Image: Malwarebytes
Cybercriminals are increasingly targeting online marketing and advertising tools to leverage them in their malicious campaigns. A recent report by Malwarebytes details a new operation targeting Semrush, a popular visibility management SaaS platform.
Semrush is a highly attractive target for online criminals. With 40% of Fortune 500 companies and 117,000 paying customers relying on Semrush, the platform’s popularity makes it a prime target for malicious actors.
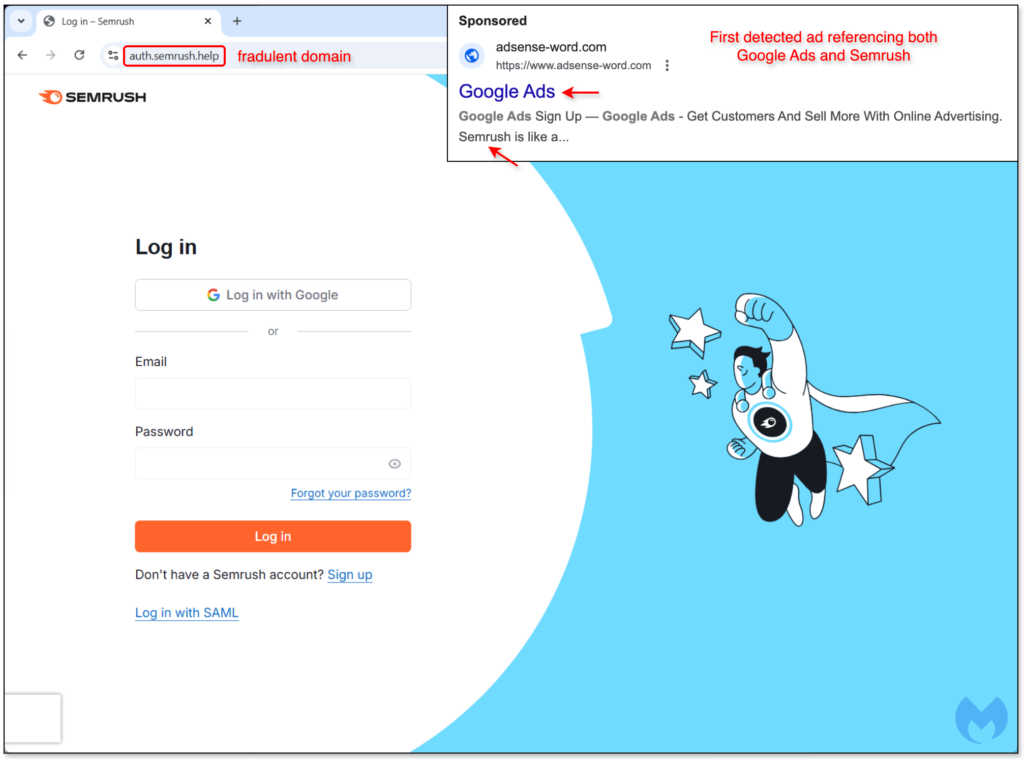
The fraudsters are taking an indirect approach to potentially hacking Google advertisers and gaining access to Semrush accounts. Malwarebytes’ investigations uncovered a campaign where malicious ads impersonated Semrush.
Malwarebytes previously documented a large phishing campaign targeting Google accounts via Google Ads using a specific technique that abused Google Sites. The criminals behind this campaign have now switched to a less direct approach. This transition was observed with a malicious ad for “Google Ads” that redirected to a fraudulent login page for Semrush.
The campaign quickly evolved to fully impersonate Semrush. The infrastructure for this new wave was recently deployed, and the domain names registered for it are all variations on the Semrush name.
Examples of malicious ads include:
- semrush.tech
- semrush-pro.click
- ads-semrush.com
- semrush.works
- semrush-pro.co
Each ad uses a unique domain name, which redirects to more static domains dedicated to the fake Semrush and Google account login pages.
The fraudulent Semrush login pages primarily focus on harvesting Google accounts. While the phishing page uses the Semrush brand, only the “Log in with Google” option is enabled, forcing victims to authenticate with their Google account username and password.
This is further confirmed by the malicious sign-in page for Google, which sends those credentials to the criminals. It’s important to note that victims who arrive at these pages are likely Semrush users, given the path they took to get there.
Compromised Google accounts can lead to the theft of Google Analytics (GA) and Google Search Console (GSC) data. These platforms contain critical and confidential information for businesses, including website performance, user behavior, and strategic business focuses.
For example, e-commerce tracking in GA shows revenue, transaction volumes, average order values, and conversion rates by channel. In GSC, malicious actors could see historical data for the past 16 months, including search queries, pages, countries, devices, search appearance, and dates.
Google Analytics and Google Search Console data is often integrated with tools like Semrush for enhanced analysis. Semrush requests validation from a Google account to allow Semrush to see and download GA and GSC data.
This integration allows for the export of behavioral data and KPIs coming directly from Google Search Console (GSC) without direct access to the Google account.
There is additional information stored in a Semrush account that a threat actor could leverage to impersonate an individual or business. This includes name, phone, business name, address, email, and the last 4 digits of a Visa card.
This information could be used to deceive vendors or partners into sending payments to fraudulent accounts, exploiting the trust tied to the business’s identity. Someone posing as Semrush support could also use this information to trick victims into providing full credit card details.