sentinel-attack
Sentinel ATT&CK aims to simplify the rapid deployment of a threat hunting capability that leverages Sysmon and MITRE ATT&CK on Azure Sentinel.
DISCLAIMER: This tool is not a magic bullet. It will require tuning and real investigative work to be truly effective in your environment.
Overview
Sentinel ATT&CK provides the following tools:
- An ARM template to automatically deploy Sentinel ATT&CK to your Azure environment
- A Sysmon configuration file compatible with Azure Sentinel and mapped to specific ATT&CK techniques
- A Sysmon log parser mapped against the OSSEM data model
- 117 ready-to-use Kusto detection rules covering 156 ATT&CK techniques
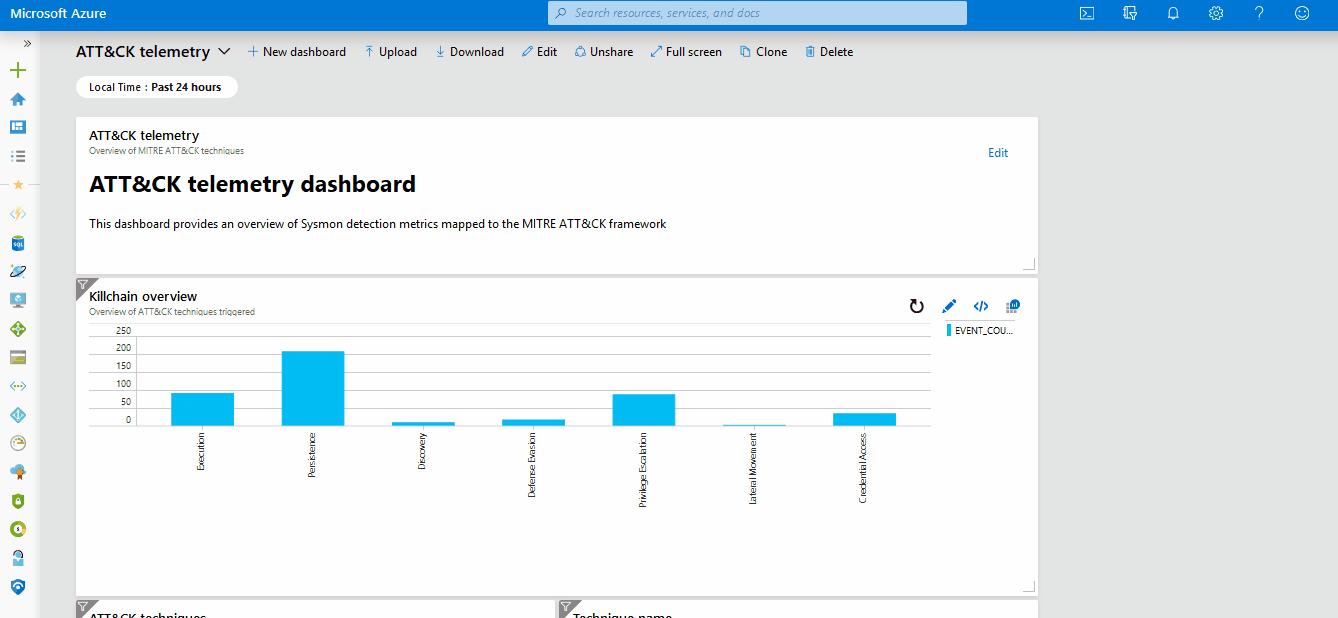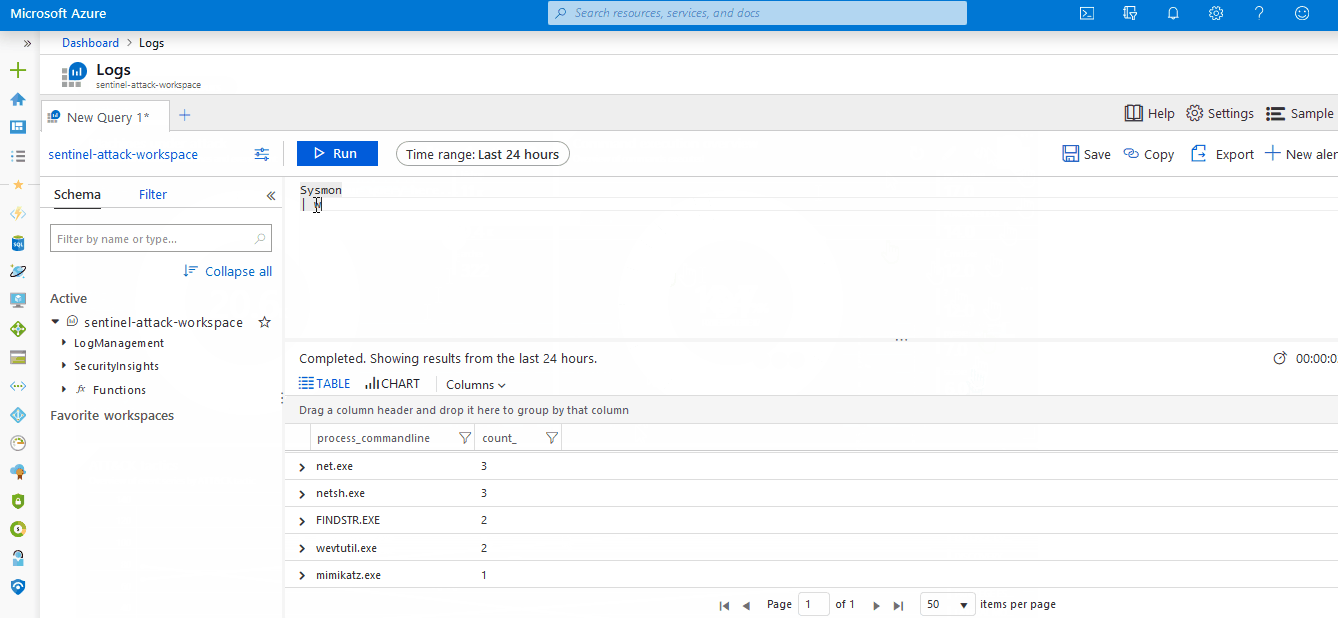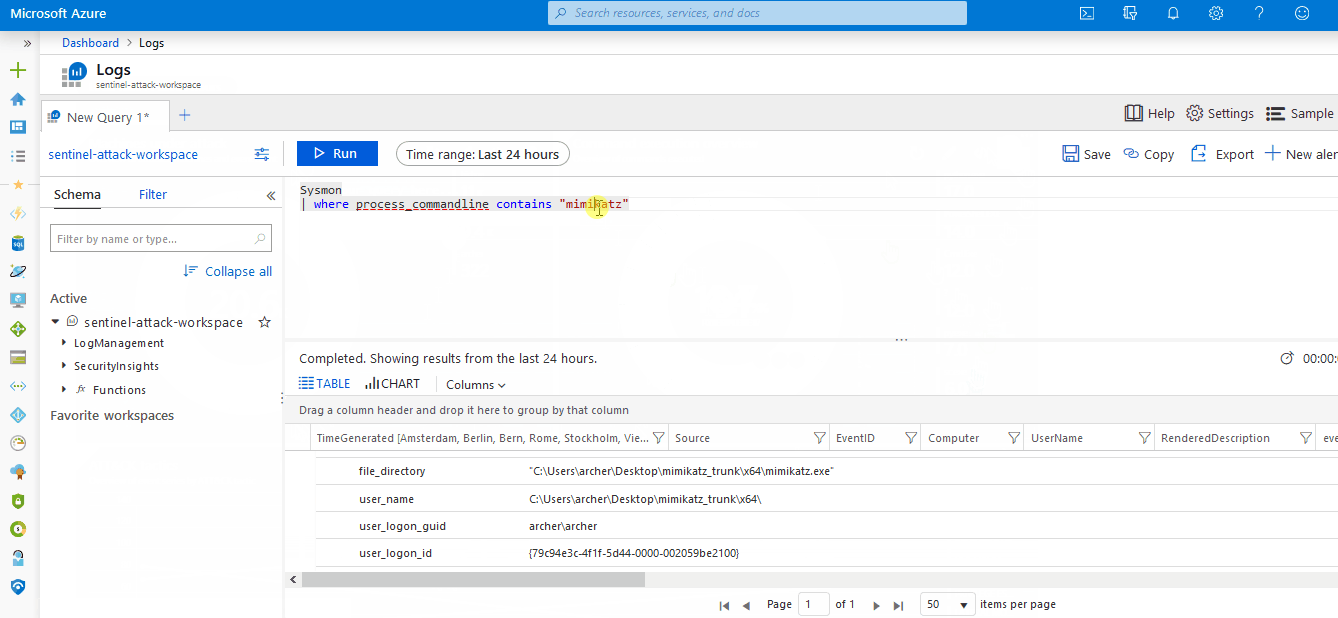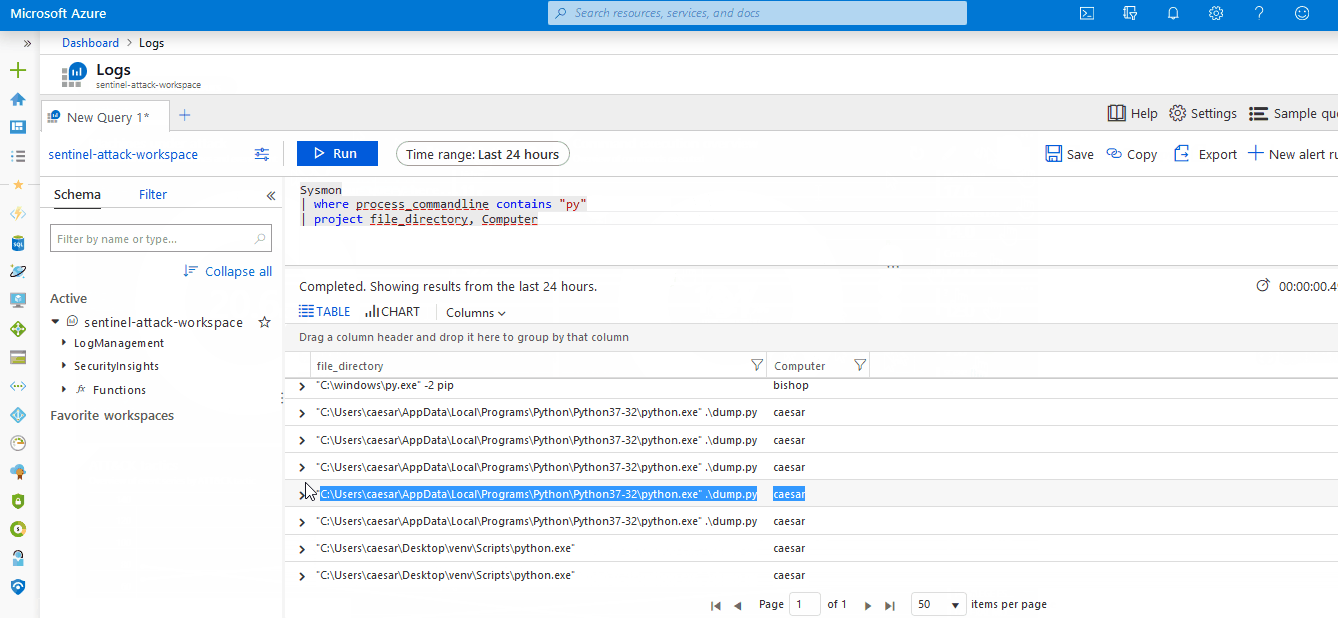
- A Sysmon threat hunting workbook inspired by the Threat Hunting App for Splunk to help simplify threat hunts
- A Terraform script to provision a lab to test Sentinel ATT&CK
- Comprehensive guidance to help you use the materials in this repository
Changelog v1.4.3
Changed
- Upgraded lab deployment script to use the latest version (v2.40) of azurerm provider plugin
- Improved stability and maintainability of the lab deployment script
- Improved management of sensitive information within the terraform .tfvars file
- Standardised naming of lab resources
- Updated Sentinel ATT&CK test lab documentation page
Fixed
- Miscellaneous fixes and improvements to make the script compatible with terraform v0.14.5
- Bug in the lab deployment script that prevented the Win10 machine from joining the domain
- Eliminated all deprecation warnings
- Confusing variable naming conventions within the terraform .tfvars file
Removed
- Automatic deployment of sentinel-attack whitelisting files
Download & Use
Copyright (c) 2019 Edoardo Gerosa, Olaf Hartong