sessionless: Burp Suite extension for editing, signing, verifying various signed web tokens
Sessionless
Sessionless is a Burp Suite extension for editing, signing, verifying, and attacking signed tokens: Django TimestampSigner, ItsDangerous Signer, Express cookie-session middleware, OAuth2 Proxy, and Tornado’s signed cookies.
It provides automatic detection and in-line editing of tokens within HTTP requests/responses and WebSocket messages, signing of tokens, and automation of brute force attacks against signed tokens implementations.
Wordlist View
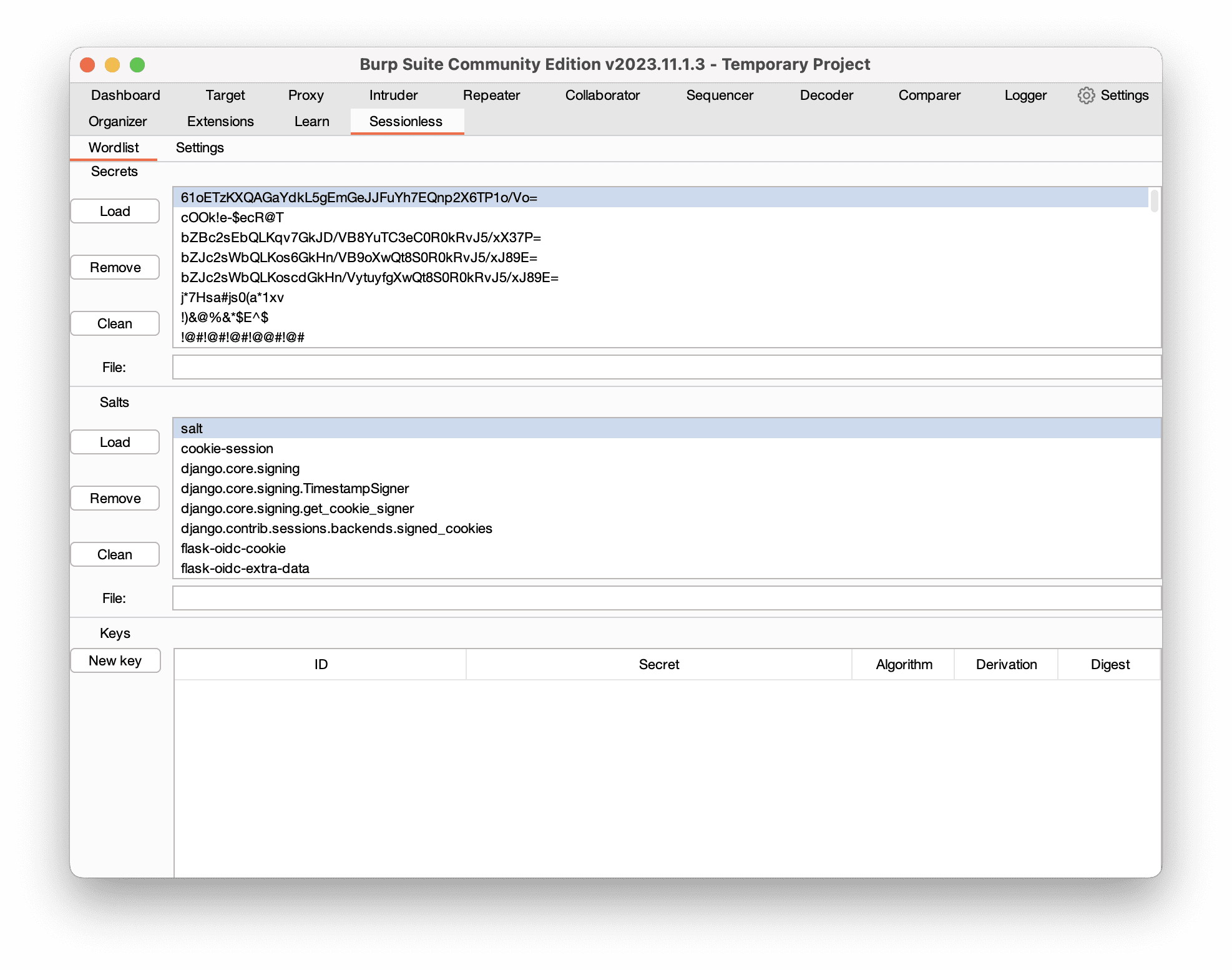
The Wordlist View allows to import of secrets and salts list files. Extension has its prebuilt dictionary lists. Most secrets are taken from jwt-secrets. As an option, Flask-Unsign-Wordlist can be used. The extension supports JSON strings format for special chars, to use it quot the secret string with ".
Editor View
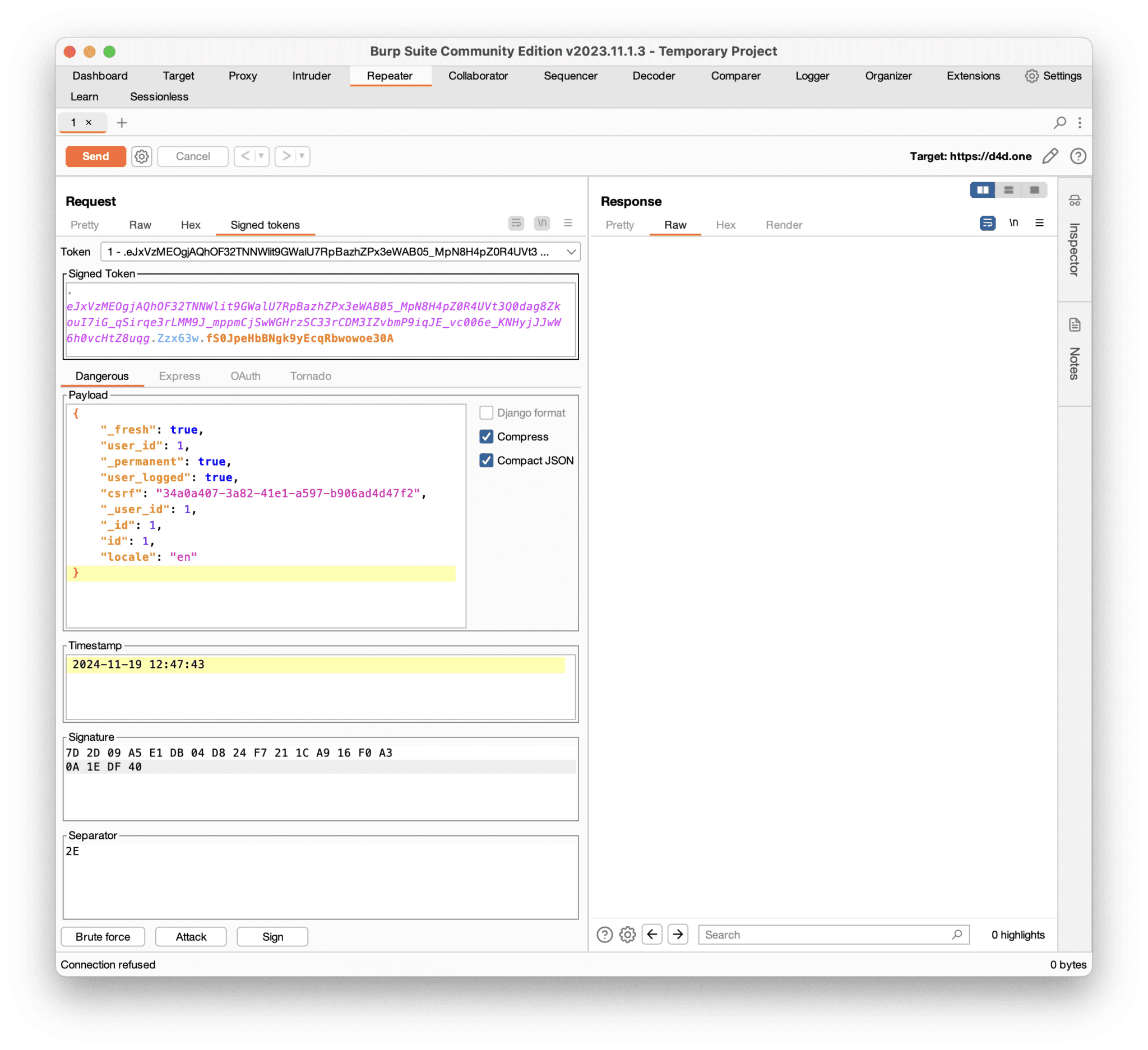
The Editor View supports a number of signed tokens: Django, Dangerous, Flask, Express, OAuth2 and Tornado. It allows modification of the signed tokens at Burp Suite’s HTTP Request/Response view in the Proxy, History and Repeater tools.
The Dangerous tab can be used for both, Flask and Django tokens, which are selected depending on whether a Dangerous or Django token is detected.
Editable Fields
A JSON text editor is provided to edit each component that contain JSON content:
- Dangerous Payload
- Django Payload (except pickle serialized payload)
- Express Payload
A timestamp editor is provided to edit each component that contain it:
- Dangerous timestamp
- Django timestamp
- OAuth2 Proxy timestamp
- Tornado timestamp
A hex editor is provided to all signed tokens, except Express signatures. NOTE Express Tab doesn’t support signature auto update yet. Please copy it manually to corresponding signature cookie.
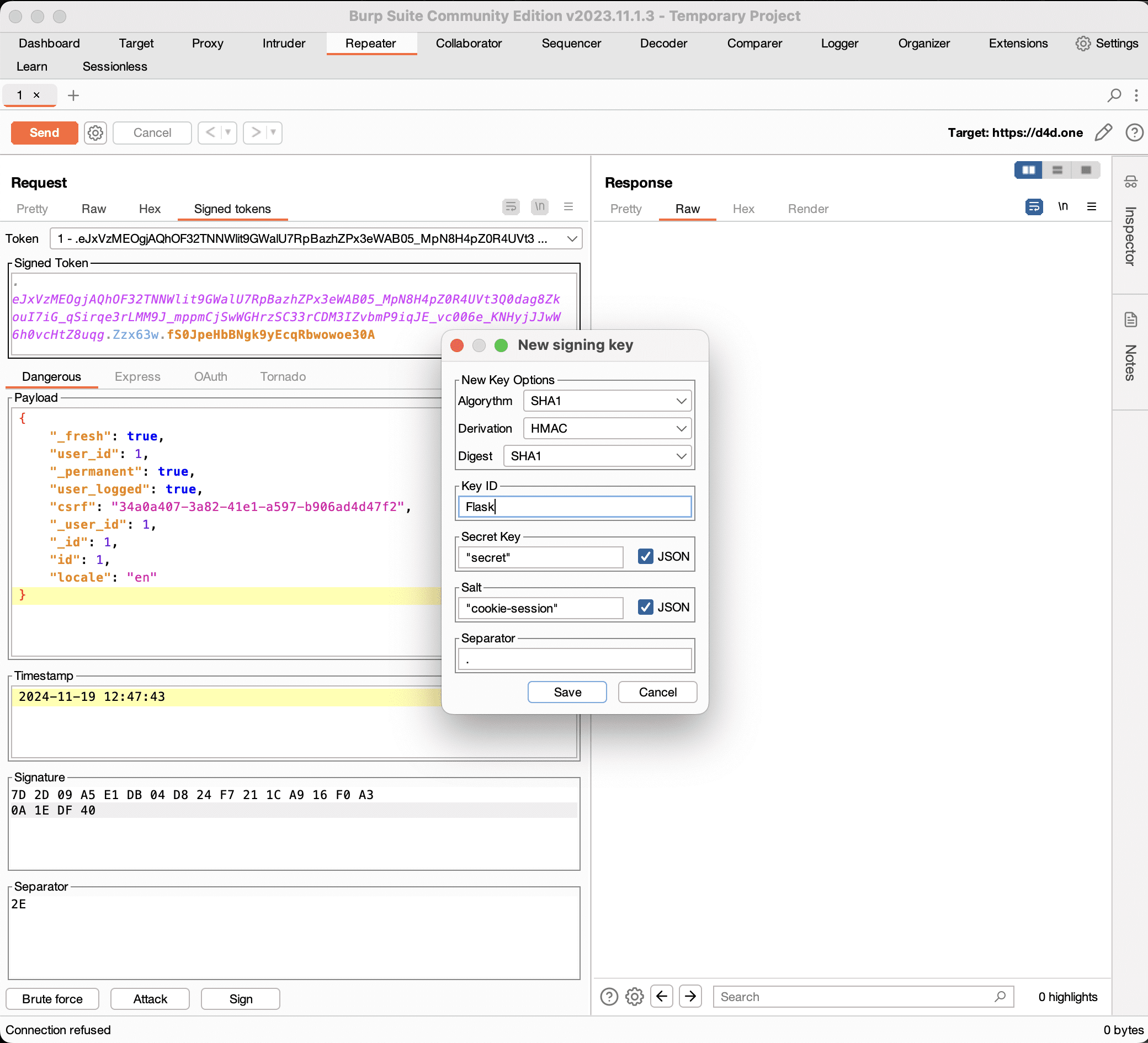
Sign
Sign presents a signing dialog that can be used to update the Signature by signing the token using a key from the Keys View that has signing capabilities
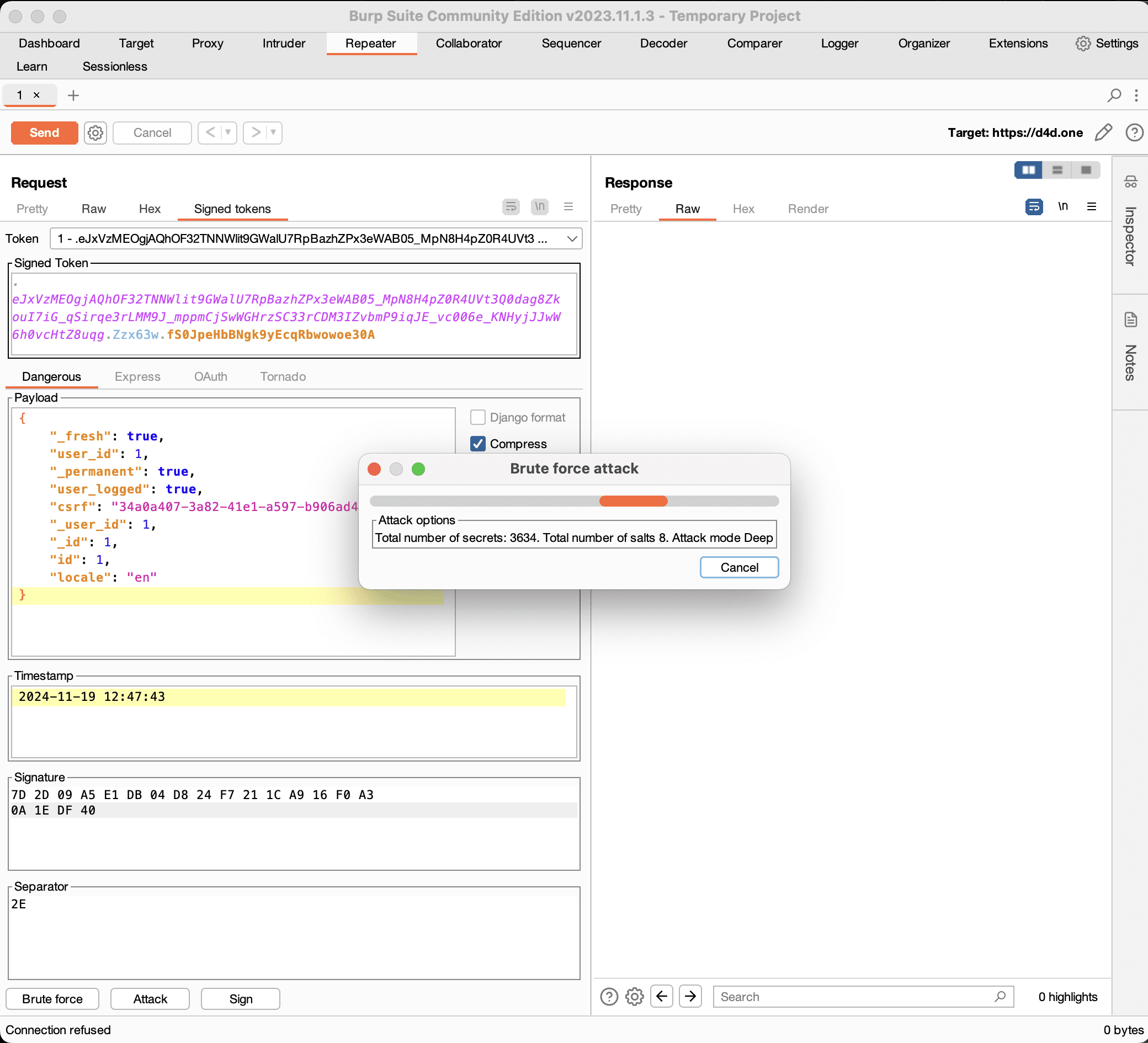
Brute force
Brute force will attempt to find secret key that was used for signature generation. If a secret key was found, a dialog will be presented.

The Brute force option implements three types of attacks against signed tokens Signatures:
- Fast will use default hashing algorithm and key derivation
- Balanced will use all known key derivation technics, except PBKDF2HMAC
- Deep will use all key derivation technics, including PBKDF2HMAC
Attack

The Attack option implements eight well-known authorization attacks against signed tokens:
- User claims
- Wrapped user claims
- Username and password claims
- Flask claims
- Express claims
- Account user claims
- Authenticated claims
- User access_token
These are described in more detail below.
Attacks
All of these attacks can be used together. Please bear in mind that extension doesn’t support token payload modification at Attack mod, so your payload will be replaced with new one.
User claims
OpenID connect ID token format usually used by signing libraries to store information about authenticated user. Extension will generate placeholder for admin user ID token.
Wrapped user claims
Same as User claims attack but will put it into user JSON attribute.
Username and password claims
Another common way to store user details is username and password JSON attributes. Extension will generate placeholder for admin user.
Flask claims
Flask authenticated user session information if stored at client side should include id and _id and user_id or _user_id JSON attribute. Extension will generate session for the first user, usually admin.
Express claims
Express framework uses passport JSON attribute to store user details. Extension will generate placeholder for admin user.
Account user claims
Some frameworks may use account wrapper to store information about authenticated user. For exploitation, it might be required to use Authenticated claims too.
Authenticated claims
The Authenticated claims implements 12 well-known authorization flags.
User access_token
The User access_token option generated JWT OpenID connect ID token signed with the same key and same hashing algorithm without any key derivation performed.
Install
Copyright 2023, d4d




