Security Researcher found autofill vulnerability in browsers
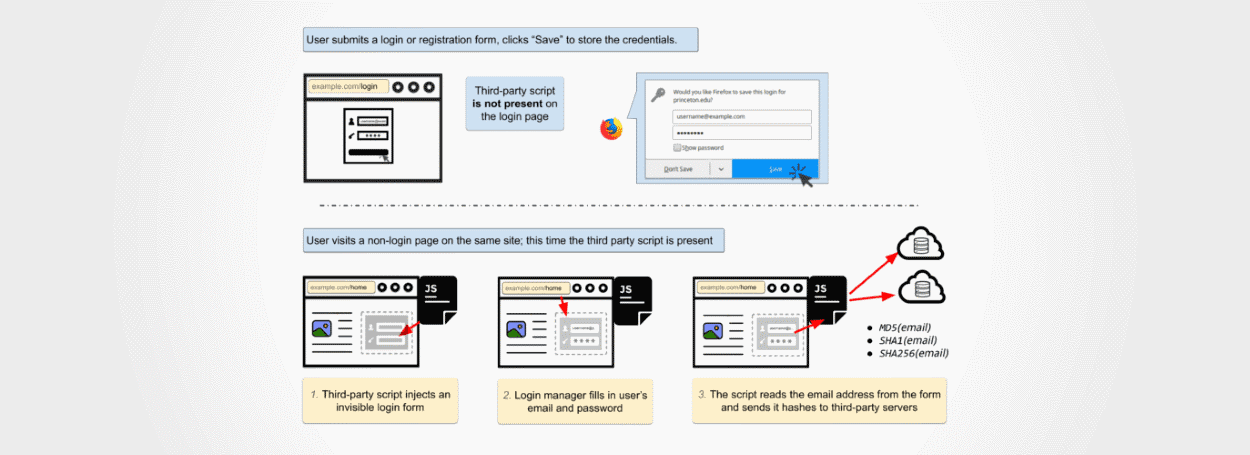
According to foreign media reports on December 27, Princeton Center for Information Technology Policy (CITP) has discovered the latest use of browser “auto-fill” vulnerability to steal user information. Currently, there is a design flaw in the login manager of all browsers – the login manager allows the browser to remember the user’s username and password on each particular website and automatically insert it when the user revisits the website To login form. It is because of the way Login Manager works that network trackers can embed hidden login forms on websites that load trace scripts to steal user information.
Princeton privacy experts warned that advertising and analytics companies exploit the login manager’s vulnerability to set up hidden login fields to secretly extract usernames from websites and bind unauthenticated users’ profiles or emails to the site. Security breaches have been described by security privacy experts for more than a decade, collecting user information only during an XSS (cross-site scripting) attack. However, the current malicious person has designed a new attack.
It is reported that Princeton researchers recently found two kinds of network tracking service using a hidden login form to collect login information: Adthink (audienceinsights.net), OnAudience (behavioralengine.com). The two tracking services use their scripts to gather login information for 1110 websites found on the Alexa Top 1 Million websites list. The current login information only contains the user name or email address, and does not involve important password information.
Given this situation, ad agencies and analytics companies create a hash from the stolen username / email and bind that hash to the site’s existing ad profile. The researchers introduced that the hash of the email address is a good tracking identifier. Because e-mail addresses are unique, persistent, and the user’s e-mail address hardly changes, clearing cookies, using private browsing mode, or switching devices does not prevent tracking. Web-based trackers can use hashes of email addresses to connect to online profiles scattered across different browsers, devices and mobile apps. In addition, the hash can also be used as a cookie to clear the link between browsing history profiles before and after.
Informed sources, in addition to the Brave browser, other major browsers seem to be vulnerable to this type of attack, for example, Chromium-based browser to disclose the user’s password when the user clicks the page. Researchers have now proposed a workaround: Manufacturers set their browsers to automatically populate only when users interact with fields that actually need to be logged in.
According to Princeton, secretly collecting user data is not limited to violating the privacy of individual users, but may actually violate the EU’s forthcoming GDPR rules, even though some website owners are not aware that their actions are tracked.
Related Reading
The demo page provided by the Princeton Center for Information Technology Policy (CITP)
Source: BleepingComputer





