
Resecurity has uncovered a widespread campaign exploiting critical vulnerabilities in ServiceNow, a popular platform for digital workflows. The flaws, identified as CVE-2024-4879, CVE-2024-5217, and CVE-2024-5178, allowed unauthenticated attackers to execute code remotely and steal sensitive data.
The widespread use of ServiceNow, particularly within major corporations and government entities, has made it a prime target for threat actors. Resecurity’s investigation uncovered a rapid surge in malicious activity immediately following the public release of a proof-of-concept exploit. Attackers, armed with this knowledge, wasted no time in scanning the internet for vulnerable instances, primarily leveraging CVE-2024-4879 to execute code remotely and exfiltrate sensitive data.
Estimating the impact is challenging, but ServiceNow is an extremely popular platform for managing digital workflows in modern IT environments. According to the output of FOFA, a popular network search engine from China, approximately 300,000 ServiceNow instances could be potentially probed remotely. These instances may have different ACL (Access Control Lists) or other access limitations at both the network and application levels, making this only an approximate estimation.
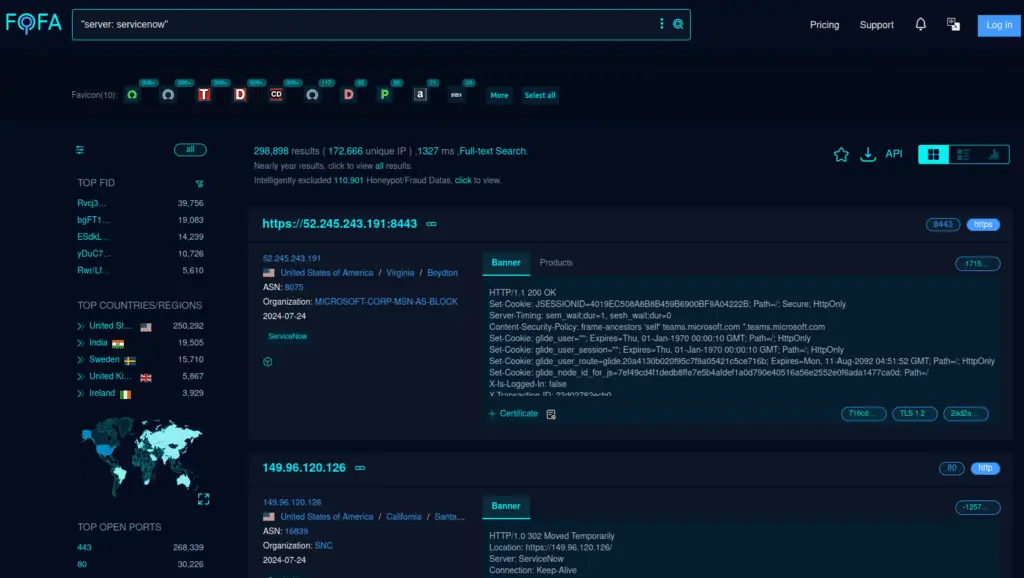
The largest number of vulnerable instances have been identified in the United States, the United Kingdom, India, and the European Union. Other search engines frequently used by adversaries for network mapping and quick identification of potentially vulnerable hosts also showed a significant number of hits, ranging from 13,300 to 23,000 network hosts.
The actual number of vulnerable hosts may vary, but adversaries have a considerable window of opportunity to exploit these vulnerabilities before patches are applied, targeting major enterprises.
The stolen data, including user lists, hashed passwords, and even plaintext credentials in some cases, could be used for cyber espionage, further targeted attacks, or even sold on the dark web. While the complexity of ServiceNow’s hashing algorithm may have prevented the immediate cracking of most passwords, the exposed user lists offer valuable reconnaissance information for threat actors to exploit in future campaigns.
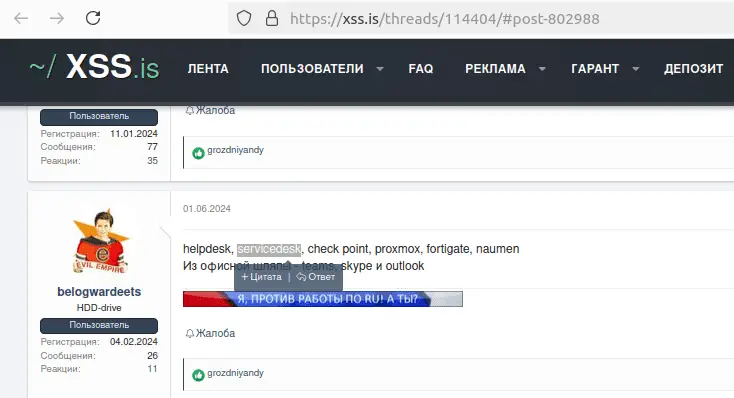
This campaign’s broad geographic reach, spanning the United States, the United Kingdom, India, the European Union, and the Middle East, underscores the global nature of the threat. Industries affected range from energy and data centers to government agencies and software development firms. The compromised data could have severe implications for affected organizations, leading to data breaches, operational disruptions, and financial losses.
ServiceNow has promptly released patches and hotfixes [1,2,3] to address these vulnerabilities. However, the window of opportunity for attackers remains open as organizations do not update their systems. The urgency is compounded by the potential for compromised ServiceNow instances to appear on the dark web, further fueling the threat landscape.
Organizations are strongly advised to prioritize the immediate application of all available security updates, monitor their network traffic for any signs of unusual activity, and bolster their security posture with robust measures like multi-factor authentication and intrusion detection systems.
Related Posts:
- ServiceNow’s ‘Simple List’: The Vulnerability Jeopardizing Thousands of Companies
- ServiceNow Security Alert: Critical Vulnerabilities Expose Businesses to RCE and Data Breaches
- US/UK warn Russia to hack into global routers