and unused code (also check so-setup, so-functions)
- FIX: Fail so-setup if Elastic Fleet Setup encounters an error #11696
- FIX: Global BPF prevents new sensor from applying highstate #11610
- FIX: Improve error handling of Elasticsearch pipeline and template load scripts #11728
- FIX: Logs not parsed correctly when shipped from Fleet Node #11698
- FIX: Only heavy nodes should be treated as remote Elastic clusters in SOC #11553
- FIX: Reduce ISO size #11510
- FIX: Set days for warm for all so-* indices
- FIX: Show container download status during soup #11550
- FIX: Sigma DNS mapping #11498
- FIX: Suricata 7 pkt_src field needs to be parsed #11566
- FIX: The values for specific nodes in zeek.config.local.load are being populated incorrectly #11472
- UPGRADE: NetworkMiner 2.8.1 #11457
- UPGRADE: Salt 3006.3 #11529
- UPGRADE: SOC dependency Axios to 1.6.1 #11763
- UPGRADE: Sophos Integration #11548
- UPGRADE: Upgrade Elastic to 8.10.4
- UPGRADE: Upgrade InfluxDB to 2.7.1 and Telegraf to 1.28.2
- UPGRADE: Upgrade Suricata to 7.0.2
- UPGRADE: Zeek 6.0.2