sg1: swiss army knife for data encryption, exfiltration & covert communication

SG1 is a wanna be swiss army knife for data encryption, exfiltration, and covert communication. In its core sg1 aims to be as simple to use as nc while maintaining high modularity internally, being a framework for bizarre exfiltration, data manipulation and transfer methods.
Features
The main sg1 operation logic is:
Keep in mind that modules and channels can be piped one to another, just use sg1 -h to see a list of available channels and modules, try to pipe them and see what happens ^_^
Modules
Modules can be combined, for instance, if you want to read from input, decrypt from AES and execute, you would use:
-in:... -modules aes,exec -aes-mode decrypt -aes-key _somekeysomekey_ -out:...
raw
The default mode, will read from an input and write to output.
base64
Will read from input, encode in base64 and write to output.
aes
Will read from input, encrypt or decrypt (depending on –aes-mode parameter, which is encrypt by default) wih –aes-key and write to output.
Examples:
-modules aes --aes-key y0urp4ssw0rd -modules aes -aes-modules decrypt --aes-key y0urp4ssw0rd
exec
Will read from input, execute as a shell command and pipe to output.
Channels
console
The default channel, stdin or stdout depending on the direction.
tcp
A tcp server (if used as input) or client (as output).
Examples:
-in tcp:0.0.0.0:10000 -out tcp:192.168.1.2:10000
udp
An udp packet listener (if used as input) or client (as output).
Examples:
-in udp:0.0.0.0:10000 -out udp:192.168.1.2:10000
tls
A tls tcp server (if used as input) or client (as output), it will automatically generate the key pair or load them via –tls-pem and –tls-key optional parameters.
Examples:
icmp
If used as output, data will be chunked and sent as ICMP echo packets, as input an ICMP listener will be started decoding those packets.
Examples:
dns
If used as output, data will be chunked and sent as DNS requests, as input a DNS server will be started decoding those requests. The accepted syntaxes are:
dns:domain.tld@resolver:port
In which case, DNS requests will be performed (or decoded) for subdomains of domain.tld, sent to the resolver ip address onport.
dns:domain.tld
DNS requests will be performed (or decoded) for subdomains of domain.tld using default system resolver.
dns
DNS requests will be performed (or decode) for subdomains of google.com using default system resolver.
Examples:
pastebin
If used as output, data will be chunked and sent to pastebin.com as private pastes, as input a Pastebin listener will be started decoding those pastes.
Examples:
This is how you can retrieve your user key given your api key.
Installation
Usage
Simple file exfiltration over DNS:
Quick and dirty AES encrypted chat over TCP:
Encrypting data in AES and exfiltrate it via DNS requests:
Test with different operating systems ( tnx to decoded ): 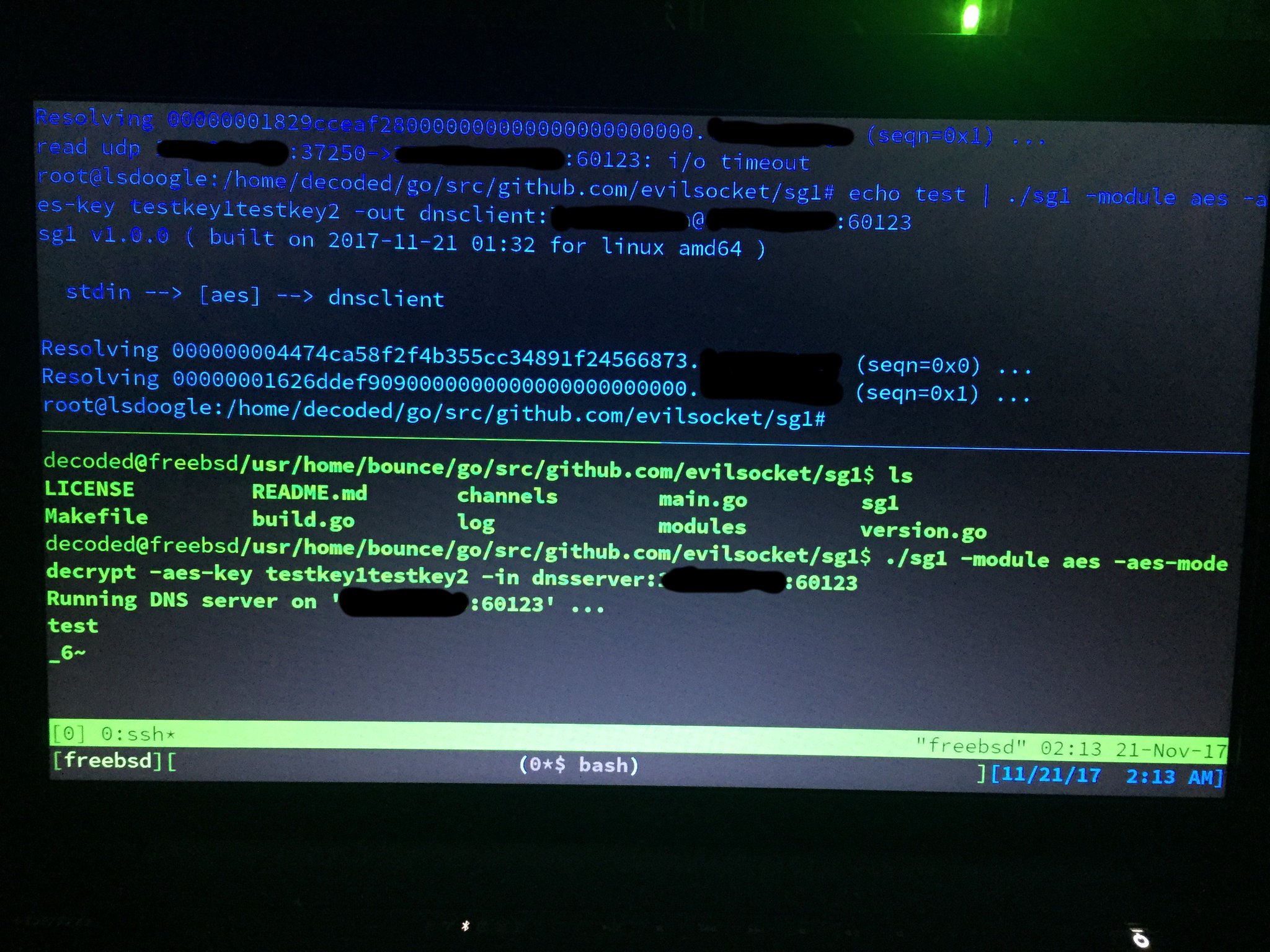
With bouncing to another host:
Just use sg1 -h to see a list of available channels and modules, try to pipe them and see what happens, you can also transfer files and make requests “bounce” to several machines with random AES keys ^_^
Copyright (C) 2017 evilsocket
Source: https://github.com/evilsocket





